Integrate Squid into Firewall¶
Enable Gateway Mode¶
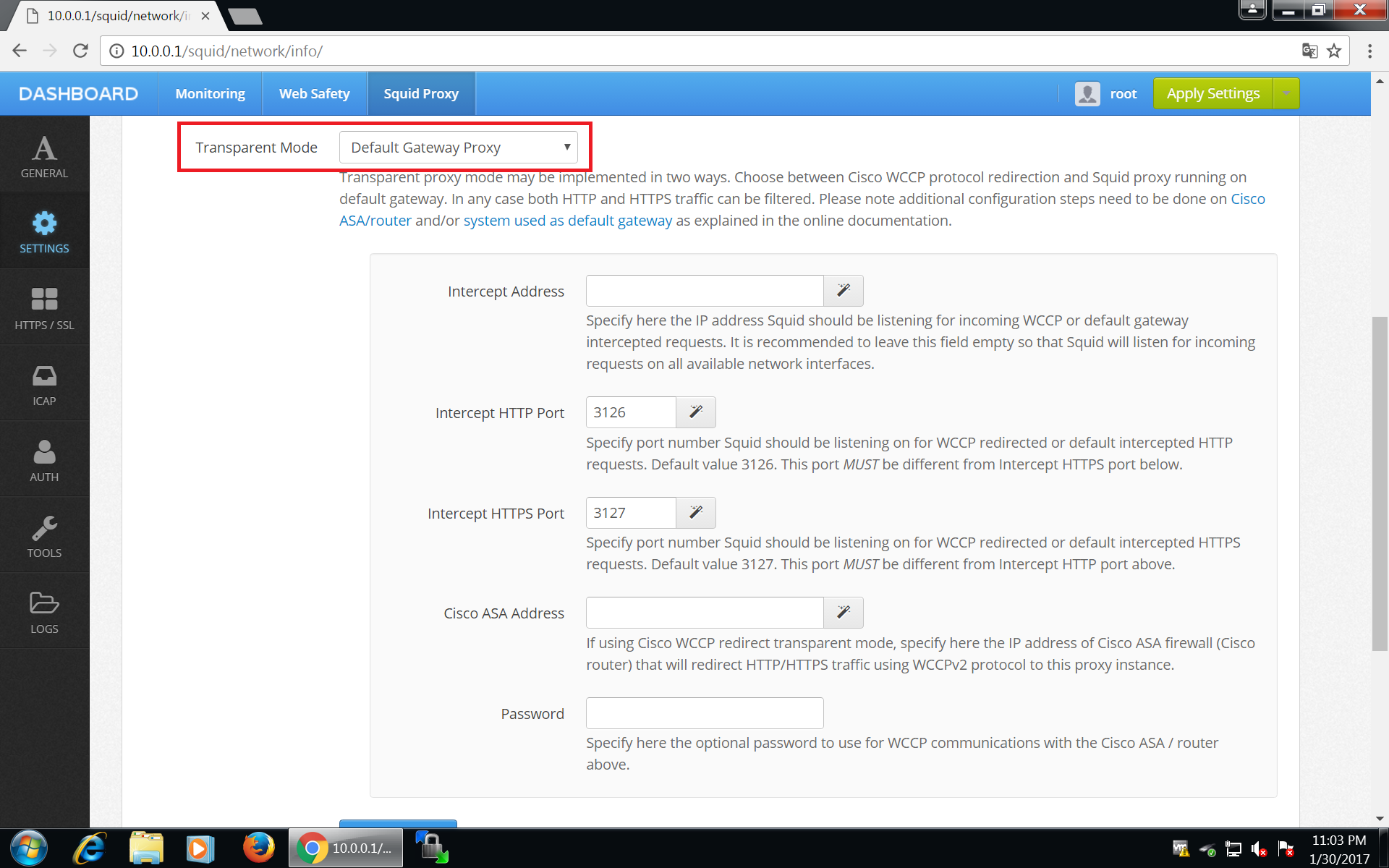
To make Squid listen on transparently redirected ports 3126 and 3127, login into Admin UI of Web Safety at http://10.0.0.1:8000 , click Squid / Settings / Network and select Default Gateway Proxy transparent mode as shown on the screenshot below. Do not forget to click Save and Restart afterwards.
After clicking Save and Restart, Admin UI will generate required http_port and https_port directives in /opt/websafety/etc/squid folder. These will look something like the following.
# port configuration
http_port 3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB cert=/opt/websafety/etc/myca.pem
http_port 3126 intercept
https_port 3127 intercept ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB cert=/opt/websafety/etc/myca.pem
Warning
Ports 3126 and 3128 are prefixed with http_port directive and port 3127 is prefixed with https_port directive.
Redirect HTTP and HTTPS Traffic¶
Squid will now listen to redirected traffic on ports 3126, 3127 and normal proxy traffic on port 3128. To finally redirect the HTTP and HTTPS traffic to Squid Proxy installed on our router we need to add the following rules to the nat table prerouting chain in /etc/nftables.conf file (the final version of that file is shown on the next step of this tutorial).
#
# skipped a lot of lines lines above!
#
table ip nat {
chain prerouting {
type nat hook prerouting priority 0; policy accept;
# redirect HTTP to locally installed Squid instance
tcp dport 80 redirect to :3126
# redirect HTTPS to locally installed Squid instance
# tcp dport 443 redirect to :3127
}
# enable nat for all packets going to the intenet through wan
chain postrouting {
type nat hook postrouting priority 100; policy accept;
oifname $wan_if masquerade
}
}
Restart your proxy box now and continue on the next step.