How to allow SSH/FTP connections through proxy?¶
Sometimes, it is required to allow SSH or FTP connections through the proxy. The following steps show required actions to do it. Please note the following instructions apply only to Web Safety version 8.0 and up.
Step 1. Define ACLs¶
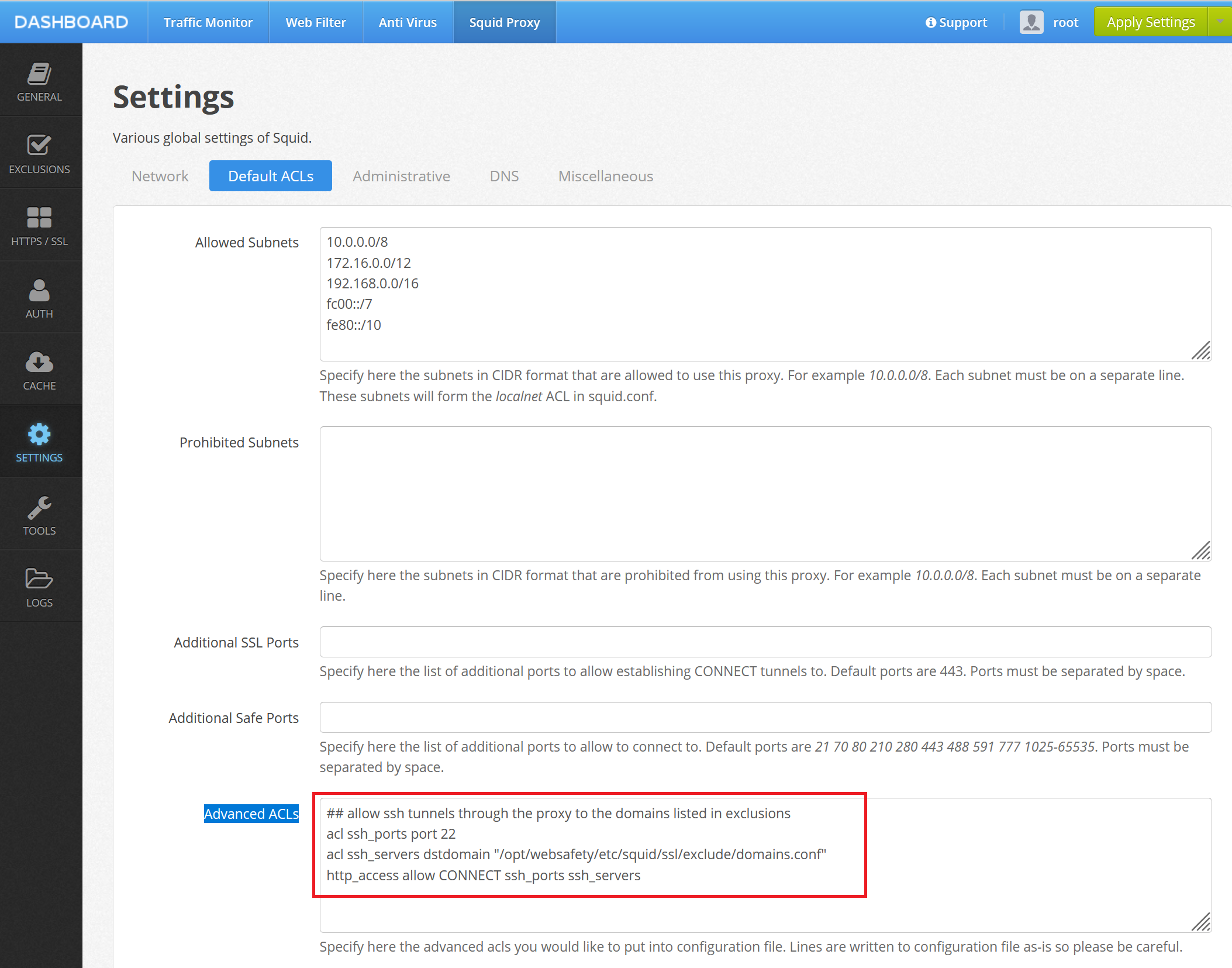
In Admin UI / Squid Proxy / Settings / Default ACLs add the following lines to the “Advanced ACLs” text field as shown on the following screenshot. These ACLs tell the proxy to allow SSH/FTP access to the selected domains and ports 22 or 21.
## add the following to allow SSH tunnels to the domains listed in HTTPS exclusions
acl ssh_ports port 22
acl ssh_servers dstdomain "/opt/websafety/etc/squid/ssl/exclude/domains.conf"
http_access allow CONNECT ssh_ports ssh_servers
## add the following to allow FTP tunnels to the domains listed in HTTPS exclusions
acl ftp_ports port 21 1025-65535
acl ftp_servers dstdomain "/opt/websafety/etc/squid/ssl/exclude/domains.conf"
http_access allow CONNECT ftp_ports ftp_servers
Step 2. Add Exclusion¶
Next step is to add the domain name and IP address that domain name resolves to to the Admin UI / Squid Proxy / Exclusions. Note we are adding both domain name and its IP address. This is because the client software (FTP mostly) will establish tunnels to the remote server first by domain name and later by IP address. This might not be required for the SSH access but it is definitely required for FTP.
Step 3. Save and Restart¶
Finally, click Save and Restart from Admin UI and try using your application to access the desired domain by SSH and/or FTP.
Important
If you need to allow the same functionality in Web Safety 6 or 7 you would need to manually move the order of Peek-And-Splice directions in /opt/websafety-ui/var/console/squid/templates/squid/conf/ssl.conf template file as shown on the following patch.
--- ssl.conf.original 2022-01-13 21:06:41.918086001 +0100
+++ ssl.conf 2022-01-13 21:07:15.386342863 +0100
@@ -292,11 +292,6 @@
# skip SSL bump in both all and targeted mode
ssl_bump splice ssl_skip_bump
-# peek at SNI the client sent to us
-ssl_bump peek step1 all
-
-# force bump in both all and targeted mode
-ssl_bump bump ssl_force_bump
# exclude from decryption all domains and ips that admin configured
ssl_bump splice ssl_exclude_domains
@@ -305,6 +300,12 @@
# advanced exclude acls
include "/opt/websafety/etc/squid/ssl/exclude/advanced.conf"
+# peek at SNI the client sent to us
+ssl_bump peek step1 all
+
+# force bump in both all and targeted mode
+ssl_bump bump ssl_force_bump
+
# now see what SSL filtering mode we are in
{% if bumpmode.value > 0 %}