How to fix X509_V_ERR_UNABLE_TO_GET_ISSUER_CERT_LOCALLY Squid error¶
Important
Web Safety 7.3+ allows you to fix this error automatically. You just need to navigate to UI / Squid / HTTPS tab and set the [X] Try to automatically download missing intermediate HTTPS certificates checkbox. Consider reading the article anyway - just to understand why this error occurs in the first place.
HTTPS filtering is a must for any network admin these days and if you implement HTTPS filtering using SSL Bumped Squid you have surely seen the X509_V_ERR_UNABLE_TO_GET_ISSUER_CERT_LOCALLY error.
The main reason for this error is very simple – one (or some) certificates presented by the remote HTTPS site are not present in the certificate store of Squid proxy server. Because of that Squid cannot generate mimicked SSL certificate required to perform HTTPS filtering.
Let’s take https://incomplete-chain.badssl.com for example. If you access it directly (FF or Chrome or even IE) you will not see any errors. If you do the same through HTTPS filtering proxy the following error page will be appear in the browser.
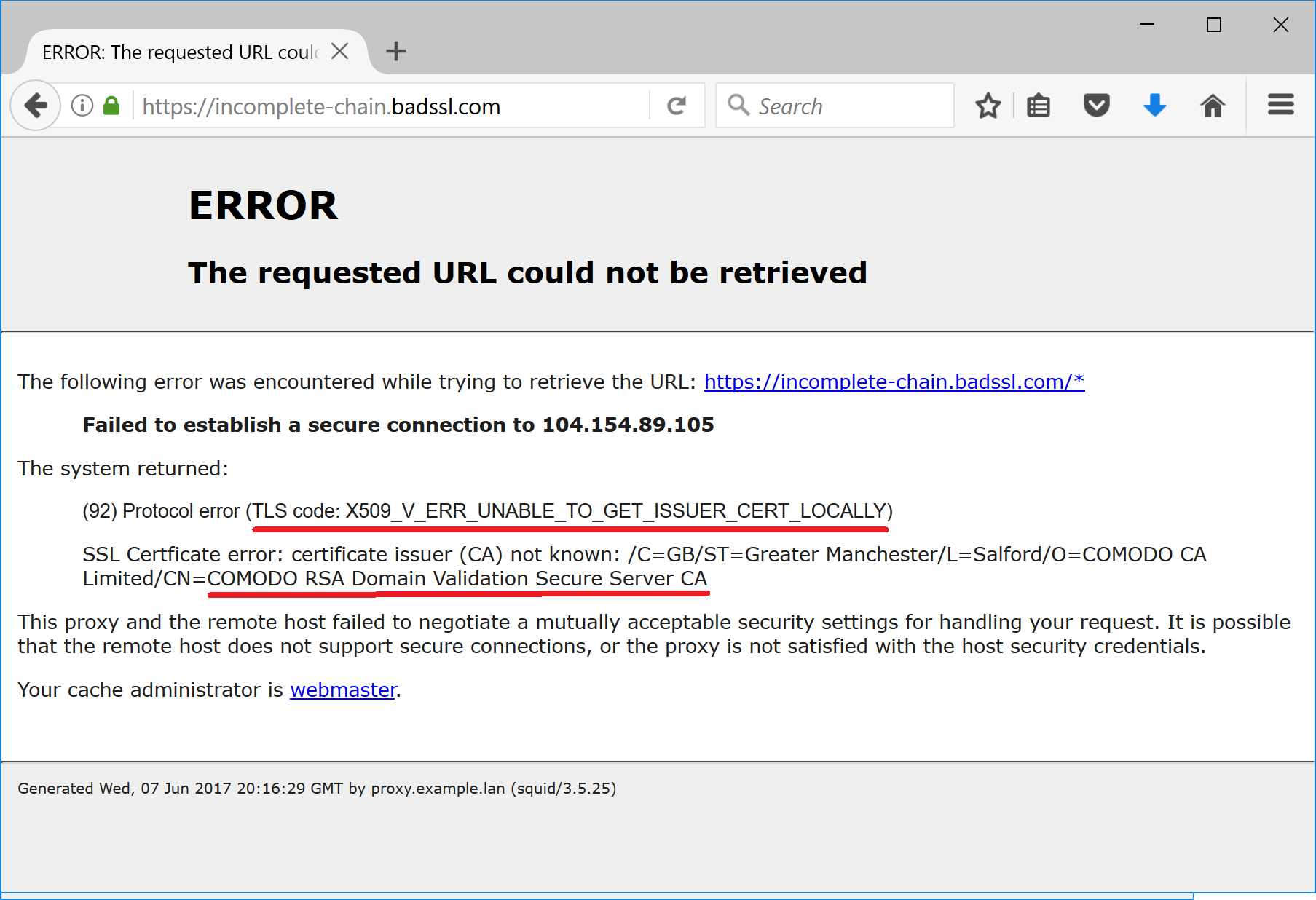
If you take a closer look at the error page then it becomes clear that the following certificate authority is missing:
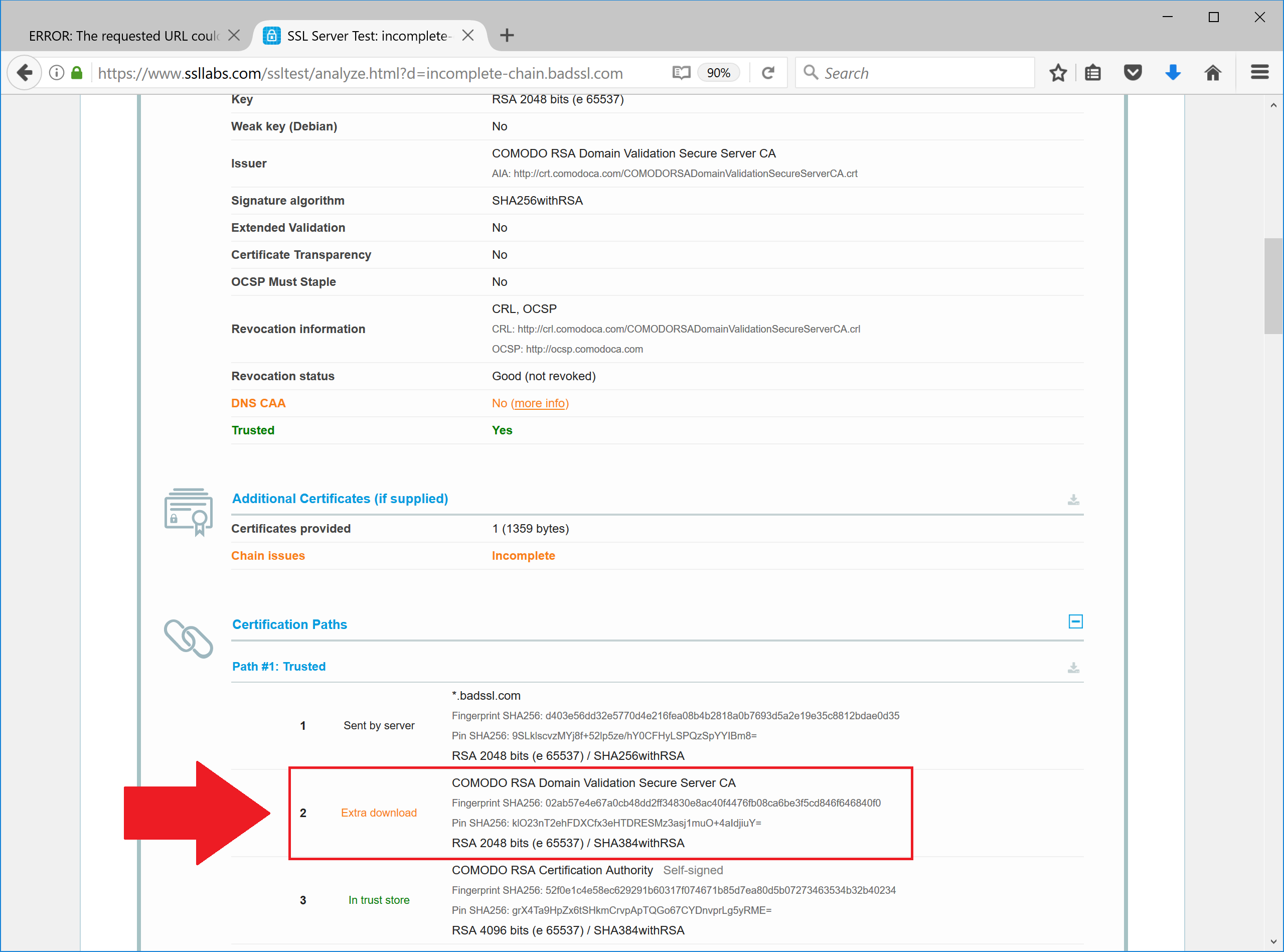
COMODO RSA Domain Validation Secure Server CA
It is missing because the administrator of the site incomplete-chain.badssl.com has configured the web server incorrectly - according to current web standards the server MUST present all chain of certificates up to (but not including) the root certificate. In this case only the site certificate is presented by the web server and other certificates in the chain are left away.
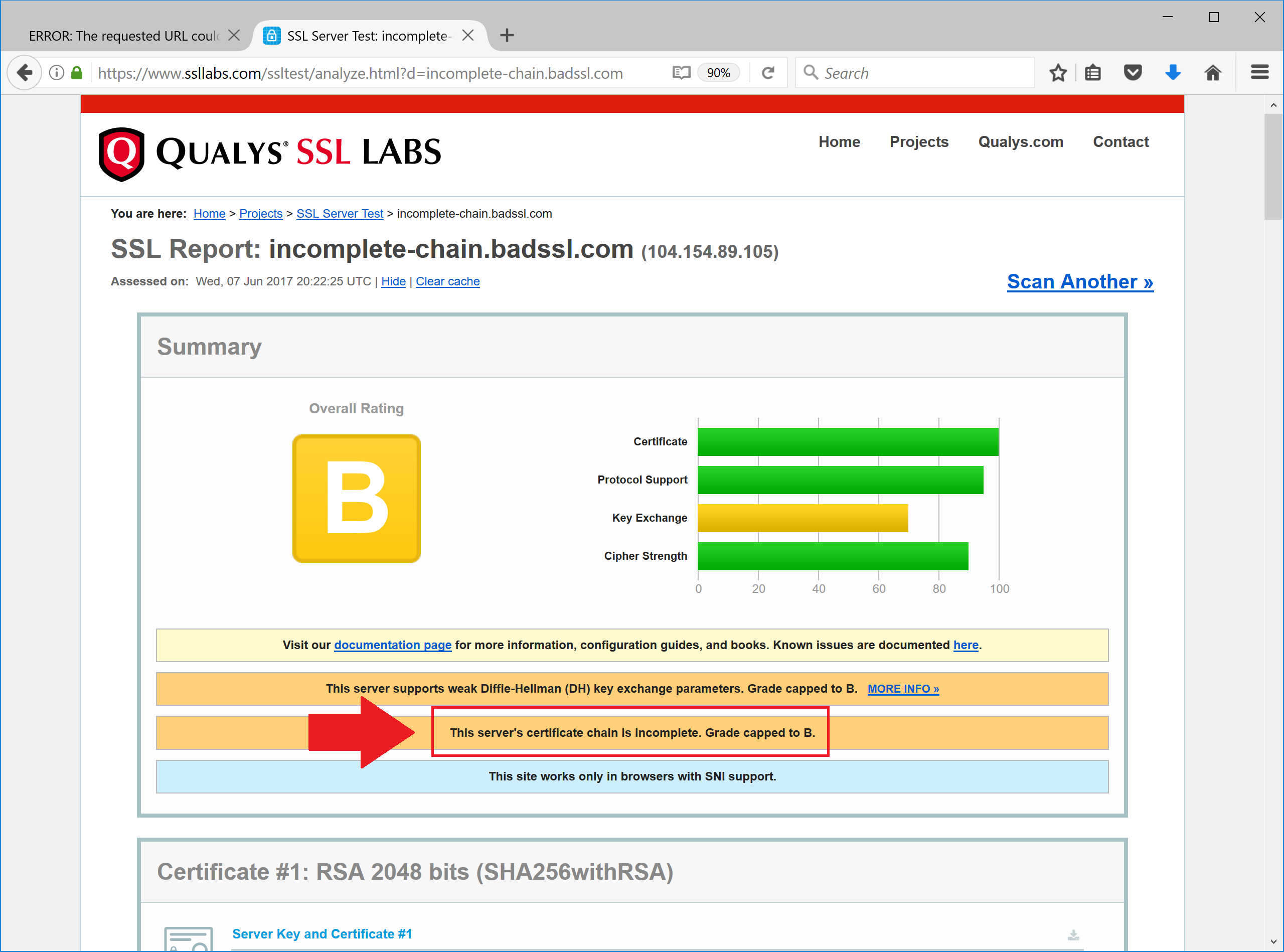
To prove that we can go to online SSL Server Site Check Tool at https://www.ssllabs.com/ssltest/index.html. Type the incomplete-chain.badssl.com into the search field and click Submit. The tool will respond with results showing “Incomplete Chain” error as inidicated on the following screenshot.
Scroll the result page down and see what intermediate certificate is missing from the chain.
Note
This page explains more about what intermediate certificates are https://www.godaddy.com/help/what-is-an-intermediate-certificate-868.
To fix this X509_V_ERR_UNABLE_TO_GET_ISSUER_CERT_LOCALLY we must manually download the missing certificate and install it into the system.
Which Certificate to Download?¶
To find out which missing certificate to download, expand the incomplete chain button from SSL Labs result page, and manually take only the missing certificate from the output. Save its contents as a missing.pem file.
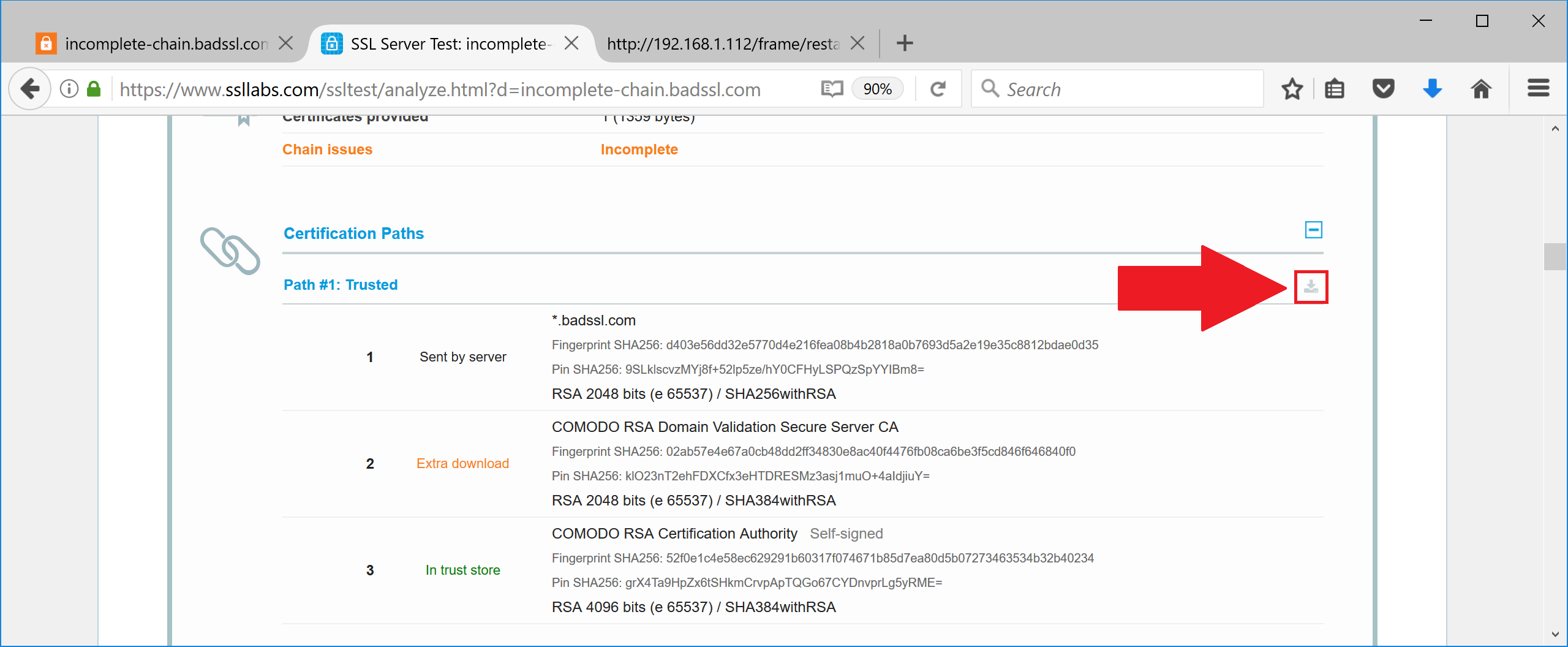
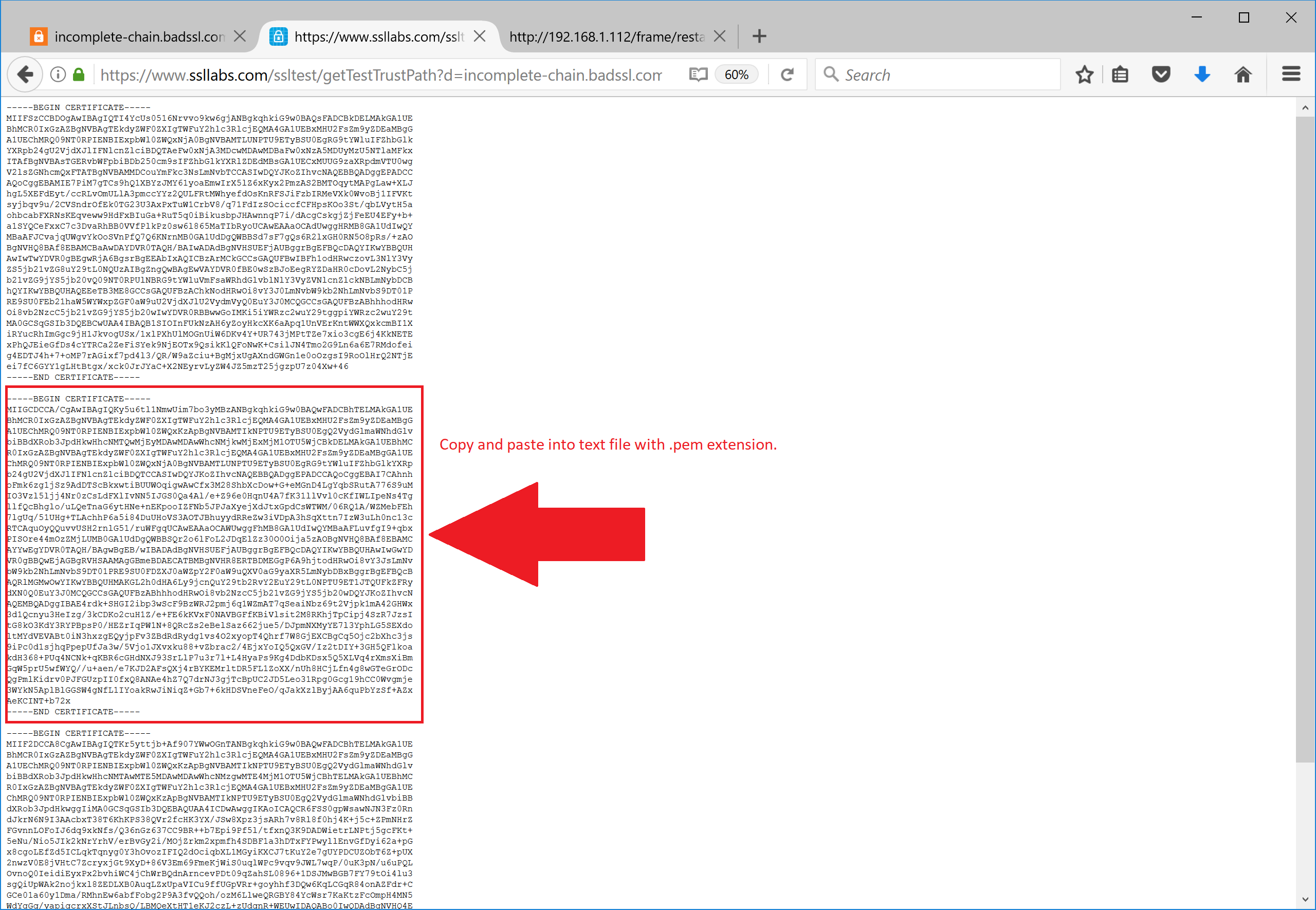
Now we need to add it to the proxy system. There are two possible ways to do it.
Way 1. Add Missing Certificate to Squid (Recommended)¶
Web Safety has the ability to add the missing certificates to the Squid intermediate certificate storage. Navigate to UI / Squid / HTTPS / Missing Certificates and upload the PEM file for the certificate as inidicated on the following screenshots.
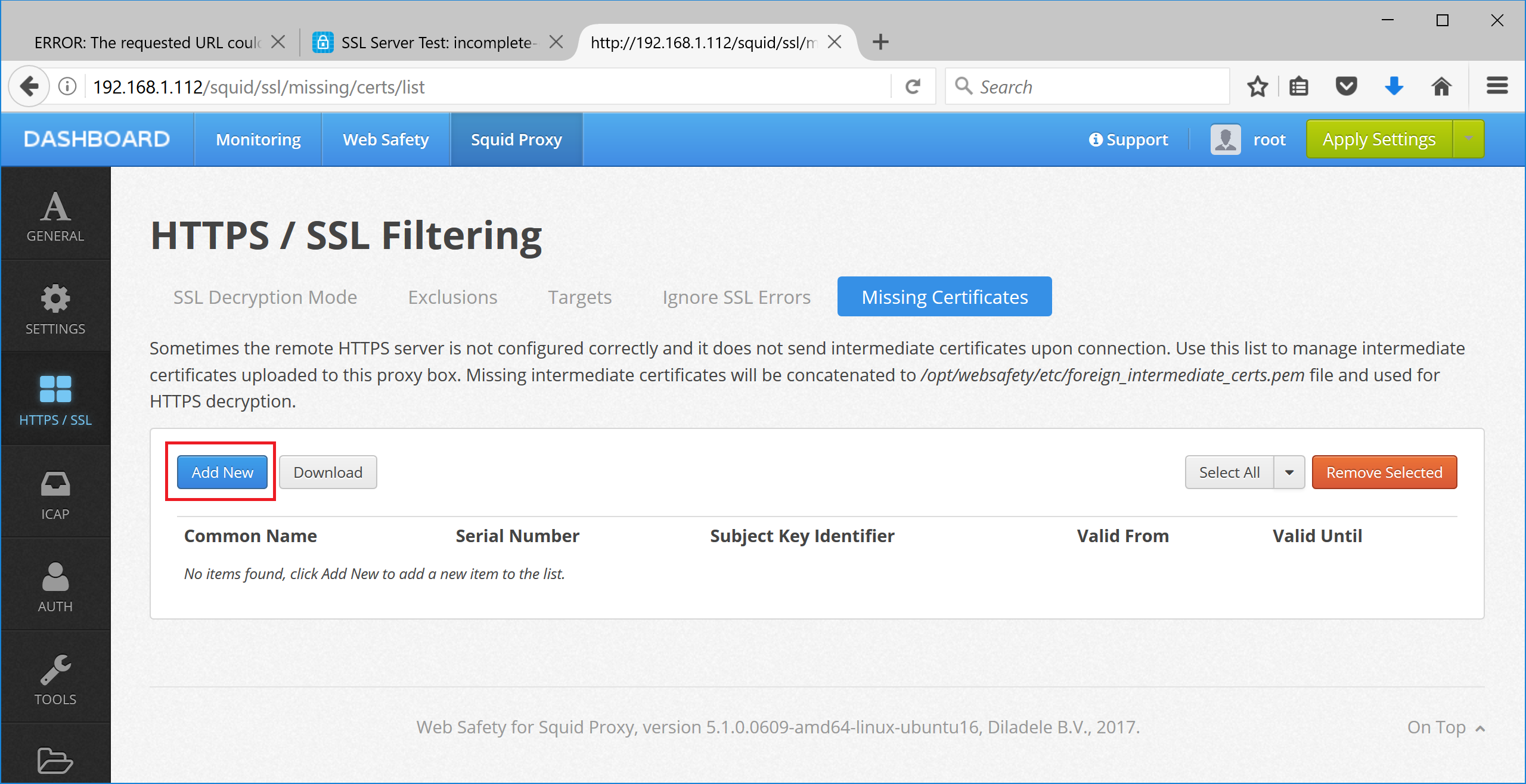
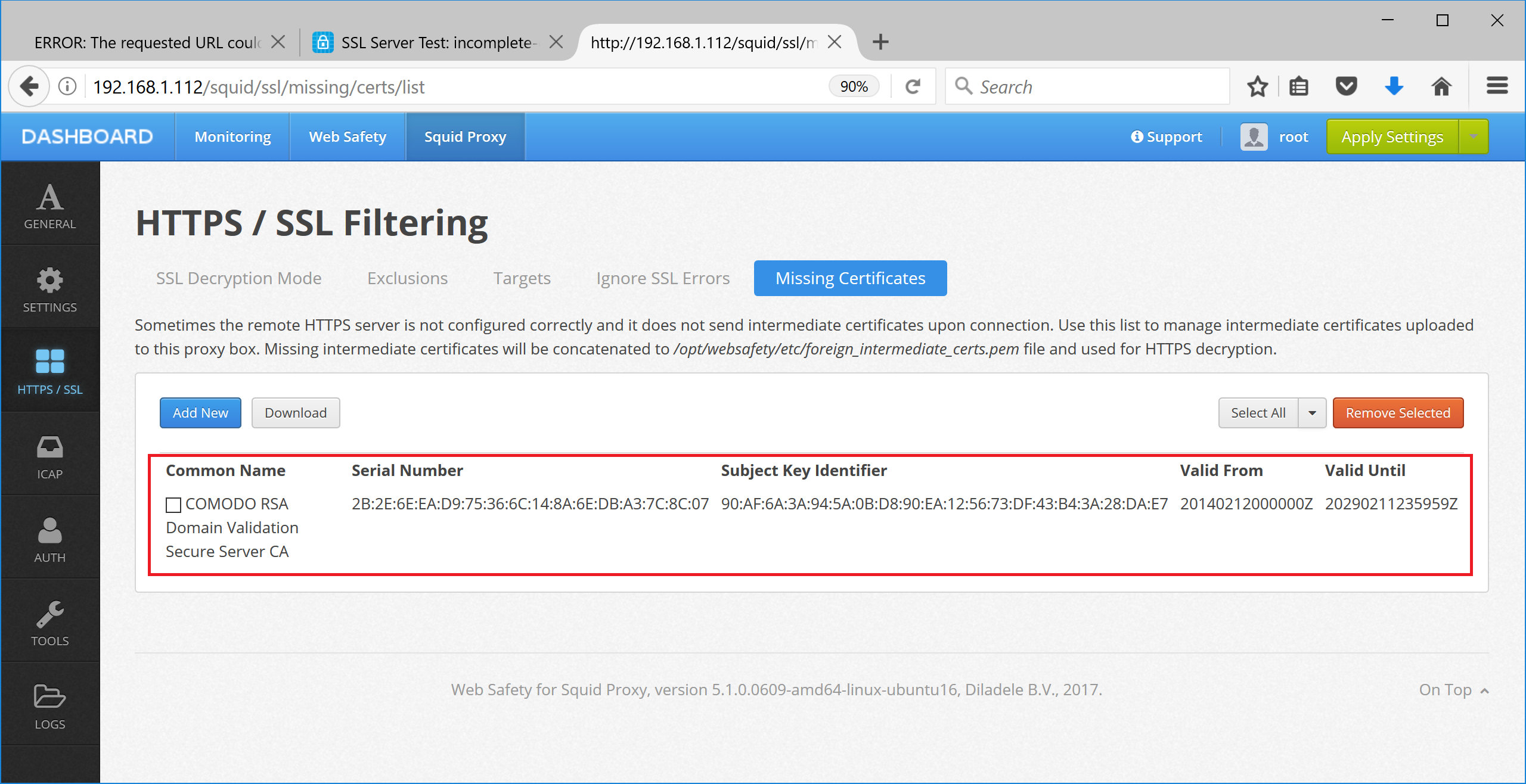
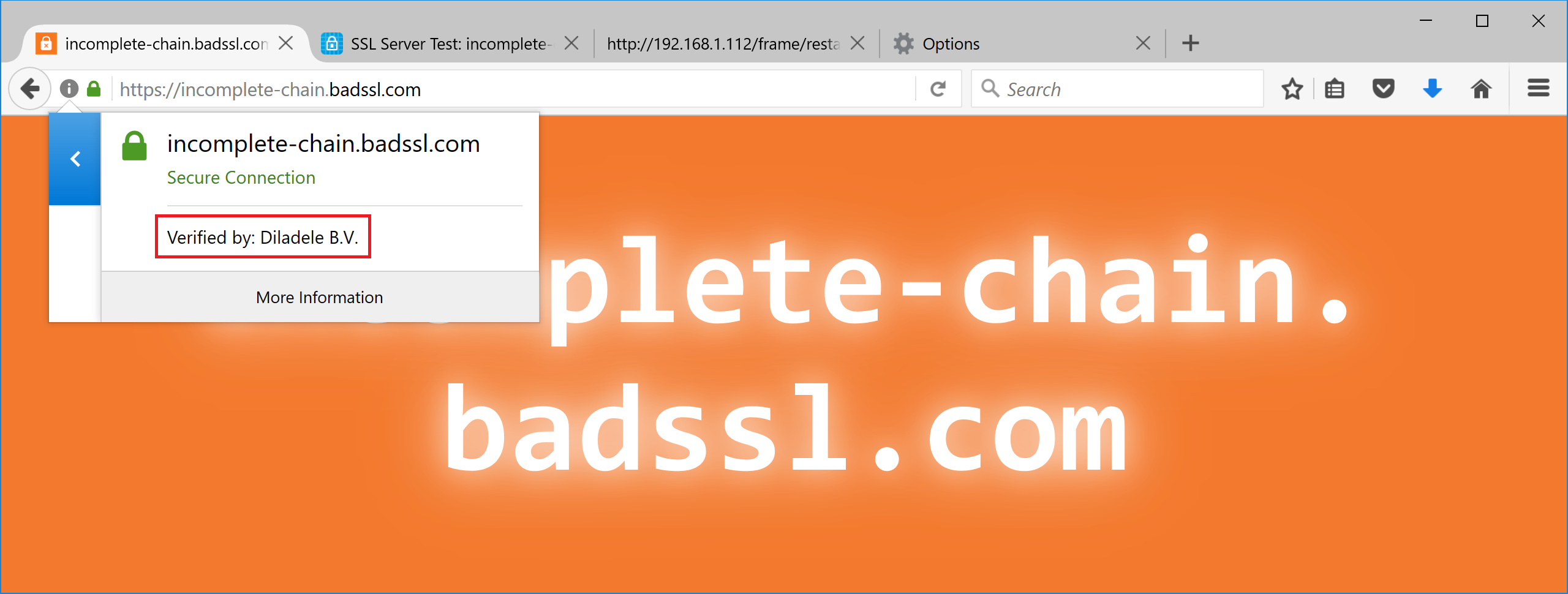
Click Save and Restart to load the storage into Squid. After that access to https://incomplete-chain.badssl.com will be successful.
Way 2. Install Missing Certificate into System Certificate Storage¶
It is also possible to add this certificate to operating system’s certificate storage. This method is generally not recommended because adding an intermediate certificate to the root certificate storage makes is “globally trusted” and this usually too much for the purposes of HTTPS filtering.
Install Intermediate SSL Certificate on CentOS 7¶
Ensure intermediate certificate ends with .pem (this is required for CentOS 7).
Open root terminal and copy the certificate into
/etc/pki/ca-trust/source/anchors/folder.Run
update-ca-trustcommand to rebuild the system certificate bundle. It should finish without any output.Restart Squid by running
systemctl restart squid.
Note
To remove this manually installed intermediate certificate from the certificate bundle in CentOS 7, remove the certificate file from /etc/pki/ca-trust/source/anchors and run the update-ca-trust again. Do not forget to restart Squid!
Install Intermediate SSL Certificate on Ubuntu (Debian)¶
Open root terminal and copy the certificate into
/usr/local/share/ca-certificates/crt. Please note, unlike in CentOS 7, the file extension needs to be crt!Run
sudo update-ca-certificatescommand to rebuild the system certificate store.Restart Squid by running
systemctl restart squid.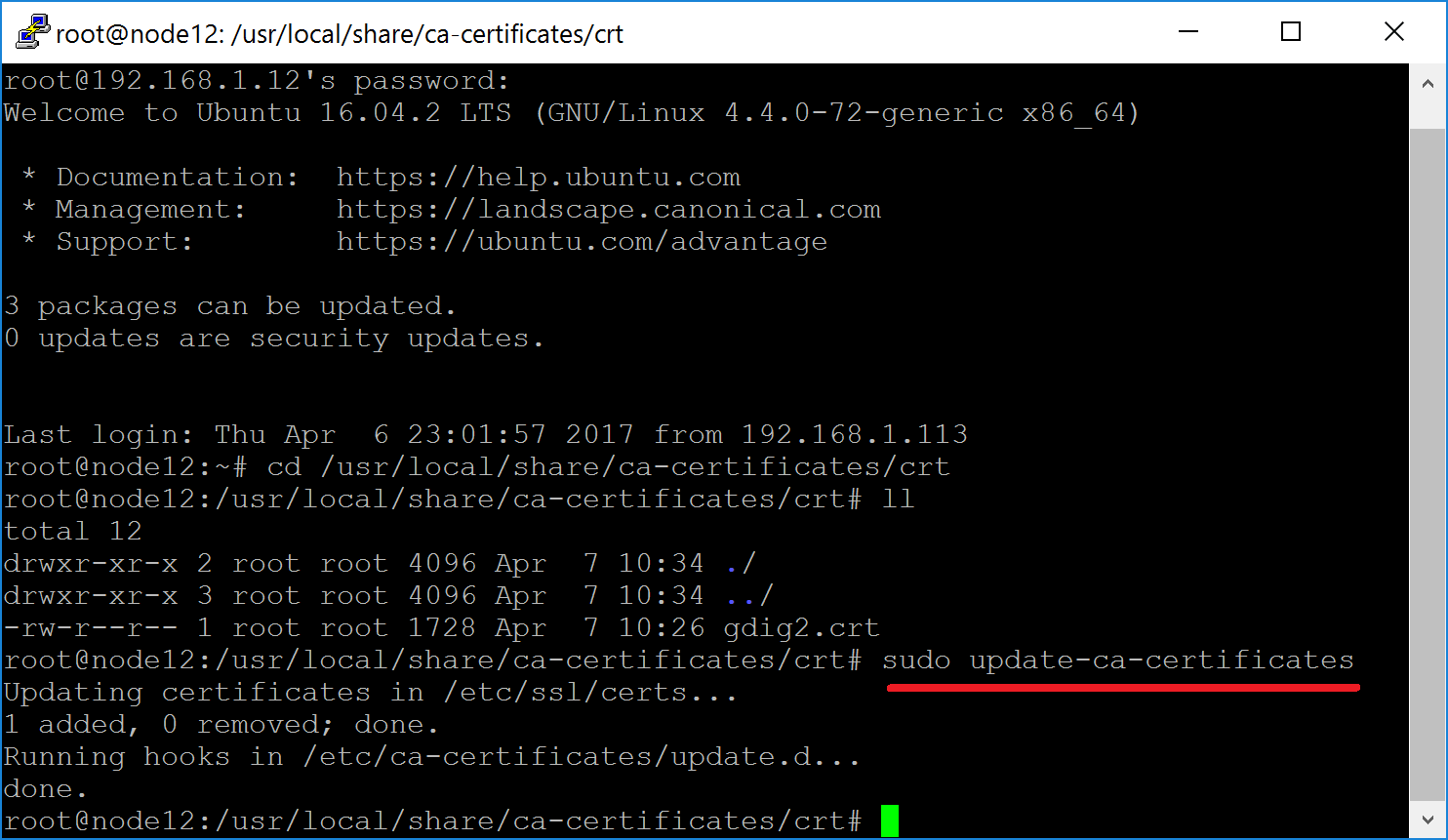
After that access to https://incomplete-chain.badssl.com will be successful.
Note
To remove this manually installed intermediate certificate from the certificate bundle, remove this certificate from /usr/local/share/ca-certificates, run sudo update-ca-certificates and finally remove all dangling links to non existing certificate in /etc/ssl/certs folder.