Identify Simple LDAP Bindings¶
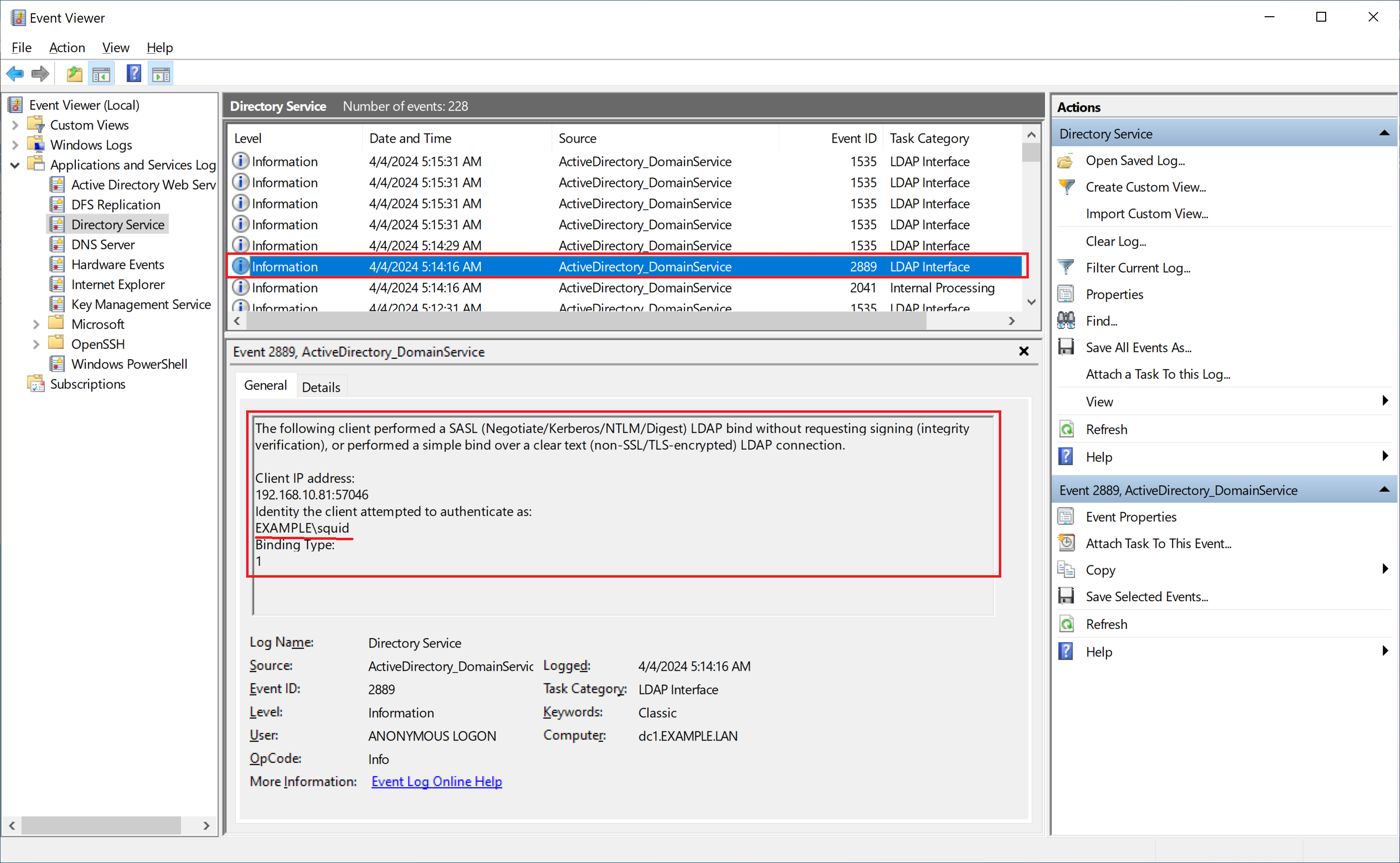
When simple LDAP binds are detected by the system, event log of the domain controller will show the warning event 2886 as presented on the following image.
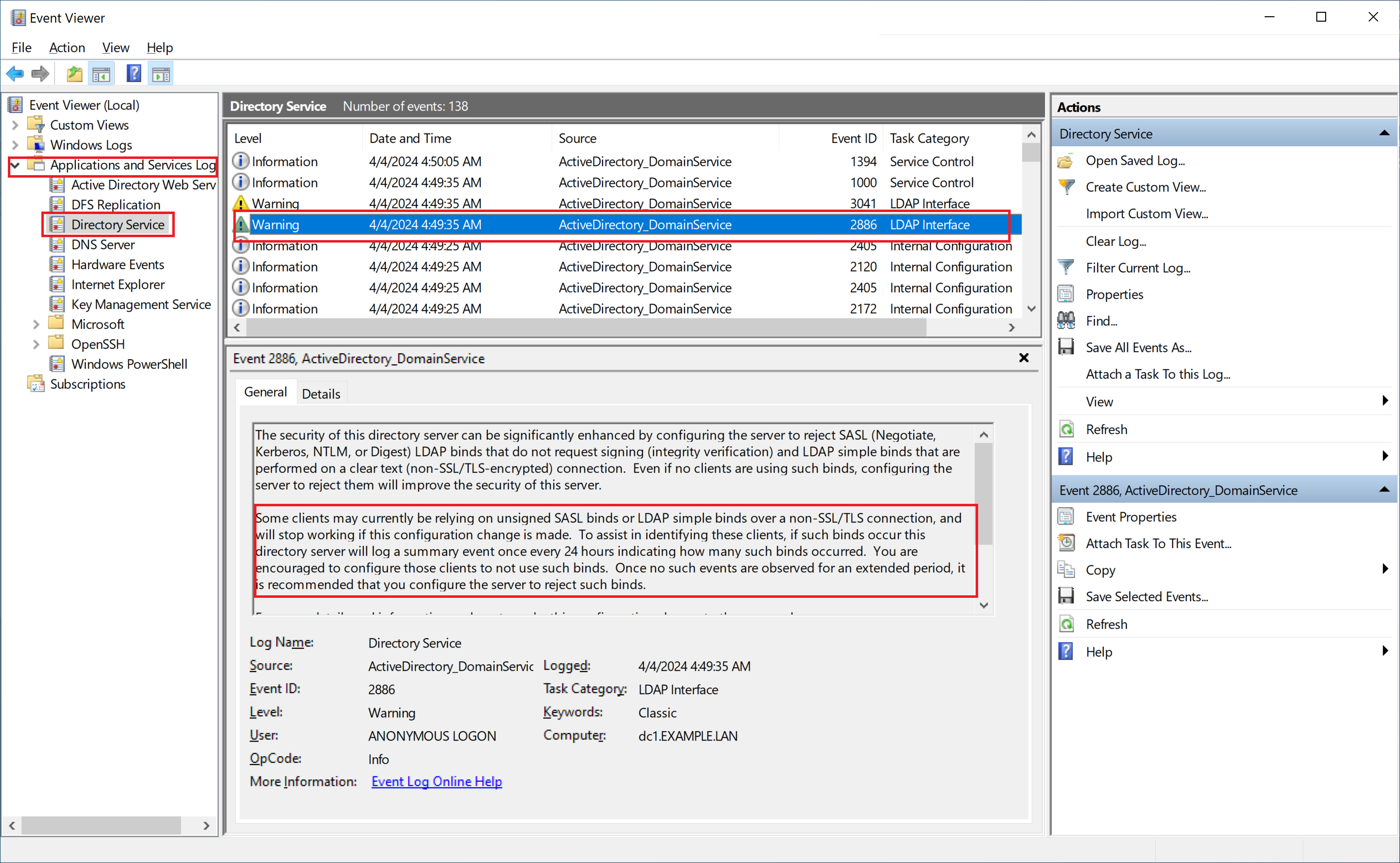
The security of this directory server can be significantly enhanced by configuring the server
to reject SASL (Negotiate, Kerberos, NTLM, or Digest) LDAP binds that do not request signing
(integrity verification) and LDAP simple binds that are performed on a clear text
(non-SSL/TLS-encrypted) connection. Even if no clients are using such binds, configuring
the server to reject them will improve the security of this server.
...
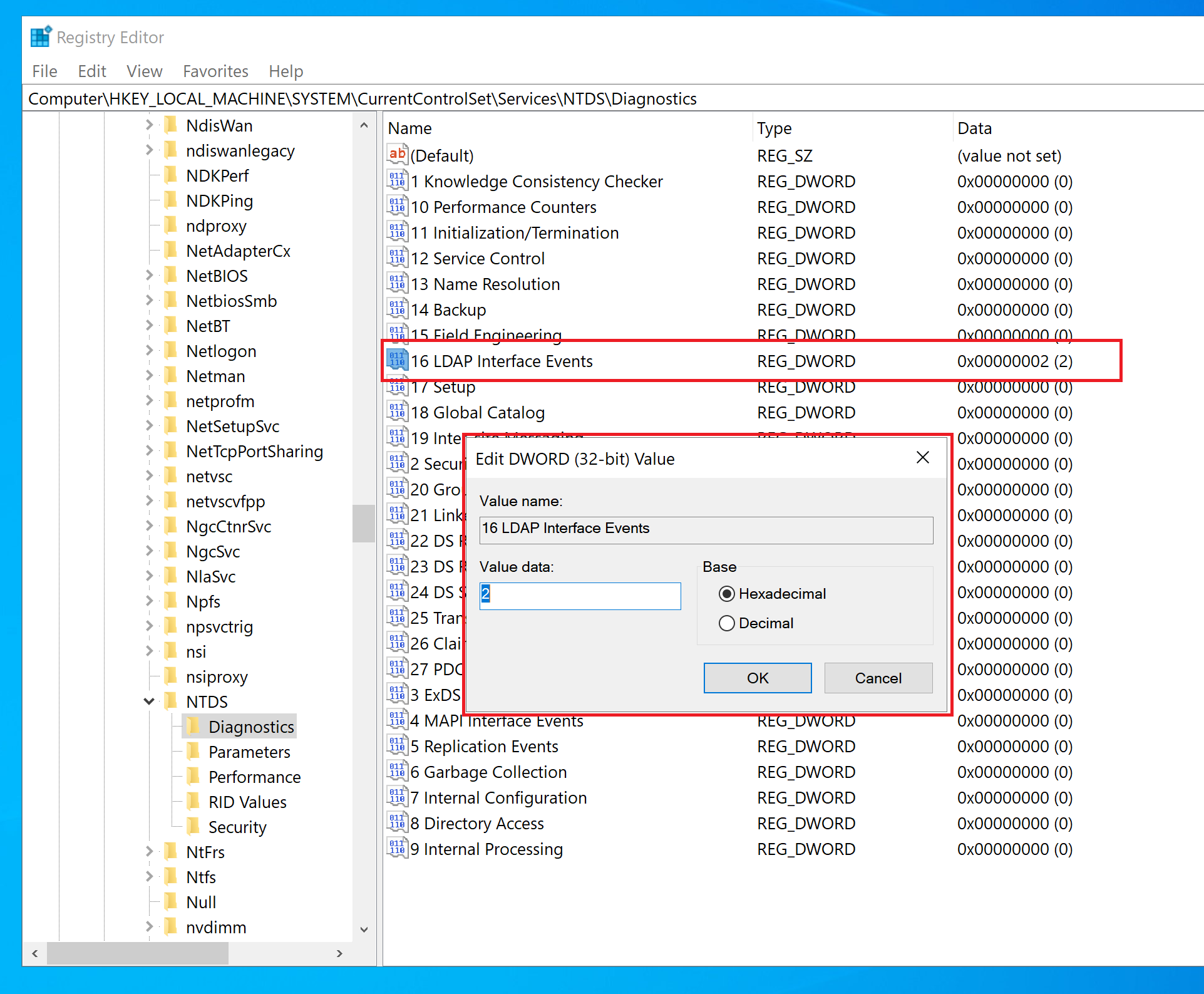
You can enable additional logging to log an event each time a client makes such a bind,
including information on which client made the bind. To do so, please raise the setting
for the "LDAP Interface Events" event logging category to level 2 or higher.
It is possible to find out which applications use simple LDAP by increasing the log level of Active Directory Domain Services component by modifying the registry on your domain controller as explained in the article https://learn.microsoft.com/en-US/troubleshoot/windows-server/active-directory/configure-ad-and-lds-event-logging.
The following screenshot shows the required manual changes.
Reboot your domain controller to make this change effective. After reboot, open Admin UI of Web Safety and navigate to Squid / Auth / Active Directory / LDAP Integration and click the Test Connection button. The application will perform simple LDAP bind to the LDAP server. As we only increased the level of diagnostics on the domain controller, test should succeed.
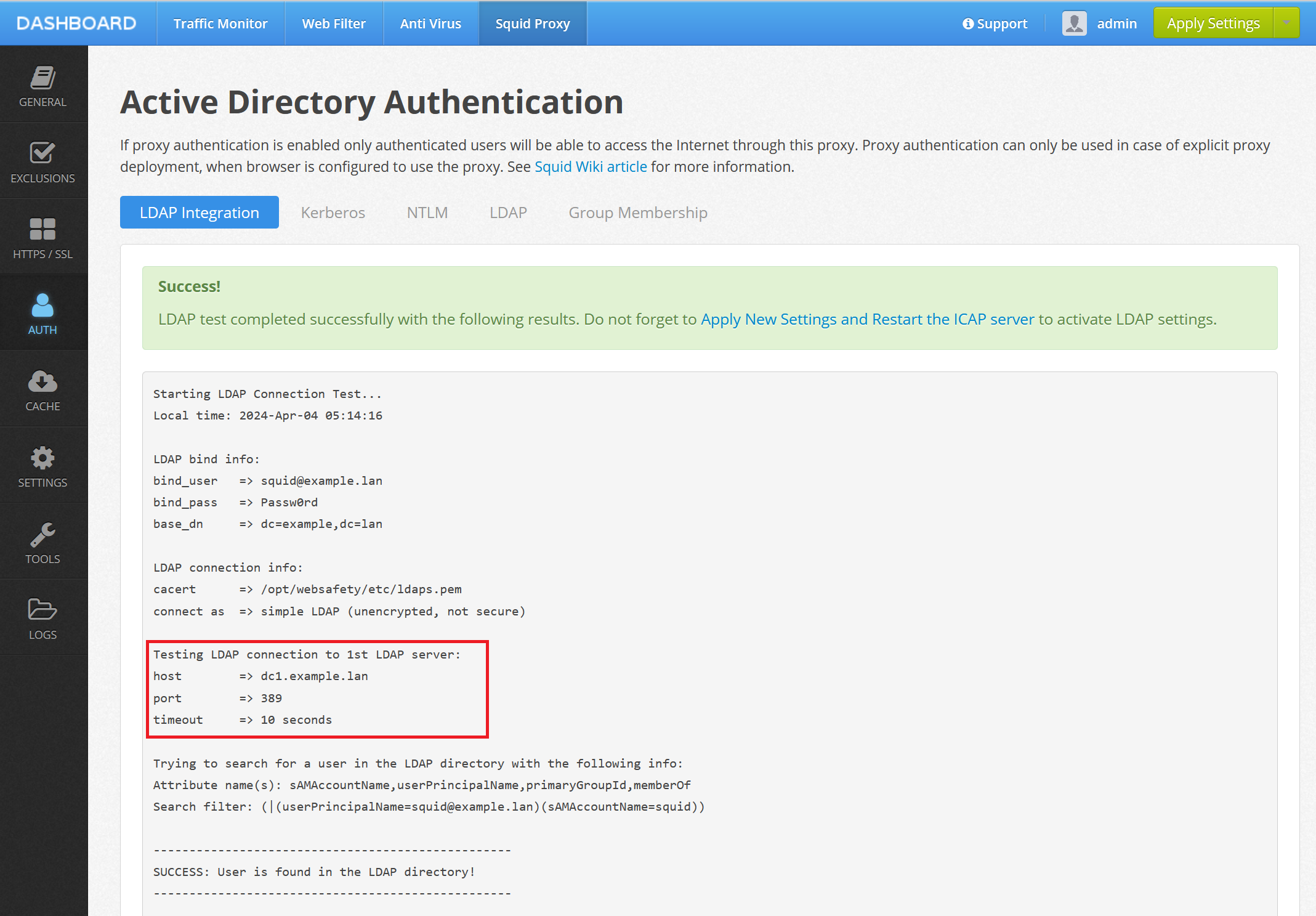
The event log will now contain the following event 2889, clearly indicating that the simple LDAP was used.