Captive Portal Authentication¶
Our proxy will utilize Azure Active Directory authentication with the help of Captive Portal. The idea is simple - if a connecting user is not known for the proxy, the proxy redirects the user to authentication page of Azure Active Directory.
After credentials are verified correctly, Azure Active Directory tells the proxy which user name should be used for the connection. The proxy will then select the appropriate web filtering policy, apply filtering algorithms, save the information about the user in the traffic monitor and reporting modules.
Provision Captive Portal App¶
In order to the proxy to be able to redirect users to Azure Active Directory we need to register the proxy Captive Portal application in the Azure Active Directory. So, login into your Azure portal and click Azure Active Directory on the left dark menu and then select the App Registrations menu item.
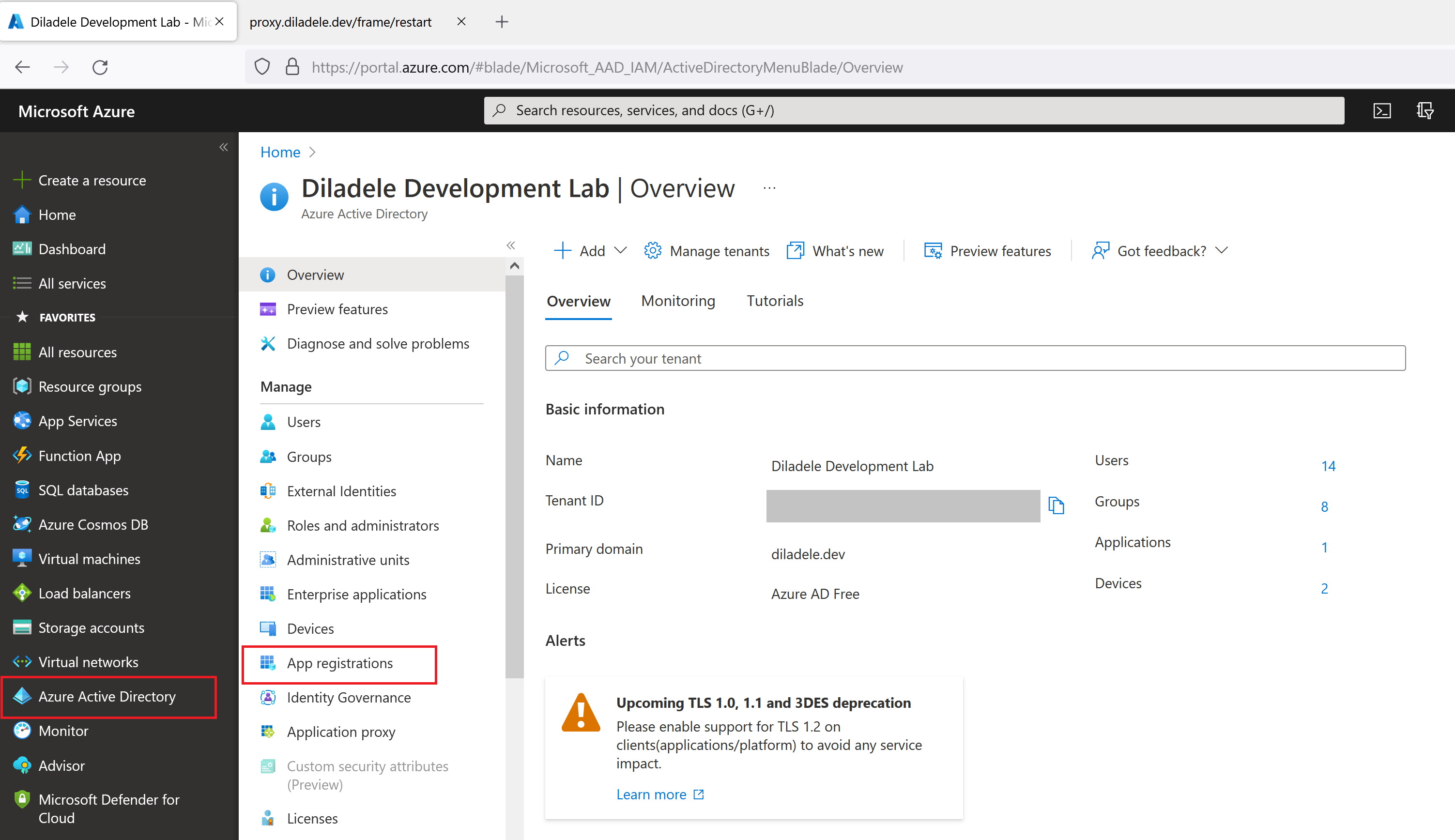
Choose New Registration from the top as shown on the following screenshot.
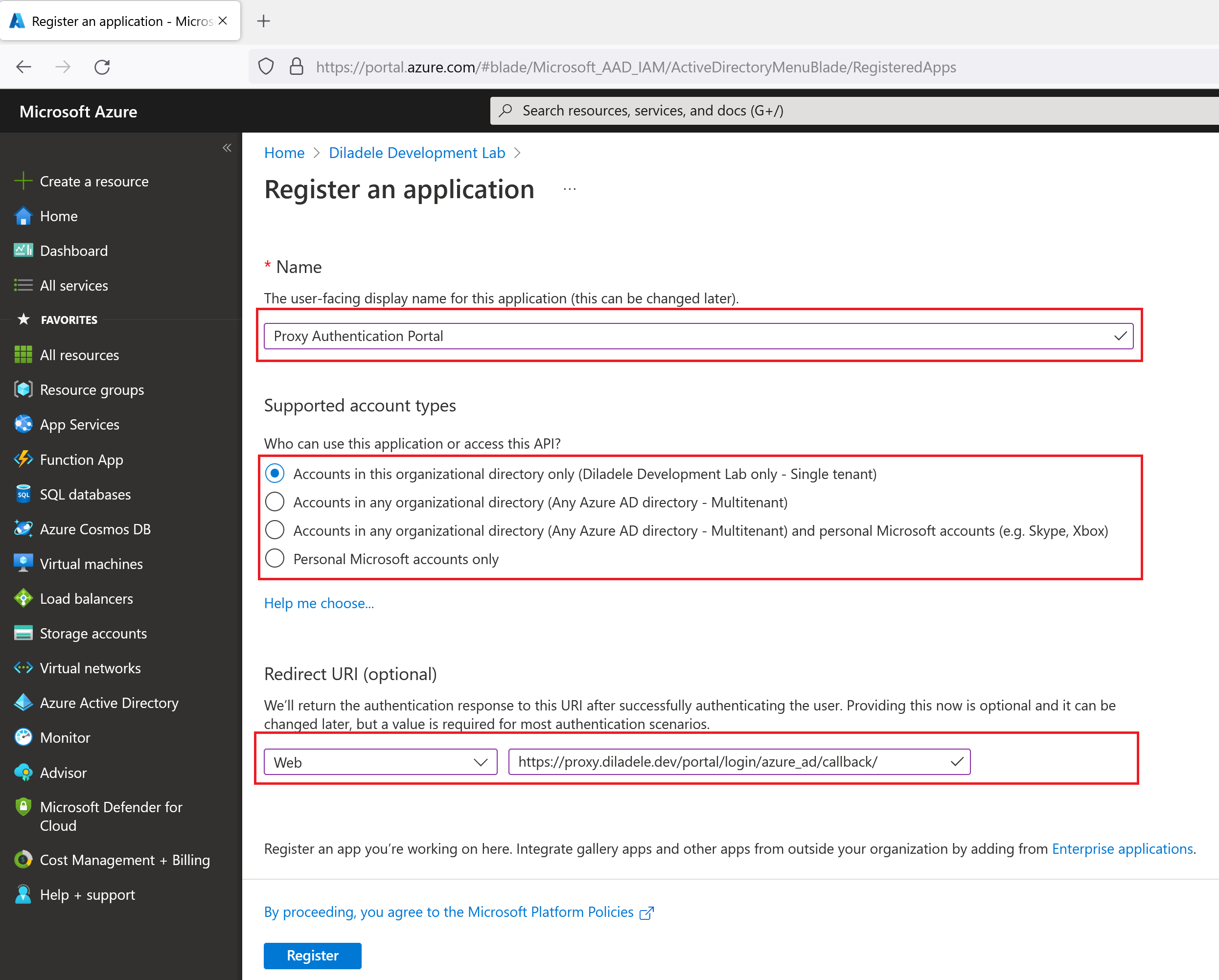
Follow the steps on the wizard providing the following information and click the Register button. Be sure to change the name of proxy.diladele.dev to your actual proxy name of course.
Display Name |
Proxy Authentication Portal |
Account types |
Single Tenant |
Redirect URI |
Select Web, https://proxy.diladele.dev/portal/login/azure_ad/callback/ |
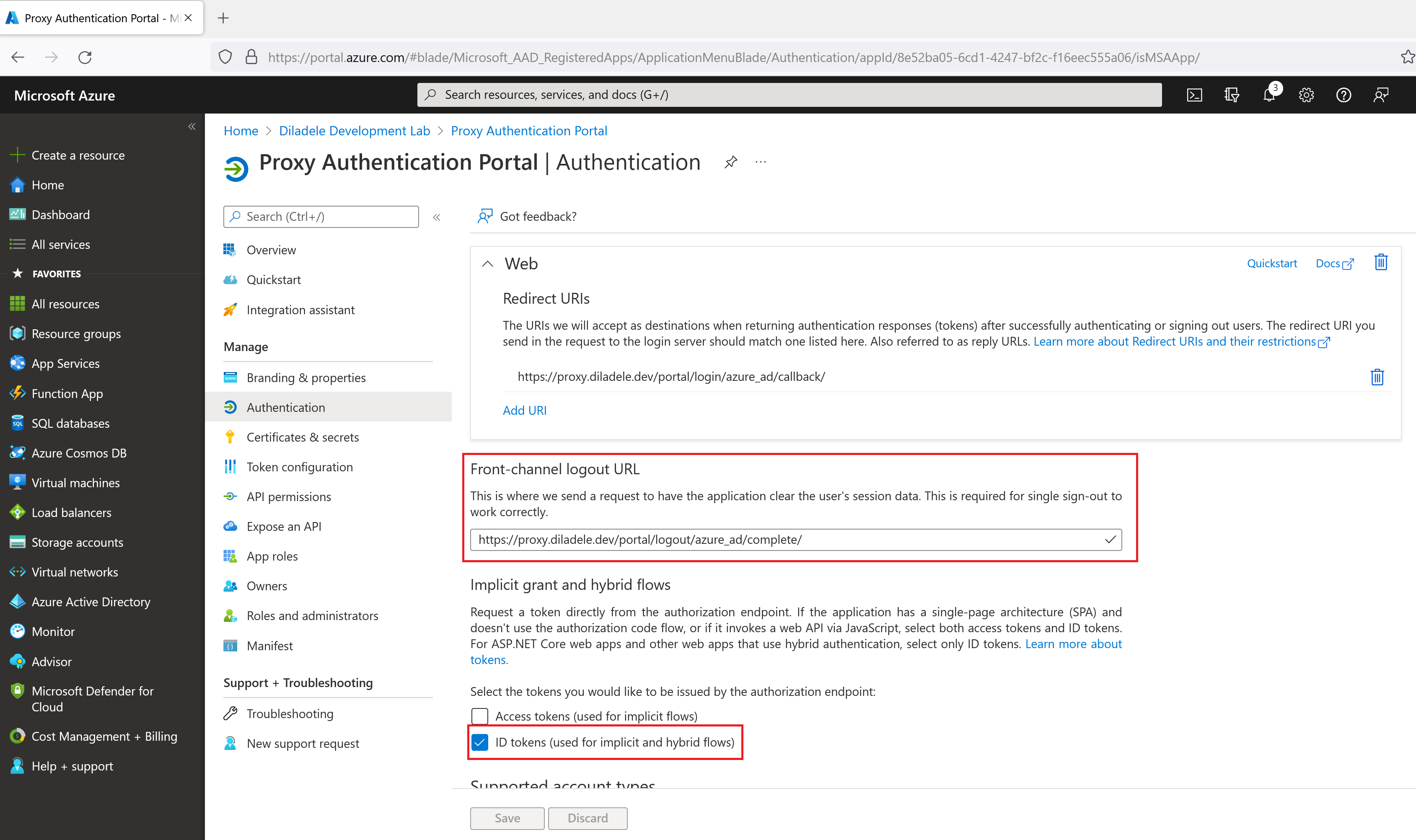
After registration, click the Authentication menu on the left and add the following values too.
Logout URL |
|
Implicit grant |
Set only ID tokens (used for implicit and hybrid flows) checkbox |
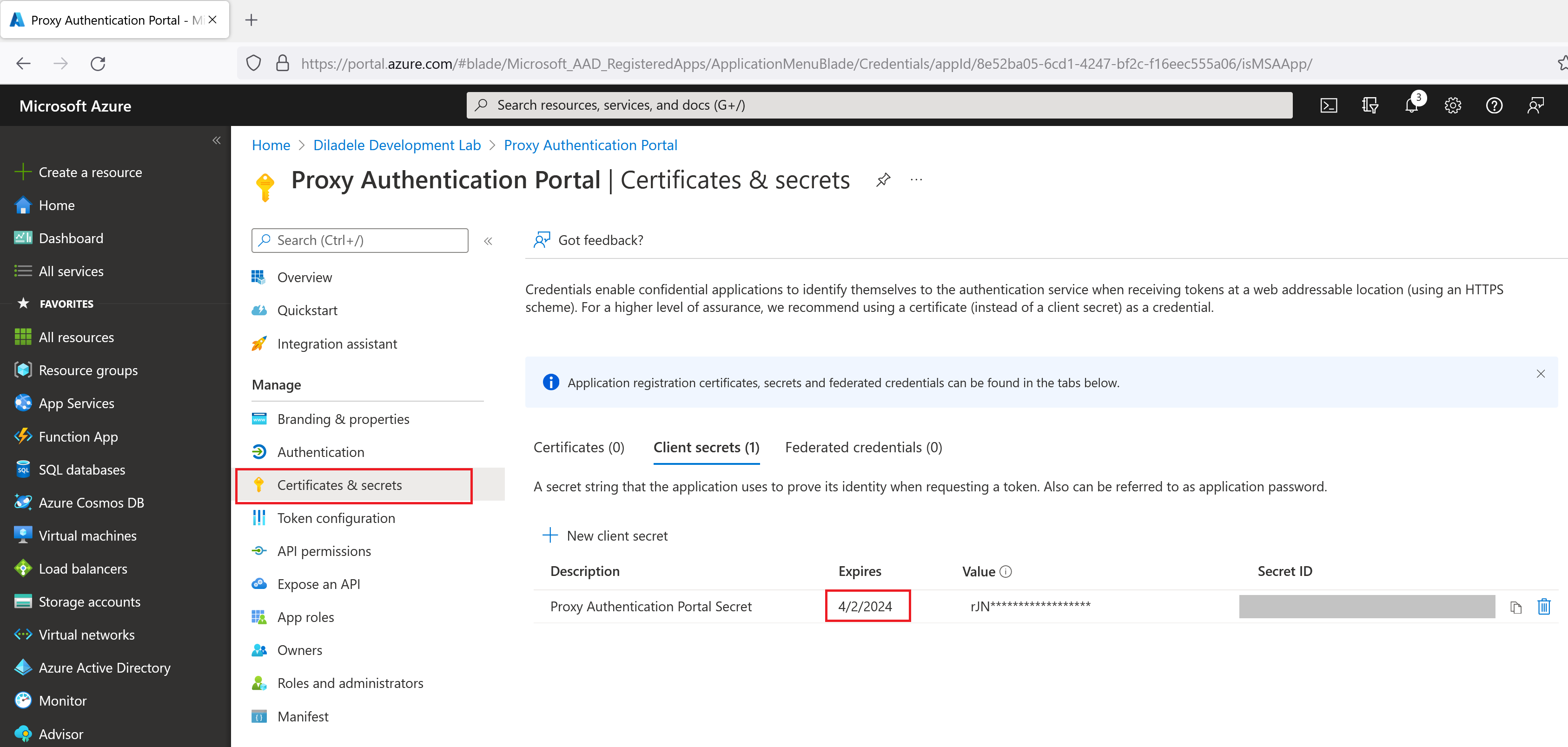
Next, generate a client secret (application password) for our app in Certificates and Secrets menu on the left. Be sure to note the client secret (which looks like a long randomly generated string of characters) because you would need it in actual Captive Portal settings later.
Important
The client secret has specific validity period after which it expires which will mean proxy authentication will fail. So, it might be a good idea somehow not to forget to re-generate that client secret in the future.
Finally, adjust the claims (information about the user) that will be present in the authentication response from Azure Active Directory to contain the list of assigned groups of the authenticated user. This will allow you to use security groups from Azure Active Directory as members of web filtering policies, greatly simplifying overall management of the application.
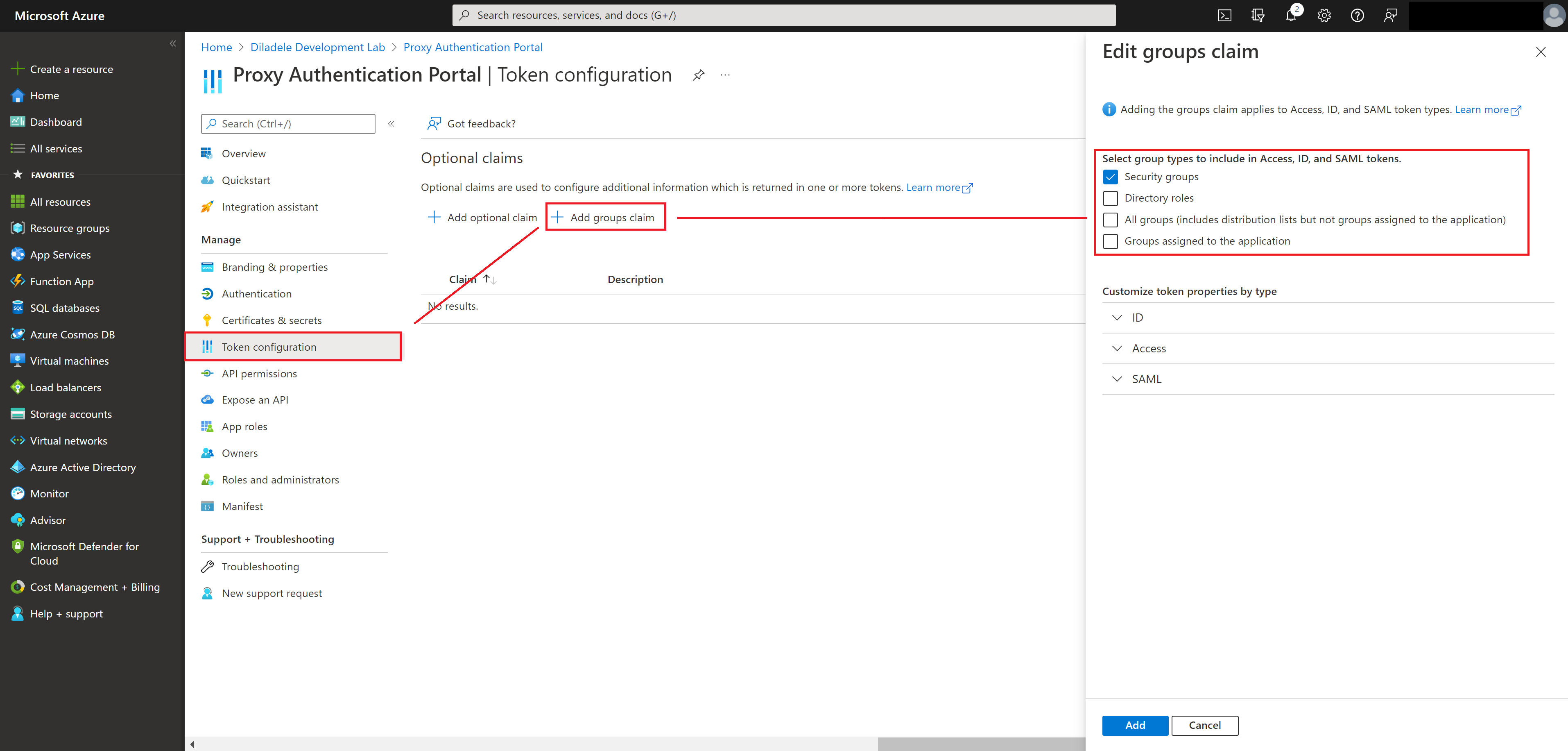
Add Required Exclusions in Admin UI¶
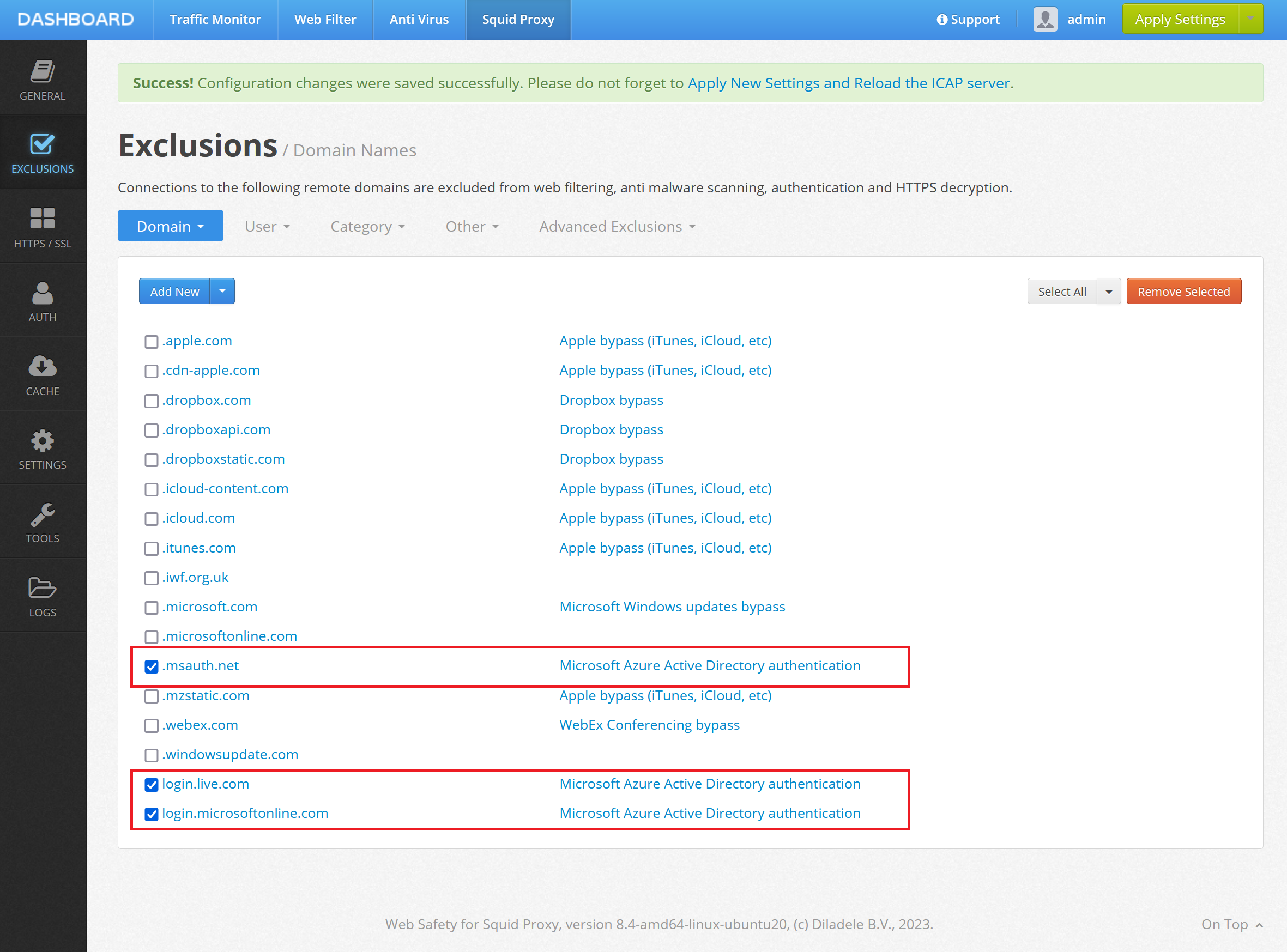
In order to let the Azure Active Directory to render the Azure Login UI without redirection we would need to add the following domains to Admin UI / Squid / Global Exclusions.
login.microsoftonline.com
login.live.com
.msauth.net
Just add those as shown on the following screenshot.
Configure Captive Portal in Admin UI¶
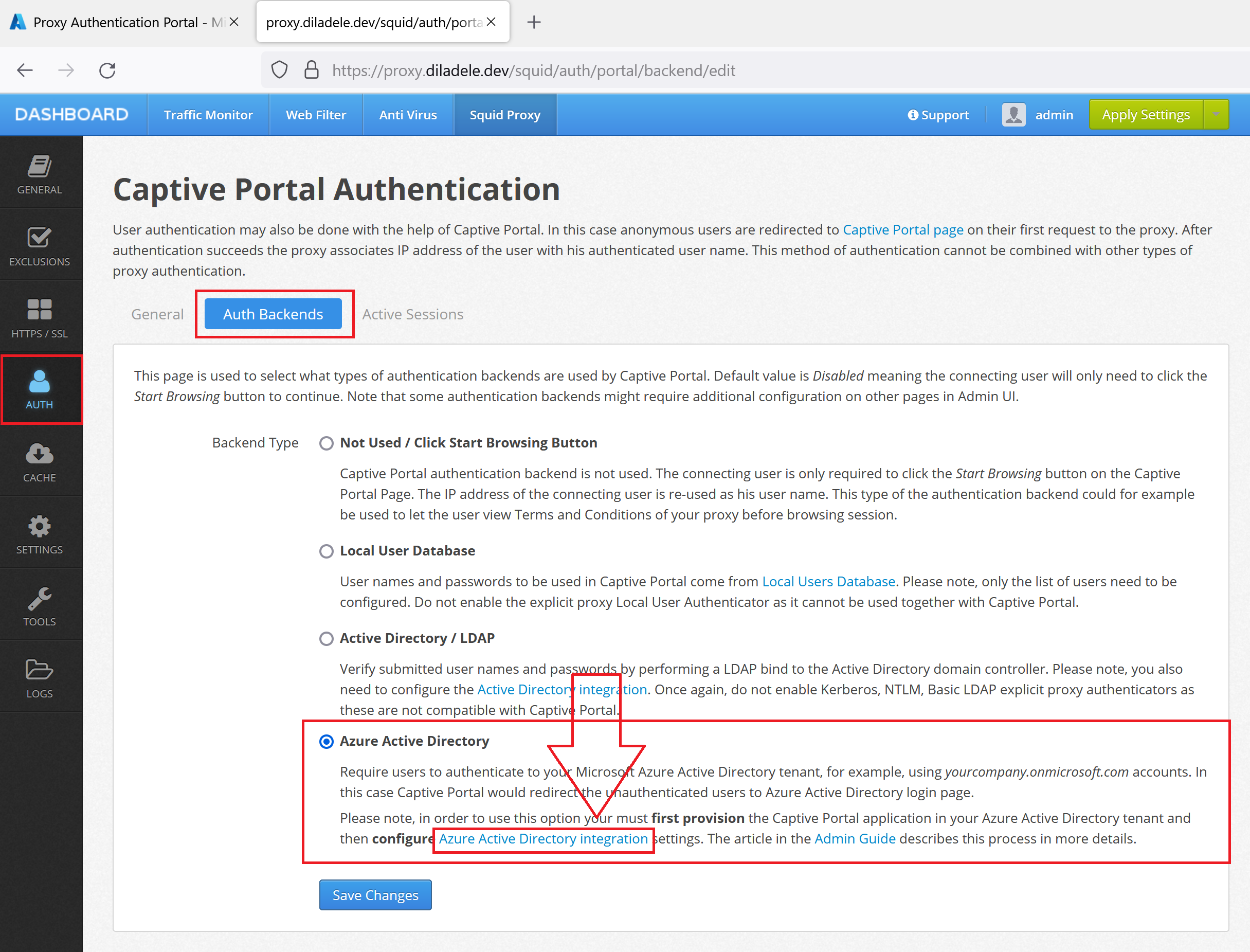
Next, we need to configure the proxy side for the Captive Portal authentication. This can be done at Admin UI / Squid / Auth / Captive Portal. Select the Auth Backends tab and click the Azure Active Directory integration settings.
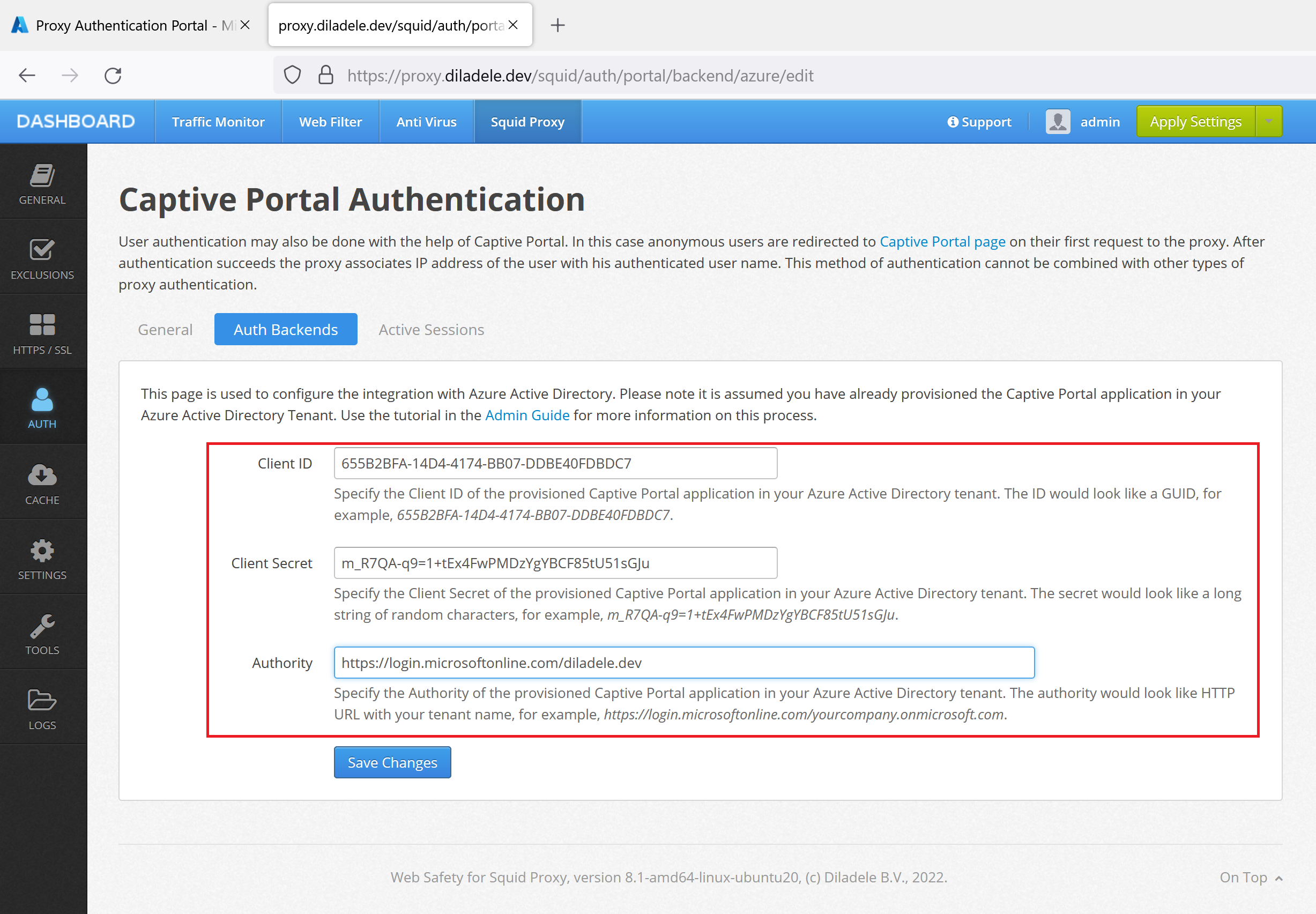
Fill in the settings with the following example information. Please be sure to put actual values for your specific case.
Authority |
|
Client ID |
a GUID string like 655B2BFA-14D4-4174-BB07-DDBE40FDBDC7 |
Client Secret |
long string of chars we have generated earlier |
Now switch to the General tab and set the Portal Address to your proxy fully qualified domain name (proxy.diladele.dev in our example). Note this is important as Captive Portal is not able to determine correct FQDN/IP address to redirect to if deployed in Microsoft Azure.
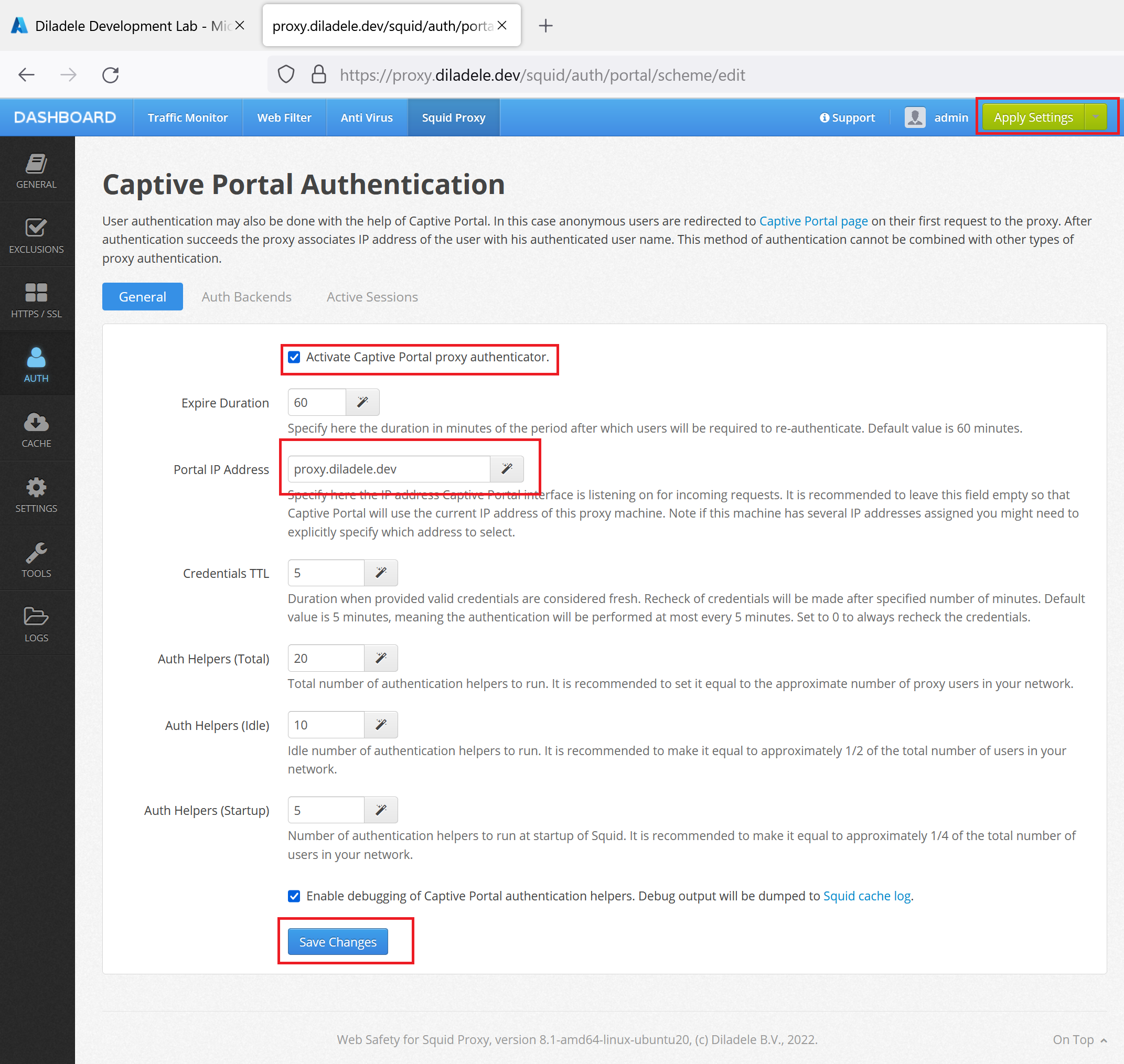
Click Save Changes and then Apply Settings from top right corner of Admin UI. Our proxy is now ready to redirect connecting clients to the Azure Active Directory for authentication.