Configure Transparent Interception on Squid¶
As separate proxy box we will use the latest web filtering virtual appliance from https://www.diladele.com/download.html. This virtual appliance contains pre-configured recent version of Squid proxy coupled with Web Safety ICAP web filter. You can easily build the same appliance on the real hardware yourself. Installation scripts at https://github.com/diladele/websafety will help you along the way.
Step 1. Set the proxy IP address¶
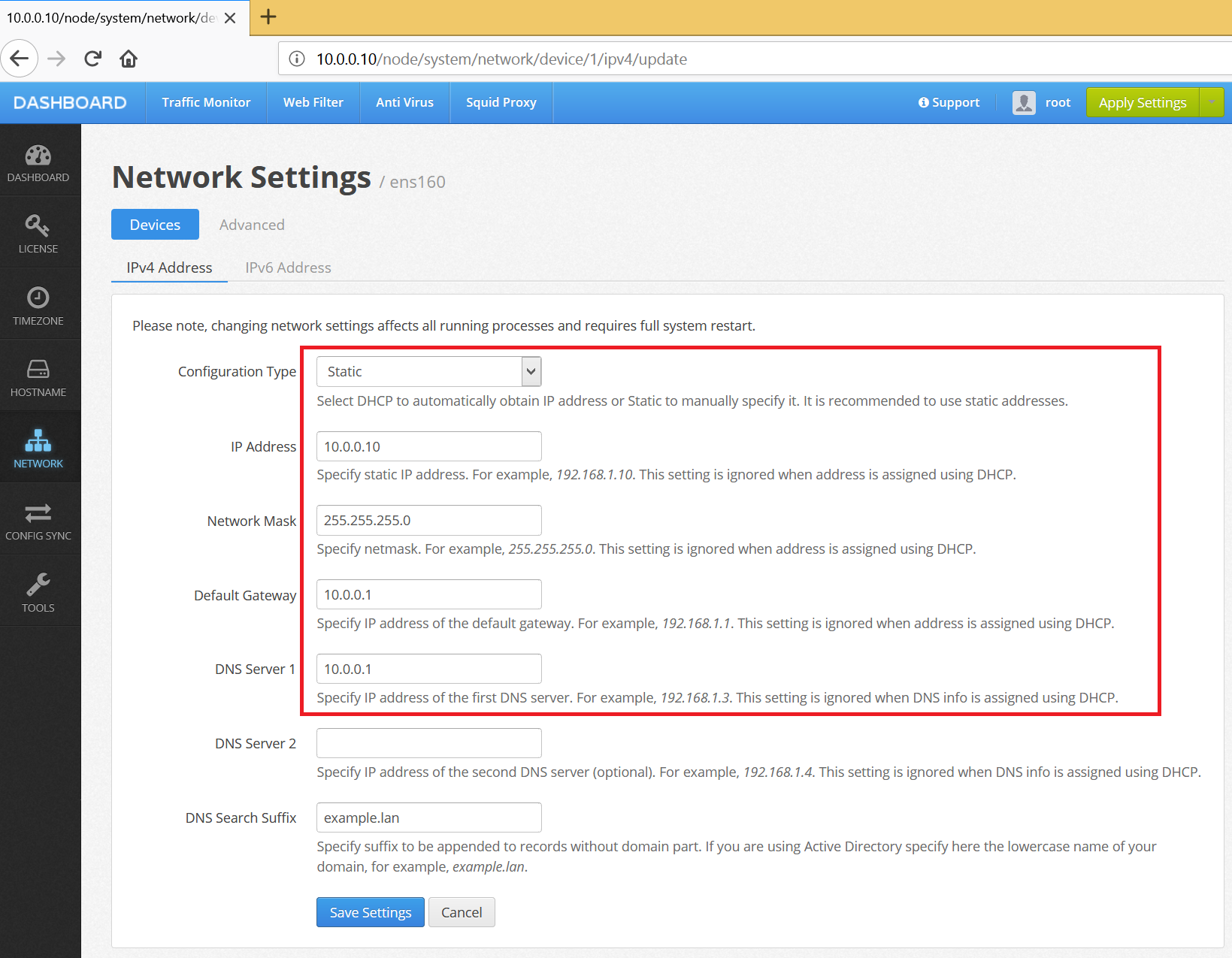
First you’d need to download the virtual appliance and run it in VMware vSphere of Microsoft Hyper-V. If you have built your web filtering appliance on real hardware, boot it up, open browser, navigate to UI / Dashboard / Network and set the static IP address for the ens160 network interface card. Do not forget to click Save Settings.
Now reboot the proxy from the root console. After it is back to life, ping our router to make sure the network is working.
root@proxy:~# ping 10.0.0.1
PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data.
64 bytes from 10.0.0.1: icmp_seq=1 ttl=64 time=0.255 ms
64 bytes from 10.0.0.1: icmp_seq=2 ttl=64 time=1.20 ms
64 bytes from 10.0.0.1: icmp_seq=3 ttl=64 time=0.400 ms
--- 10.0.0.1 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 0.255/0.619/1.204/0.418 ms
Step 2. Enable Gateway Mode¶
To make Squid listen on these transparently redirected ports, navigate to UI / Squid / Settings / Network and select Default Gateway Proxy mode as shown on the screenshot below. Click Save and Restart afterwards.
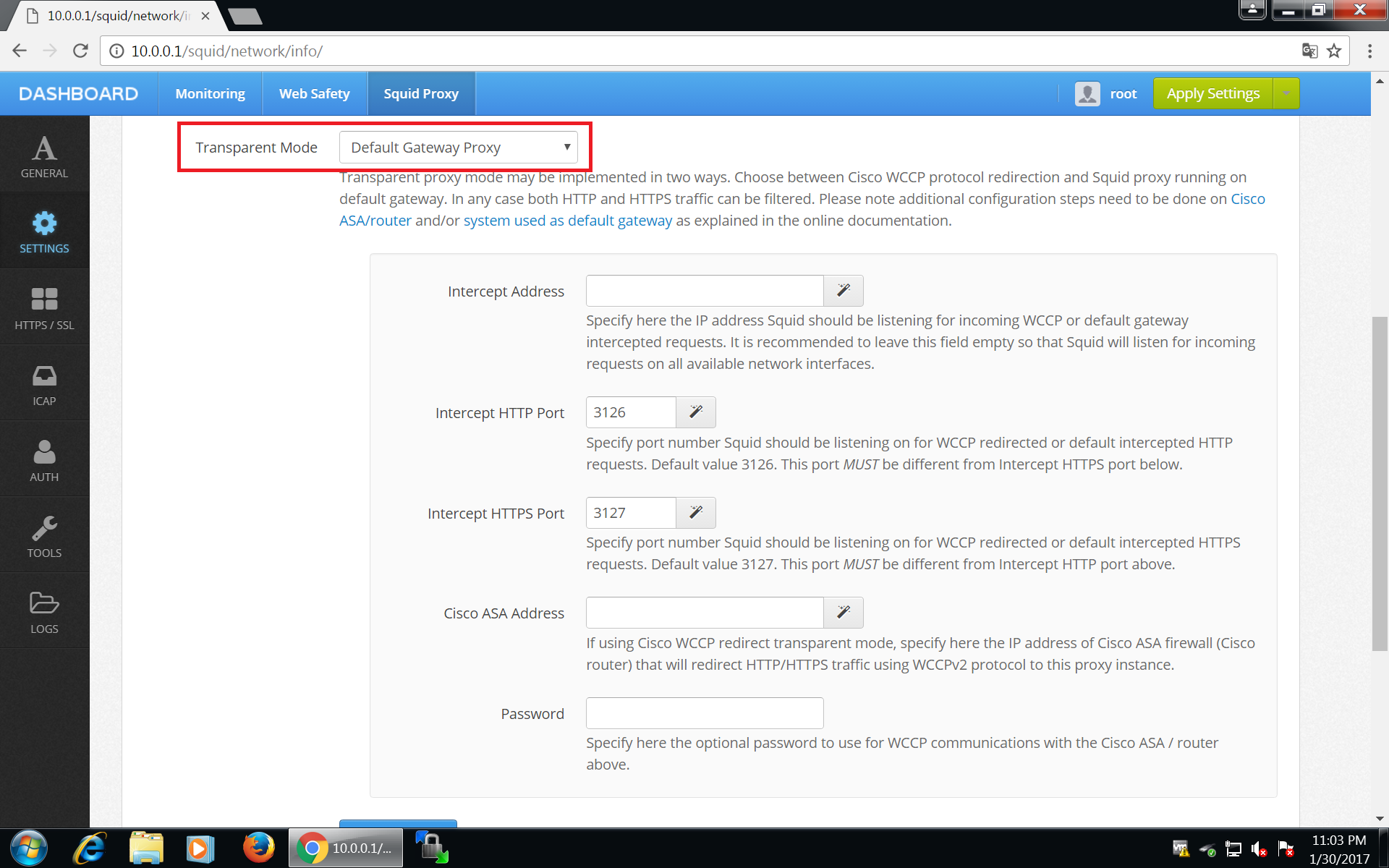
After clicking Save and Restart, UI will generate required http_port and https_port directives in /opt/websafety/etc/squid folder. These will look like the following.
# port configuration
http_port 3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB cert=/opt/websafety/etc/myca.pem
http_port 3126 intercept
https_port 3127 intercept ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB cert=/opt/websafety/etc/myca.pem
Note
Ports 3126 and 3128 are prefixed with http_port directive and port 3127 is prefixed with https_port directive!
Step 3. Redirect traffic to local Squid instance¶
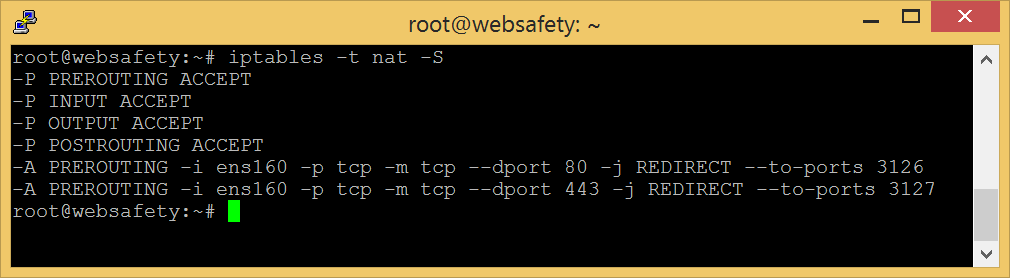
To redirect the incoming HTTP and HTTPS traffic to local instance of Squid proxy we need to add the following rules to the firewall on the proxy box (and NOT on your Debian 10/Ubuntu 16 router!!!). Please note, here HTTP traffic is redirected to http_port 3126 and HTTPS traffic is redirected to https_port 3127.
# redirect HTTP to locally installed Squid instance
iptables -t nat -A PREROUTING -i ens160 -p tcp --dport 80 -j REDIRECT --to-ports 3126
# redirect HTTPS to locally installed Squid instance
iptables -t nat -A PREROUTING -i ens160 -p tcp --dport 443 -j REDIRECT --to-ports 3127
To save configured iptables between reboots run the following command (you might need to install the iptables-persistent package by running apt-get install iptables-persistent).
netfilter-persistent save
Reboot your proxy box again and check the output of iptables -t nat -S command. It should look like: