Admin UI via HTTPS¶
Starting from Web Safety version 8.1 Admin UI is accessible by HTTPS by default. To get to the Admin UI type the https://ip_address_of_the_proxy/ URL in your browser address box.
Certification Warning¶
Default HTTPS certificate for Admin UI was generated at the development time in /opt/websafety-ui/etc folder using the following command.
openssl req -x509 -nodes -days 1825 \
-newkey rsa:2048 -keyout admin_ui.key -out admin_ui.crt \
-subj "/C=NL/ST=Noord-Holland/O=Example Ltd./OU=IT/CN=proxy.example.lan/emailAddress=support@example.lan"
The default certificate is self signed, so you will get a self signed warning from the browser when navigating to the Admin UI for the first time. To silence the warning and continue to the Admin UI click the Accept Risk and Continue button.
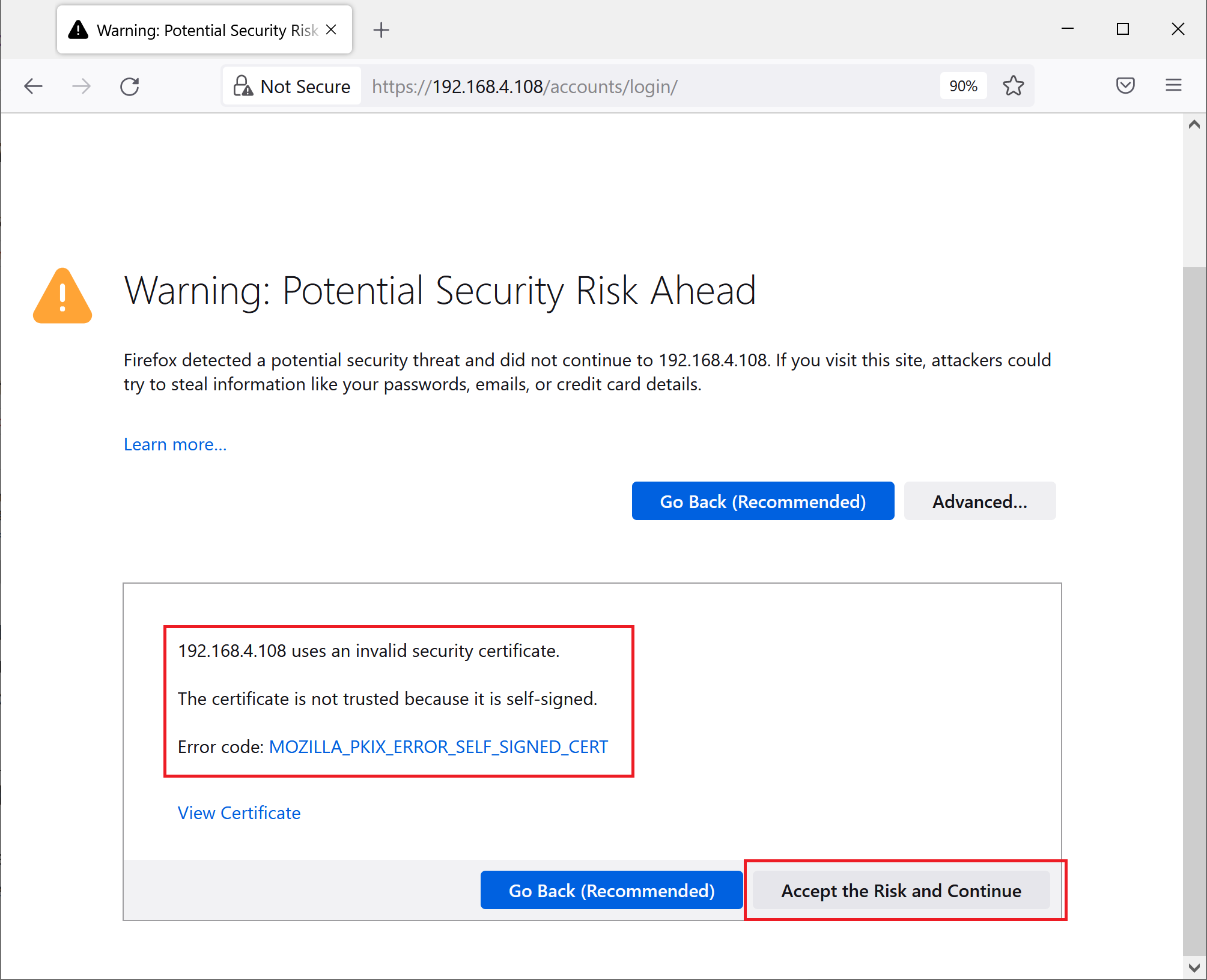
Note that default certificate is the same for all deployed instances of the application so it is a good idea to run this command again to be sure you are trusting only your specific certificate which is owned and controlled by you.
Install Your Own Certificate¶
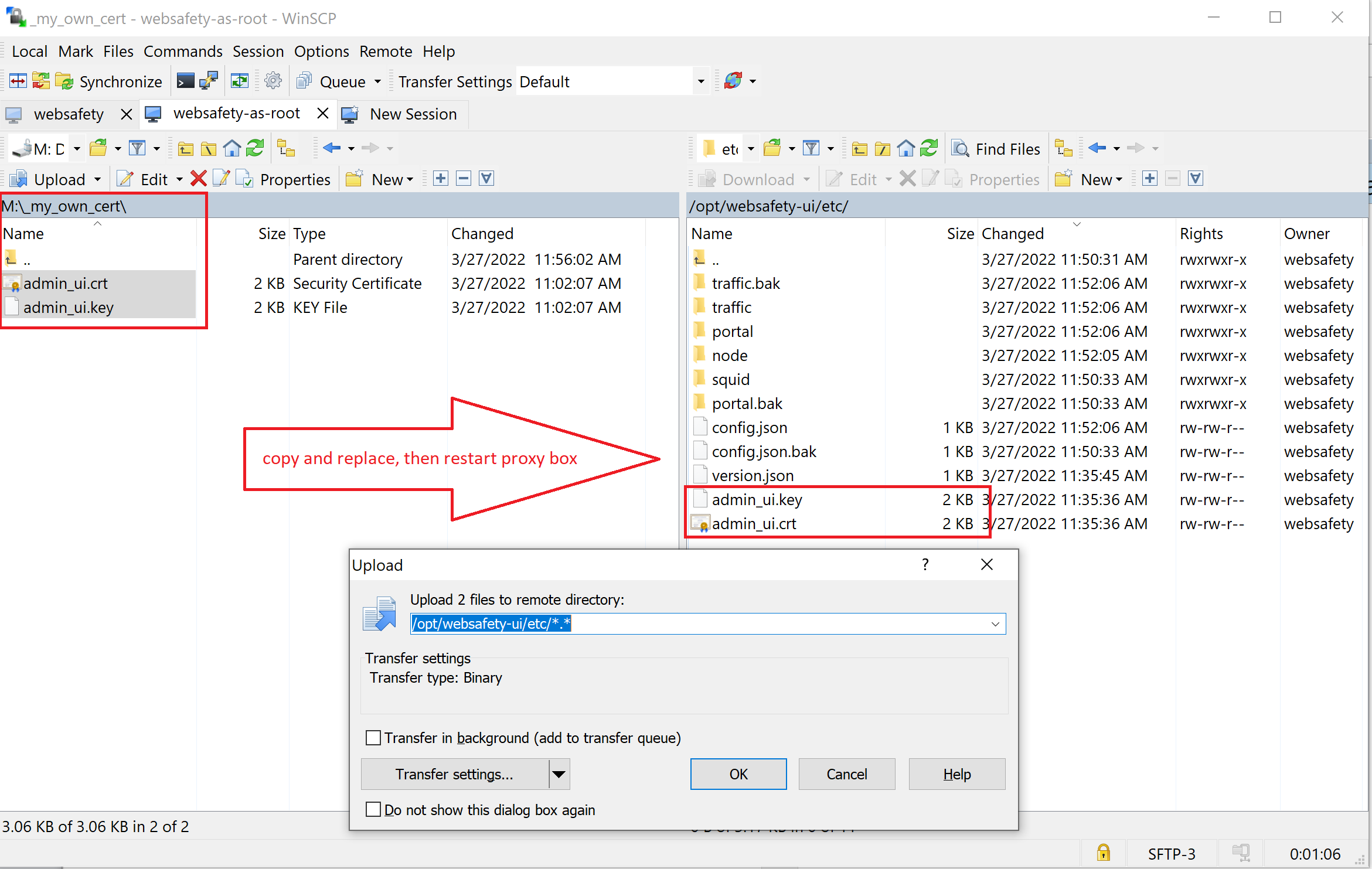
If you have a third party certificate for Admin UI, you can use winscp to upload it into /opt/websafety-ui/etc folder. Be sure to name the key as admin_ui.key and certificate as admin_ui.crt. Both files should be readable by the Apache 2 (it is so by default).
Regenerate with Trusted Root CA¶
If you decide to regenerate your own certificates for Admin UI another possible way is to reuse your own HTTPS decryption certificate for this purpose. When you enable HTTPS decryption your browser trusts this decryption certificate anyway so it makes good sense to re-use that trust for HTTPS access to Admin UI.
To do that run the following script being root in the folder /opt/websafety-ui/etc. Be sure to adjust the script to use your actual IP address and domain name of the proxy machine.
# change to actual domain name and IP address of your proxy that Admin UI runs on
# this important - otherwise when accessing your proxy by FQDN or IP address your
# browser will show the Warning: Potential Security Risk Ahead - SSL_ERROR_BAD_CERT_DOMAIN
# error
LOCAL_FQDN="proxy.example.lan"
LOCAL_IP="127.0.0.1"
#
# create a key - be sure to change the subj fields if needed (optional)
#
openssl req \
-newkey rsa:2048 \
-nodes \
-keyout admin_ui.key \
-subj "/C=NL/ST=Noord-Holland/L=Amsterdam/O=Example B.V./OU=IT/CN=$LOCAL_FQDN" \
-out admin_ui.csr
#
# use Root Decryption Certificate from Web Safety to sign it
#
openssl x509 \
-req \
-extfile <(printf "subjectAltName=DNS:$LOCAL_FQDN,DNS:$LOCAL_IP,IP:$LOCAL_IP") \
-days 1825 \
-in admin_ui.csr \
-CA /opt/websafety/etc/myca.pem -CAkey /opt/websafety/etc/myca.pem -CAcreateserial \
-out admin_ui.crt
# change the owner to match other files
chown websafety:websafety admin_ui.*
# and restart the apache now
systemctl restart apache2