Check HTTP and HTTPS are Transparently Filtered¶
Install Trusted Proxy Certificate¶
In order for HTTPS filtering to function correctly we must install the proxy certificate from /opt/websafety/etc/myca.der into Trusted Root Certification Authority on all workstations in our network. Please see the Install Trusted Certificates for instructions how to do it. The self signed root certificate to be installed is available from the login page of Web Safety.
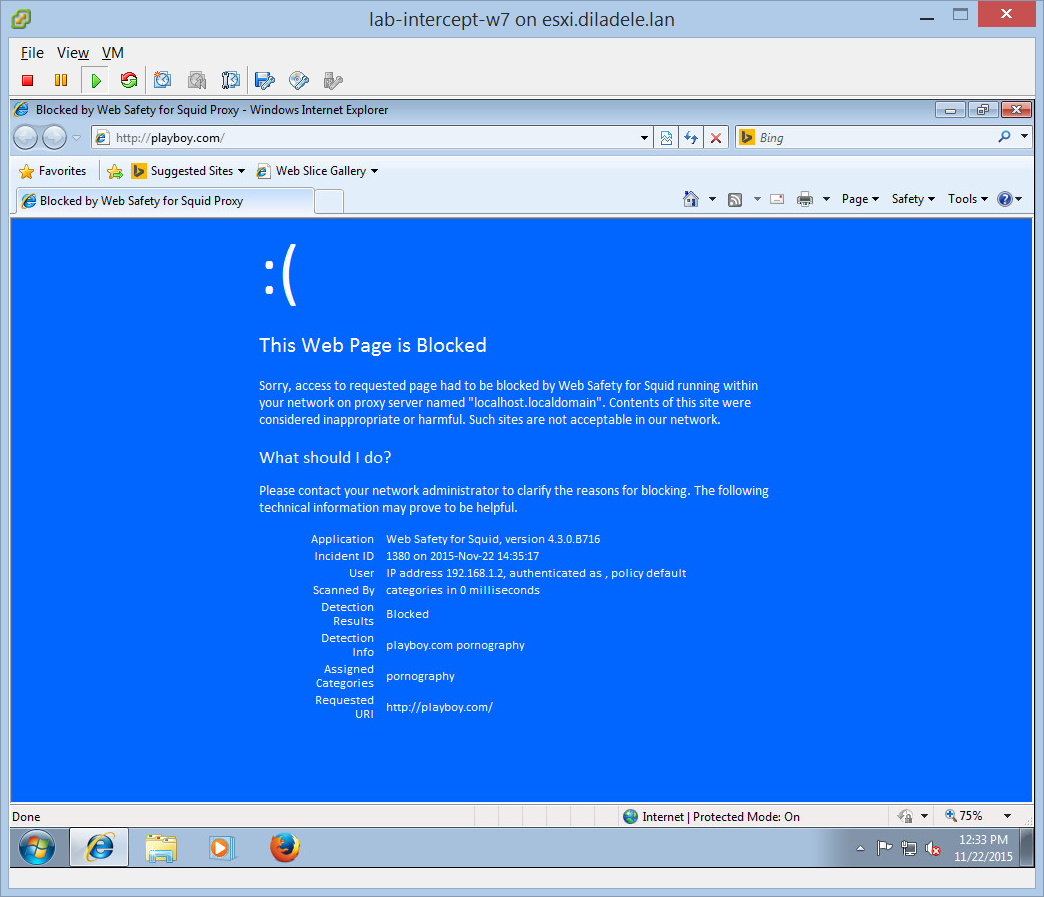
Filter Normal HTTP¶
The following screenshots show that normal HTTP requests were filtered transparently out of the box without any additional configuration.
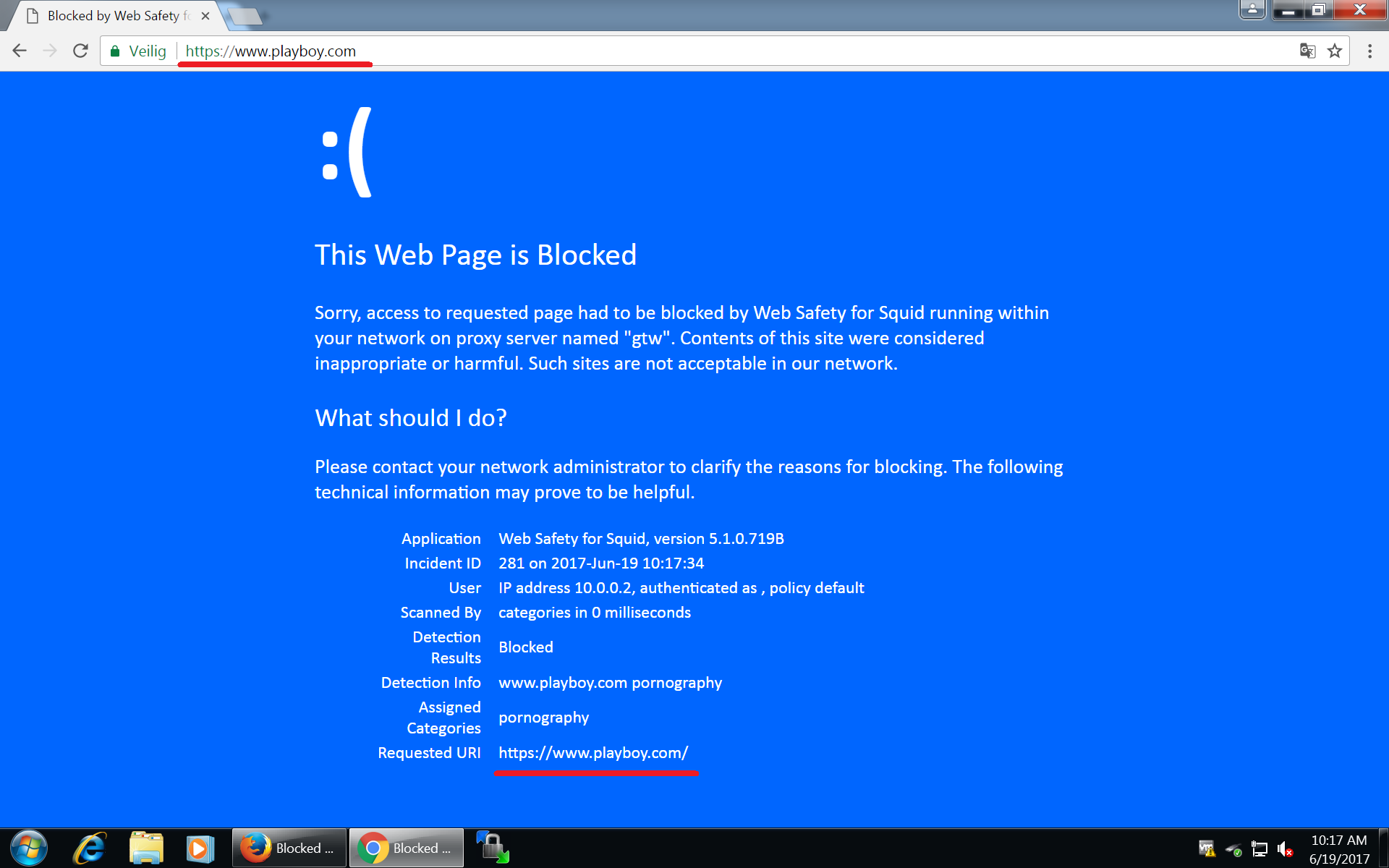
Decrypt and Filter HTTPS¶
To filter HTTPS we need to enable HTTPS decryption in Admin UI / Squid / HTTPS/ Mode. See Enable HTTPS Filtering in Admin UI article for more information. After enabling of HTTPS filtering access to HTTPS sites is also filtered correctly.
Resume¶
We now have the default gateway in our network capable of transparently filtering HTTP and HTTPS traffic. All workstations in our network trust the root certificate from proxy and thus get their HTTPS request decrypted and filtered. Browsing environment in our network became much safer.
Important
Block the QUIC protocol on your firewall, otherwise Chrome will be able to bypass the transparently redirected proxy when going to QUIC enabled sites, like google.com, youtube.com, etc.
To block the QUIC protocol, add the following rule to the input chain. See more info at http://wiki.squid-cache.org/KnowledgeBase/Block%20QUIC%20protocol.
# uncomment this to block quic protocol from lan
udp dport { 80, 443 } reject with icmpx port-unreachable