How to switch Web Safety UI to HTTPS?¶
Important
This article is now obsolete. Starting from version 8 Web Safety Admin UI uses HTTPS by default.
UI of Web Safety is only accessible by HTTP after installation. To switch it to use HTTPS, login to the terminal console as root user and perform the following steps.
Note
The following commands need to be run from /opt/websafety/etc current directory. Also note you MUST change the Common Name proxy.example.lan below to FQDN of your proxy box!
Create self-signed HTTPS certificate that will be used by Apache web server to serve incoming HTTPS connections.
cd /opt/websafety/etc openssl req -x509 -nodes -days 1825 -newkey rsa:2048 -keyout gui.key -out gui.crt -subj "/C=NL/ST=Noord-Holland/O=Example Ltd./OU=IT/CN=proxy.example.lan/emailAddress=support@example.lan"
Enable SSL module for apache by running
a2enmod ssl.Modify configuration file
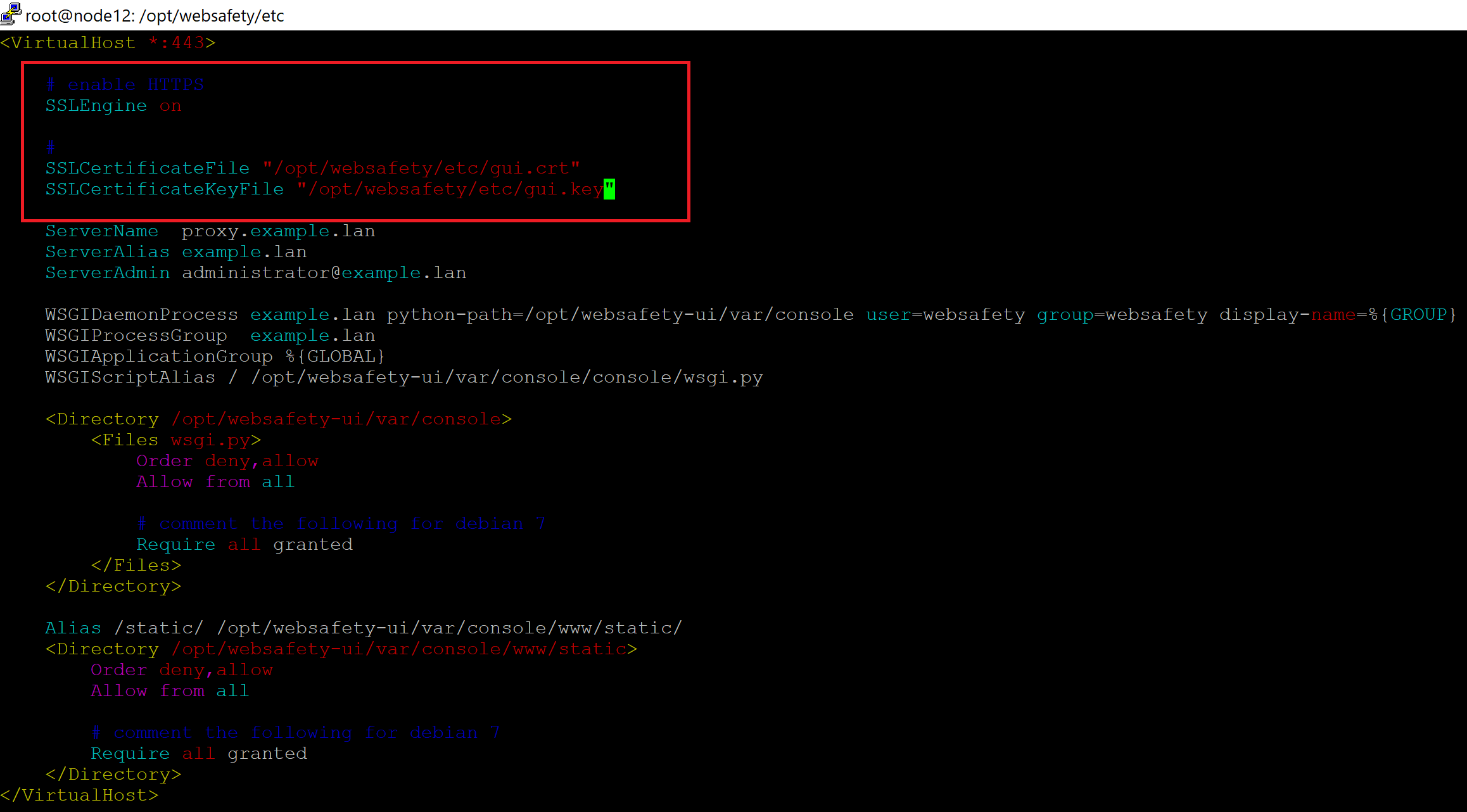
/etc/apache2/sites-enabled/websafety.conf- first changeVirtualHost *:80toVirtualHost *:443and then add the following lines (only leave SSLCertificate* lines for your version of course).# enable HTTPS SSLEngine on # SSLCertificateFile "/opt/websafety/etc/gui.crt" SSLCertificateKeyFile "/opt/websafety/etc/gui.key"
Restart Apache service by
systemctl restart apache2.
The UI of Web Safety web filter should now be accessible on port 443 using https://fqdn.of.your.proxy.box/ address. Note that port 80 will contain default Ubuntu Apache web page and thus can be ignored. If needed you can put a link on that page to point to the HTTPS version of the Admin UI, just change the contents of /var/www/html/index.html file and reload Apache.
Note
Limitations:
You SHOULD NOT access UI running on HTTPS through Squid - the Squid does not trust the Root CA by default and you will get X509_V_ERR_UNABLE_TO_GET_ISSUER_CERT_LOCALLY error.
Access to UI by IP will not work as certificate we have generated only contains FQDN as Common Name
Chrome 58+ will show [missing_subjectAltName] error because certificate we have generated does not have subjectAltName extension set. It is possible to fix that but then you need to use more complex command line as explained in https://security.stackexchange.com/questions/74345/provide-subjectaltname-to-openssl-directly-on-command-line