Check HTTP and HTTPS are Transparently Filtered¶
In order for HTTPS filtering to function correctly we must install the proxy certificate from /opt/websafety/etc/myca.der into Trusted Root Certification Authority on all workstations in our network. Please see the Install Trusted Certificates for instructions how to do it. The self signed root certificate to be installed is available from the login page of Web Safety.
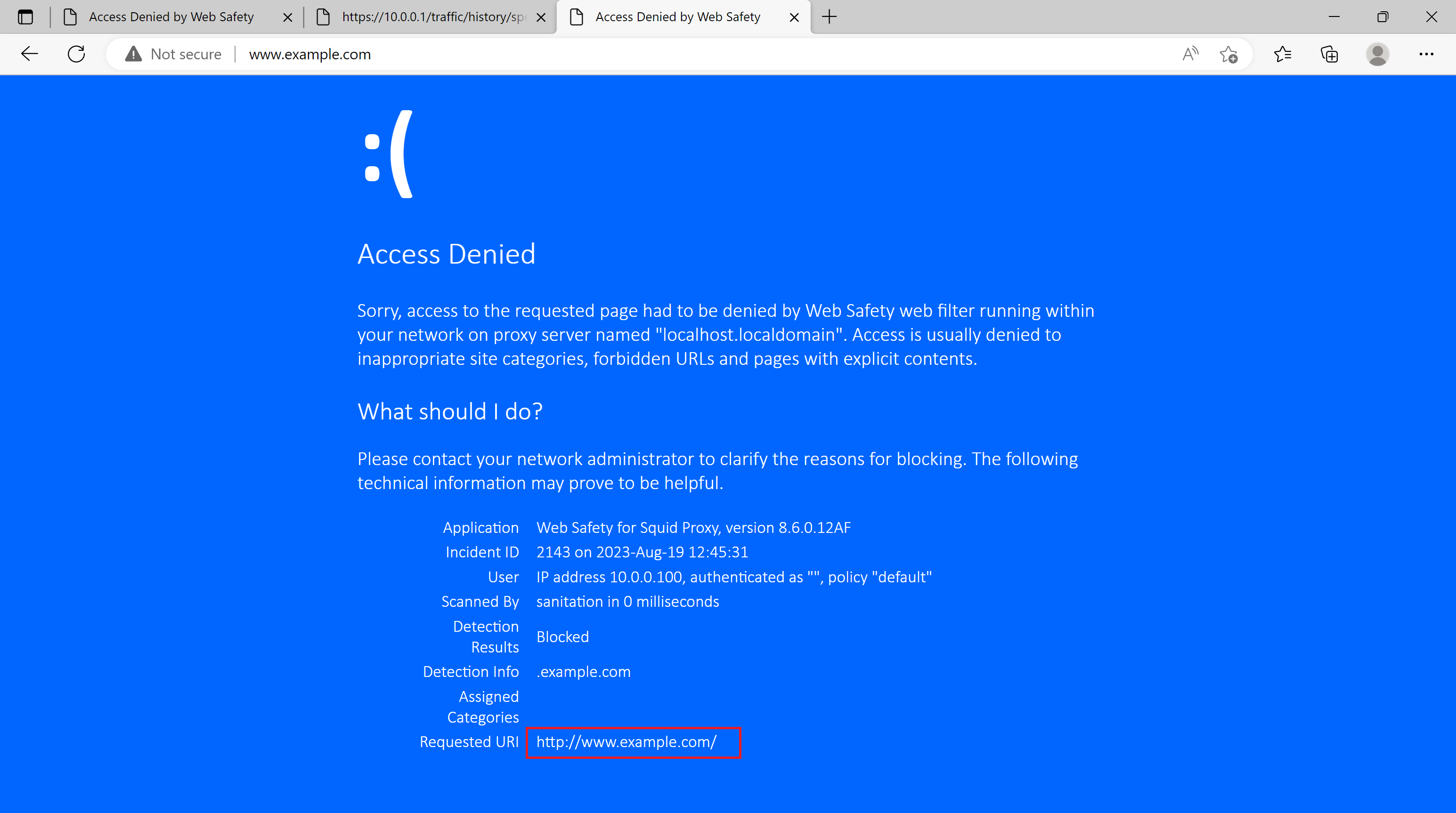
The following screenshot shows that normal HTTP requests were filtered transparently (we have manually blocked example.com for this tutorial as it is the only readily available site served through plain old HTTP nowadays).
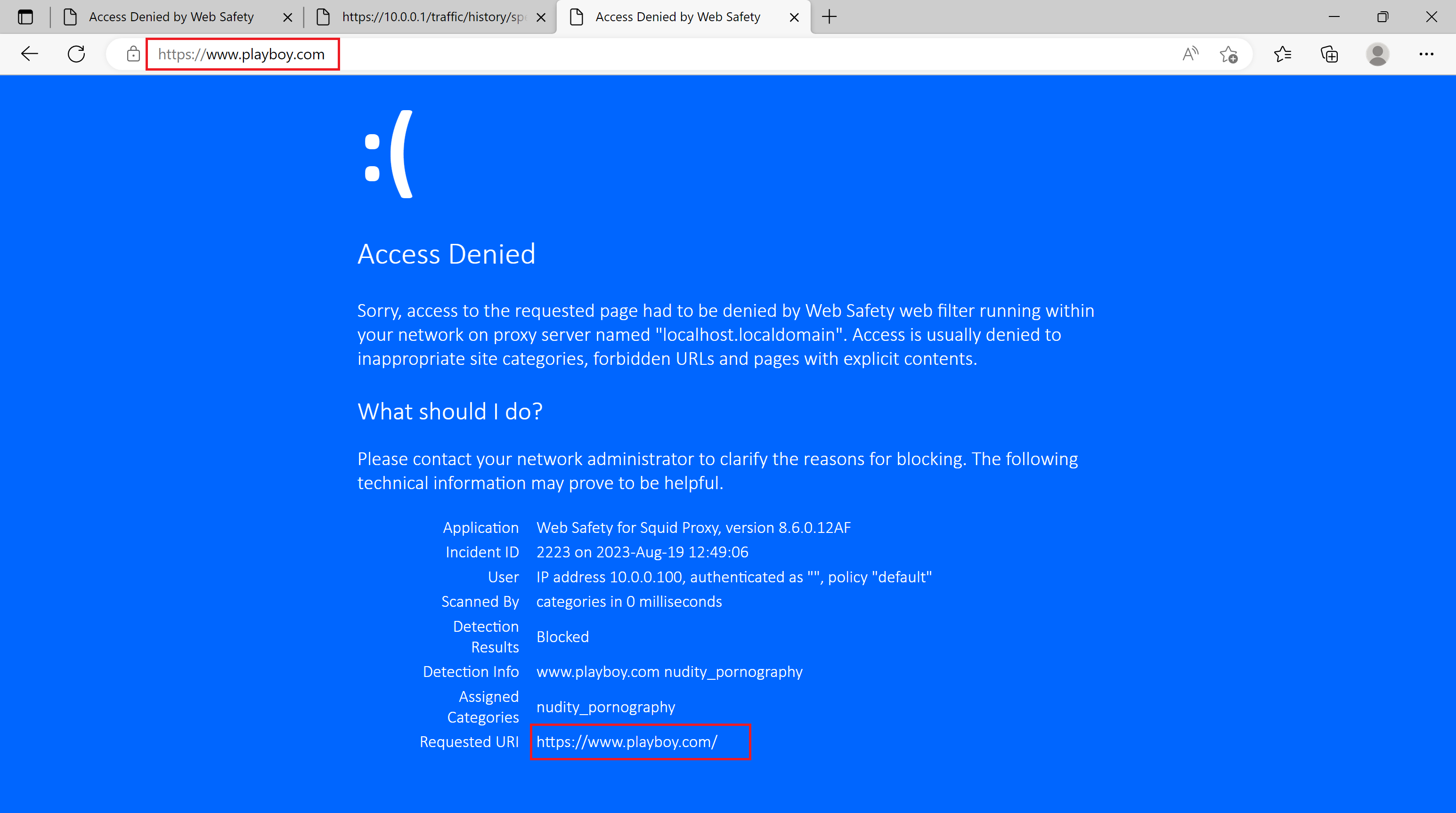
The following screenshot shows that HTTPS request to a prohibited site was successfully decrypted and blocked without explicit proxy set in the system.
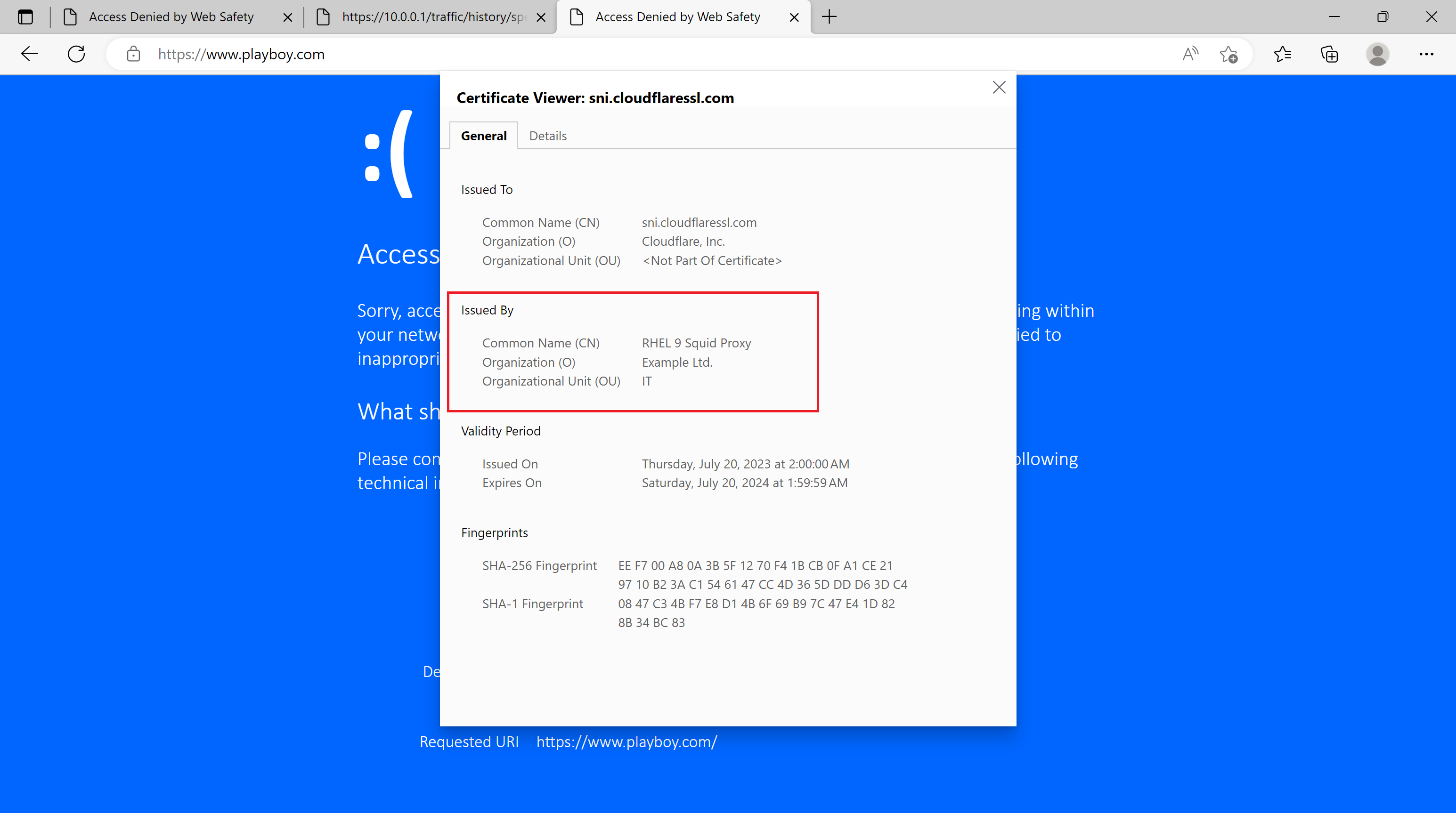
The site certificate was issued by our Root CA from the proxy.
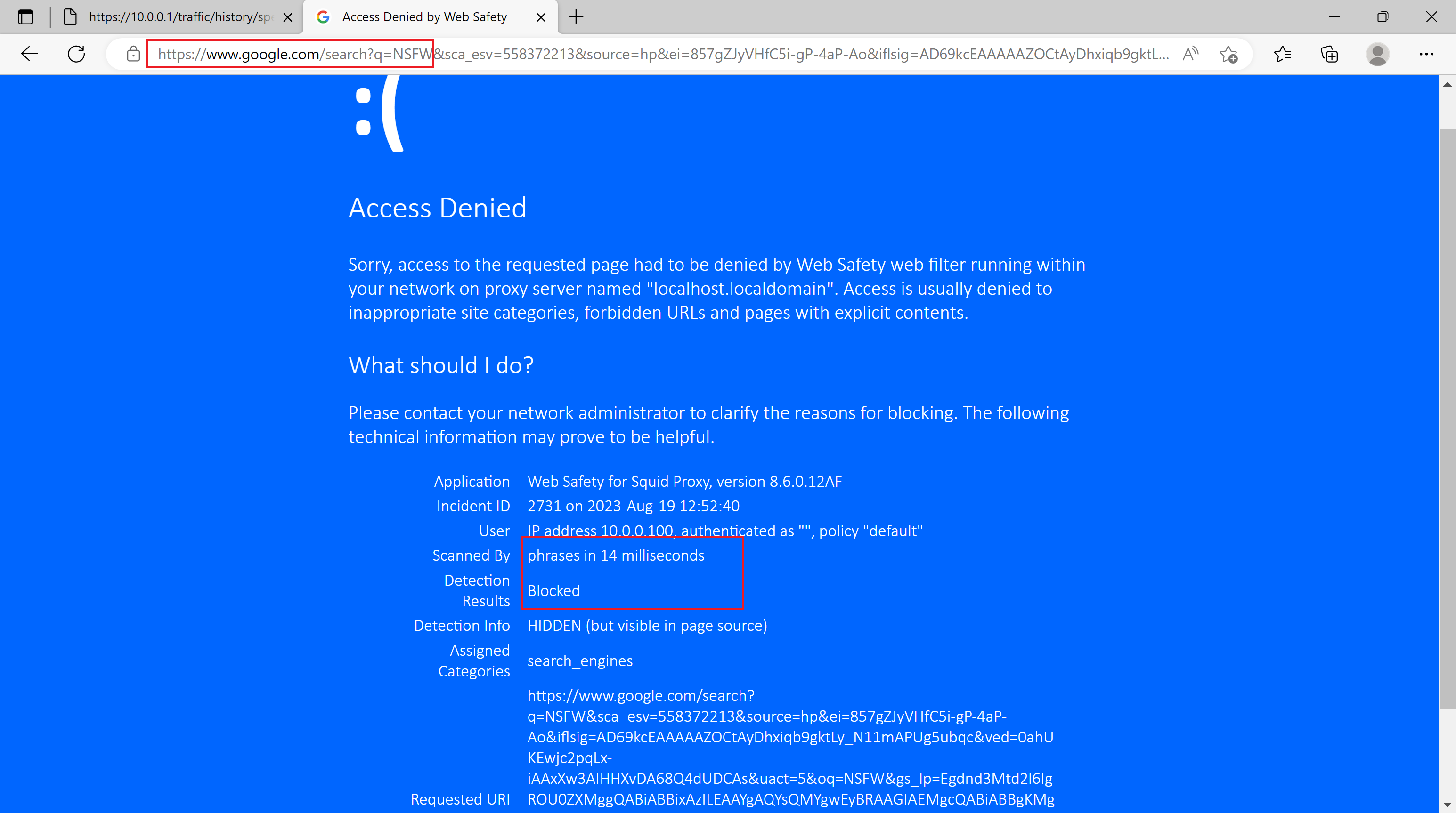
And finally browsing to Google and searching for an adult term (e.g. NSFW) we get the HTTPS request filtered and blocked transparently too.
Resume¶
We now have the default gateway in our network capable of transparently filtering HTTP and HTTPS traffic. All workstations in our network trust the root certificate from proxy and thus get their HTTPS request decrypted and filtered. Browsing environment in our network became much safer.
Some more ideas to implement
Block QUIC protocol to force Google Chrome to fallback to normal HTTP(S) and thus get filtered. See article http://wiki.squid-cache.org/KnowledgeBase/Block%20QUIC%20protocol