Troubleshooting Squid Active Directory Integration¶
It is recommended to follow these troubleshooting steps when Active Directory integration of Web Safety is not functioning as required:
Check that the domain user that you are using to test proxy authentication has a valid password in Active Directory domain and that password is not already expired. If it is expired - proxy authentication will not work and browser will continuously show authentication popup box! Ideally you should do logout/login on the desktop before any troubleshooting steps.
Check you are accessing the proxy from DOMAIN JOINED Windows PC and from DOMAIN USER ACCOUNT if you are testing Kerberos authentication. Validate Kerberos authentication using latest version of Microsoft Internet Explorer. If neccessary, clear the credentials cache by running
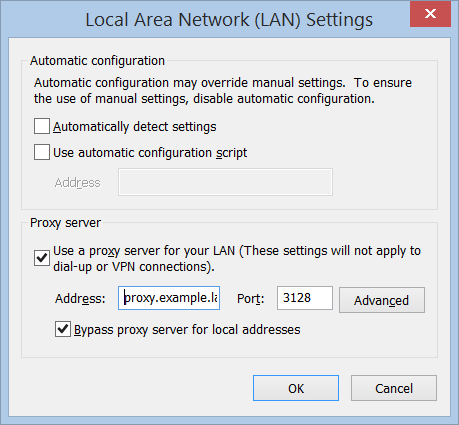
rundll32.exe keymgr.dll , KRShowKeyMgrand reboot the client machine.Check if proxy in the browser network settings is specified by FQDN and not by IP address (i.e. proxy.example.lan is correct both 192.168.1.2 and proxy are incorrect). Usually the following line in cache.log illustrates this problem:
2016/02/13 17:35:07| ERROR: Negotiate Authentication validating user.
Error returned 'BH gss_acquire_cred() failed: Unspecified GSS failure.
Minor code may provide more information. No key table entry found for HTTP/proxy@EXAMPLE.LAN
Check date and time settings in Squid proxy by running
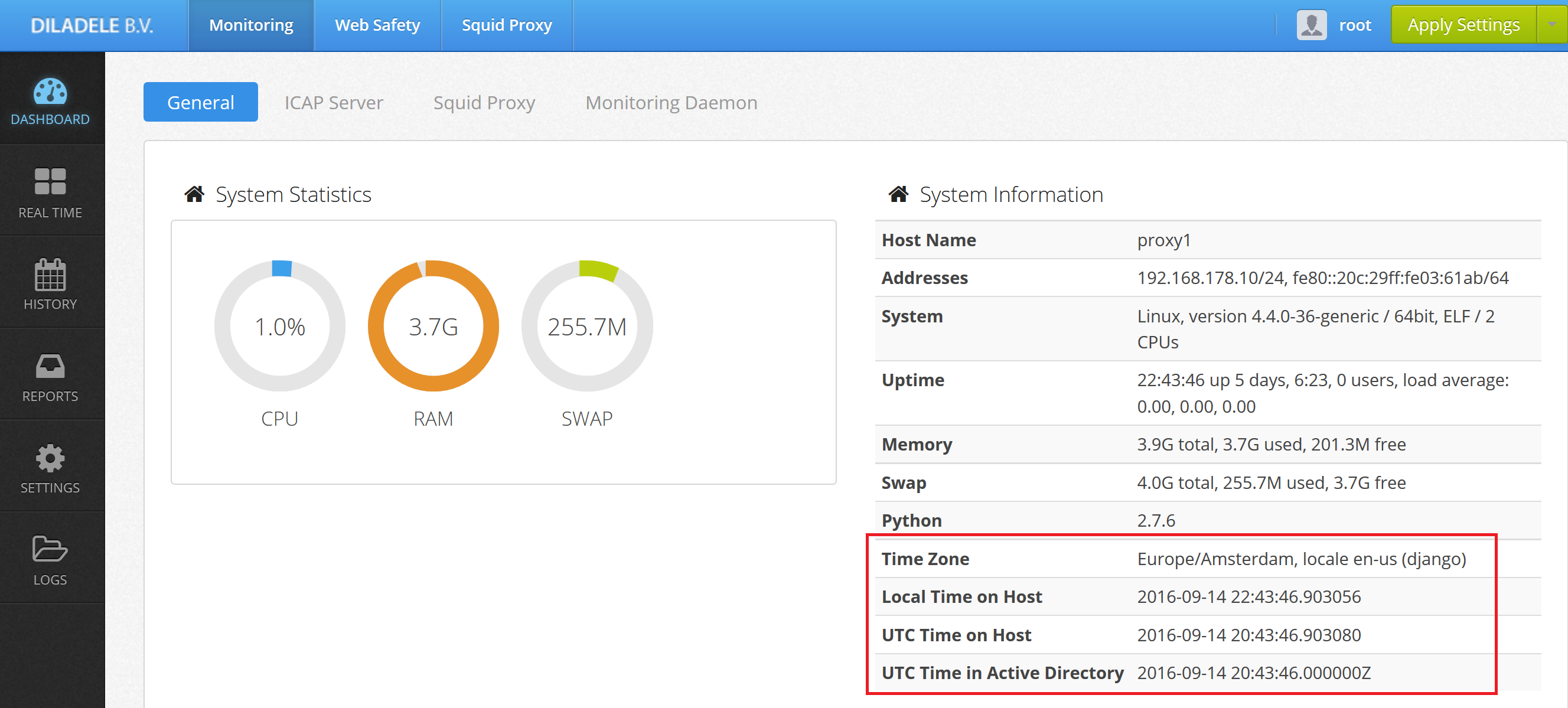
datein the command terminal. It should be the same as on your domain controller. It is also possible to see if the time difference on your proxy and domain controller is too big (more than 5 minutes) - in this case Kerberos authentication will always fail.
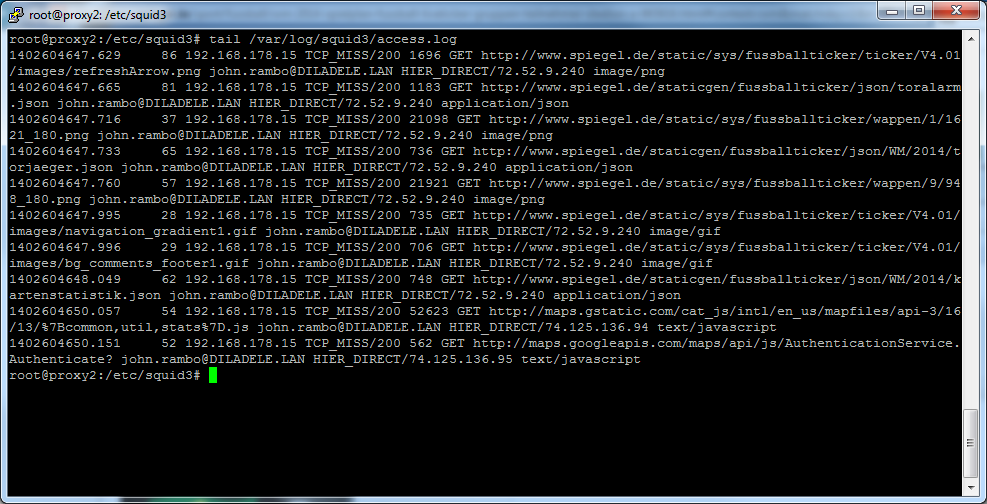
Check user authentication and authorization on your Squid proxy is set up correctly. User names in form of user@EXAMPLE.LAN or EXAMPLE\User need to be present in the Squid log file (usually /var/log/squid/access.log). If these are not present check your browser is set to use the proxy as FQDN and NOT AS IP ADDRESS.
Check your Squid configuration file contains references to include files generated by UI of Web Safety as explained on article Squid Configuration with Proxy Authentication.
Check if LDAP server settings in UI / Squid / Auth / Domain Info are correctly configured. Click the Test Connection button, check the output of this command.
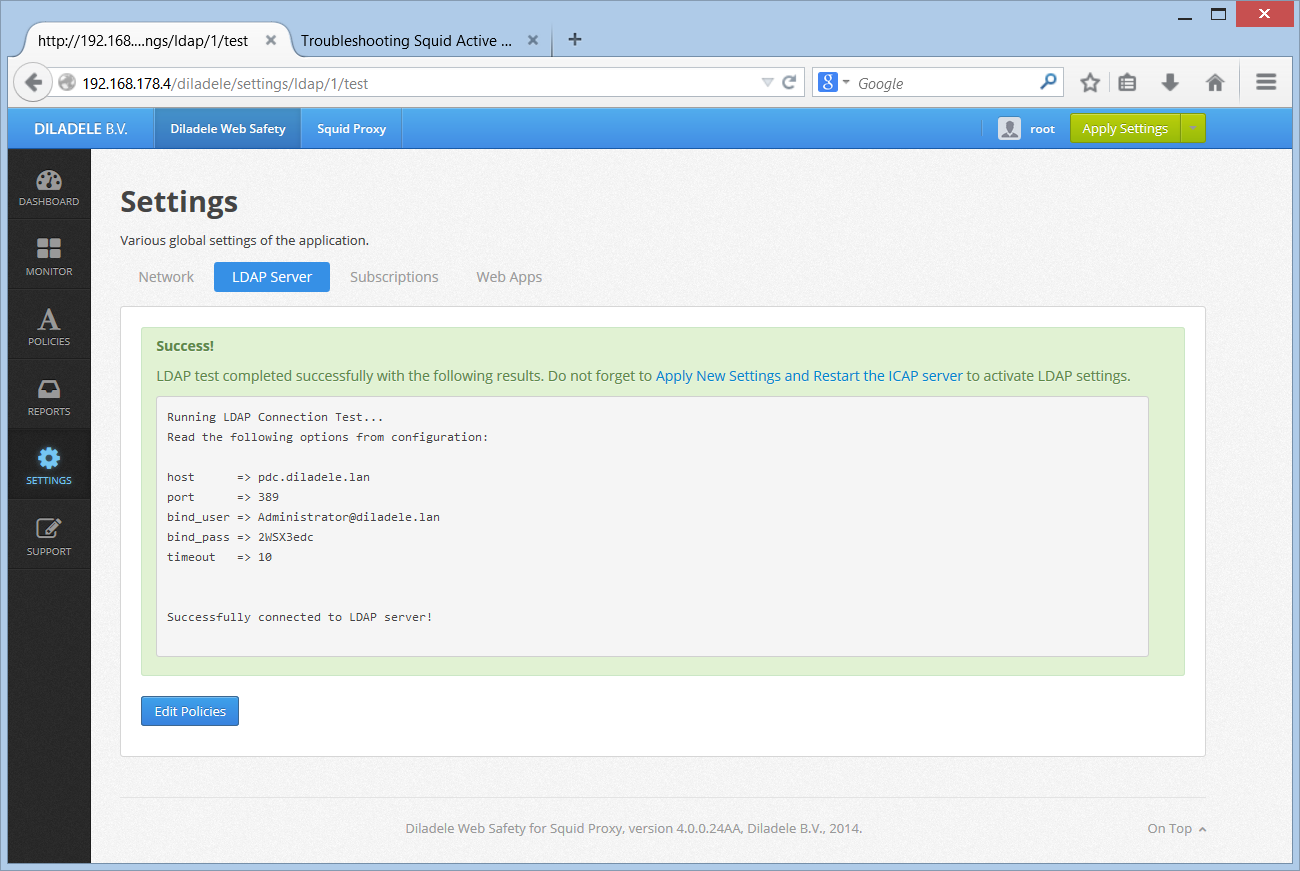
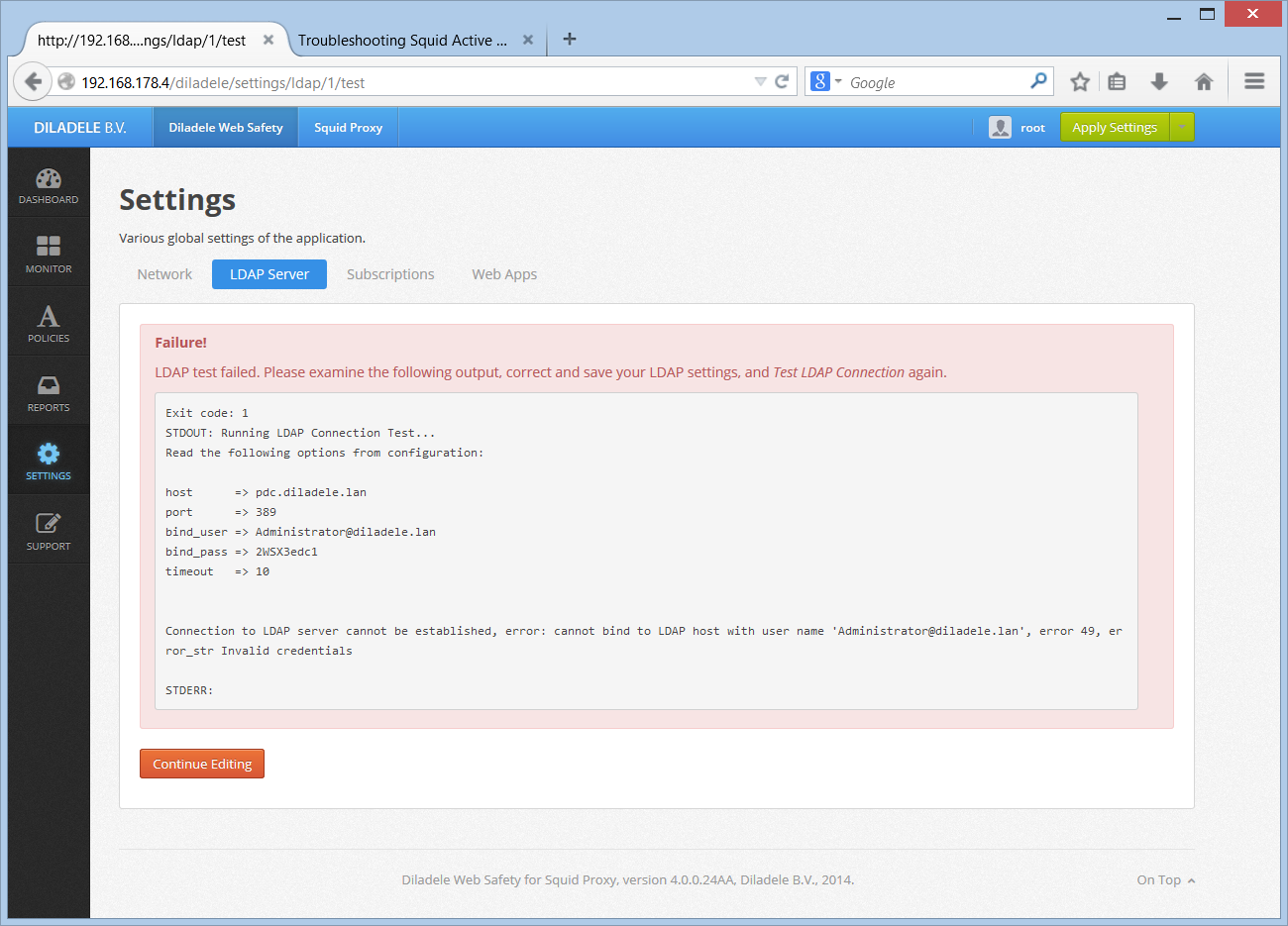
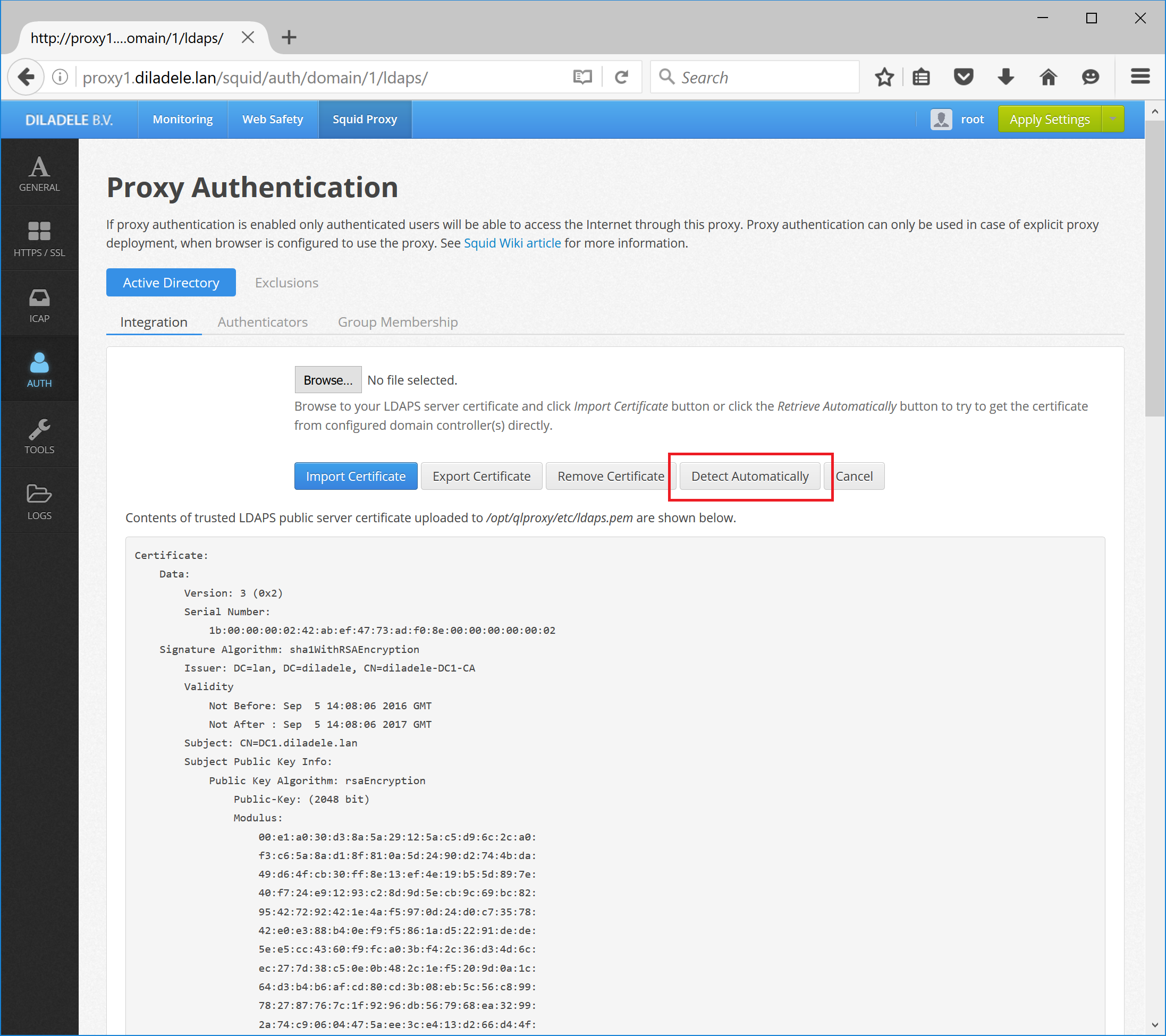
If you are using LDAPS connections check the server certificate is correctly visible in UI / Squid / Auth / LDAPS.
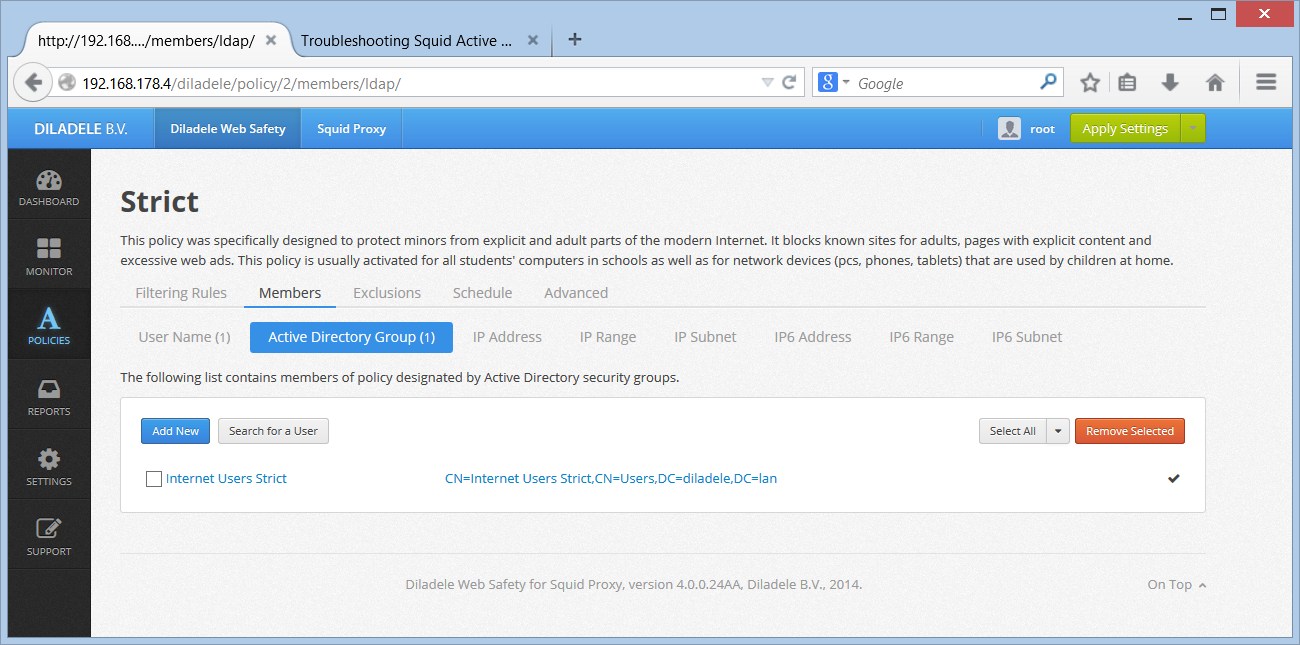
Open UI / Web Safety / Policies / Your Policy / Members / Active Directory Group and click the Search User button. Select the user which is definitely known to be in the target group and click the Search. Check the result of this command.
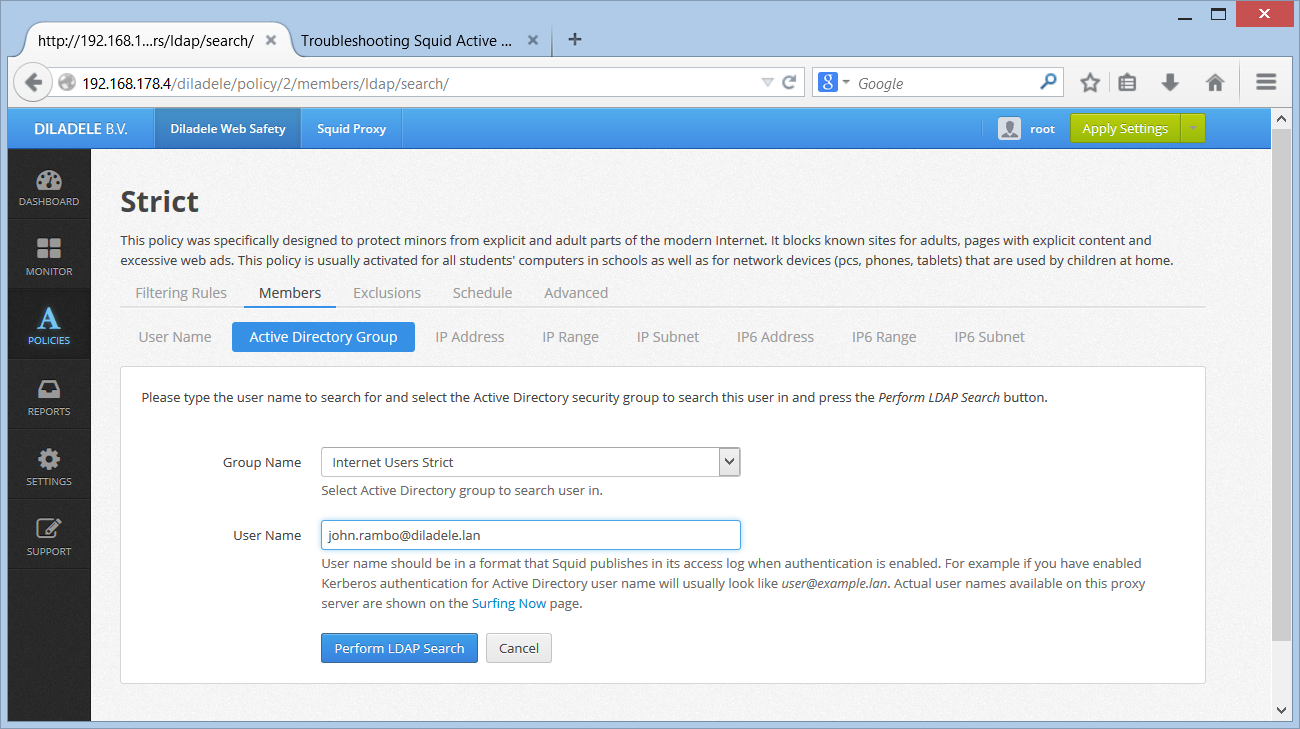
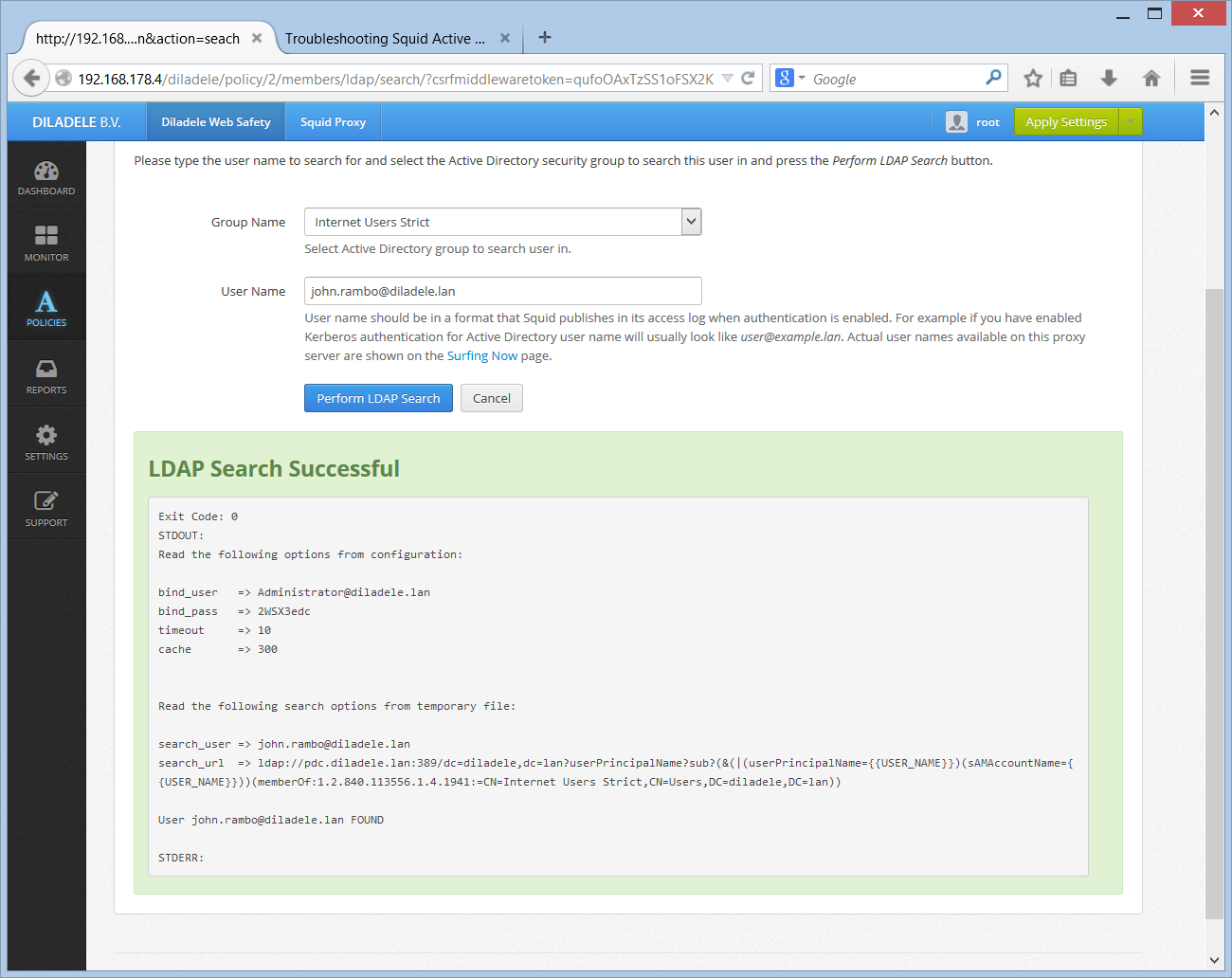
Check the timezone setting in your proxy box, including UI timezone setting as indicated in Step 2. Syncronize time.
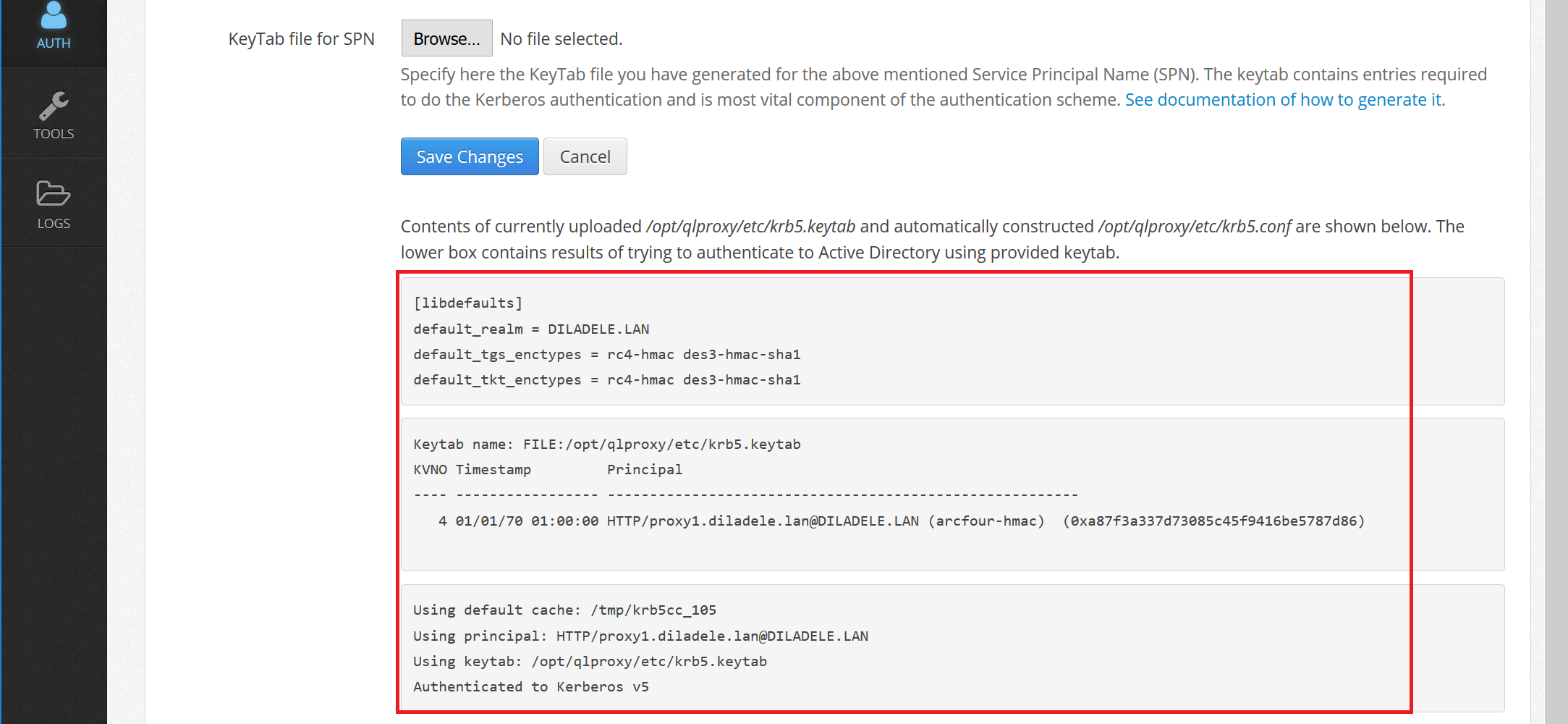
Check keytab verification steps are successful and no errors are shown in UI / Squid / Auth / Authenticators like shown on the following screenshots.