Using Subordinate CA for HTTPS Decryption in Active Directory Integrated Squid¶
Warning
In order to use Subordinate CA for HTTPS filtering on Squid proxy (SSL Bump) you need to migrate your PKI infrastructure to SHA256 algorithm. This must be done because of SHA1 sunsetting in all major browsers as explained in https://security.googleblog.com/2014/09/gradually-sunsetting-sha-1.html. Failure to do so will result into Your connection is not secure message after you enable HTTPS decryption.
The following articles may prove to be helpful:
Generate CSR on Squid¶
Login to your proxy box (using ssh or console) and run the following commands. These are needed to generate the CSR request that will later be signed by your Enterprise CA. Adjust the subj fields as needed.
openssl req -nodes -newkey rsa:4096 -keyout subca.key -out subca.csr -subj "/C=NL/ST=Noord-Holland/O=Example Ltd./OU=IT/CN=proxy.example.lan/emailAddress=support@example.lan"
Sign CSR by Enterprise CA¶
Copy the subca.csr to some folder on the server that has Active Directory Certification Services role installed (your Enterprise CA), open command prompt, change to that folder and run the following commands.
certreq.exe -submit -attrib "CertificateTemplate:SubCA" subca.csr
This command will show a series of windows that you need to click through according to the following screenshots.
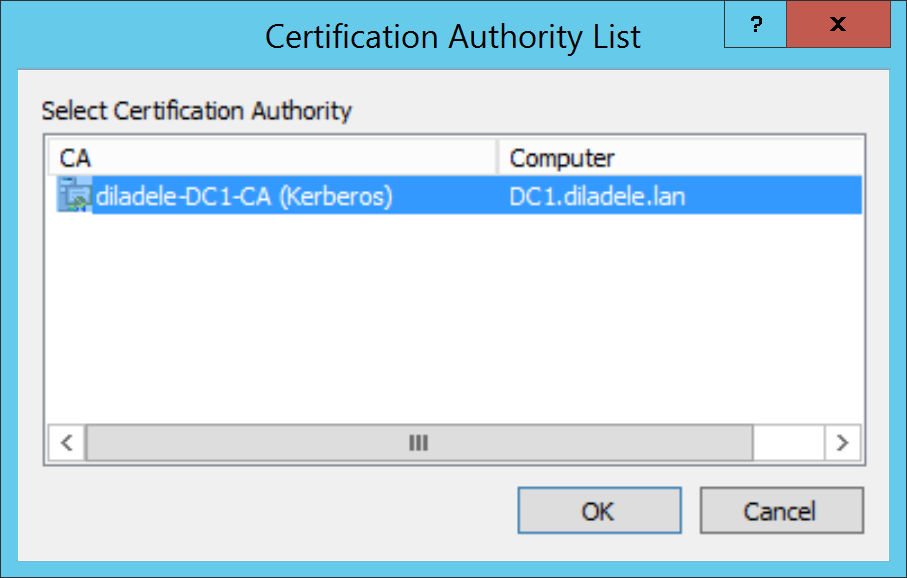
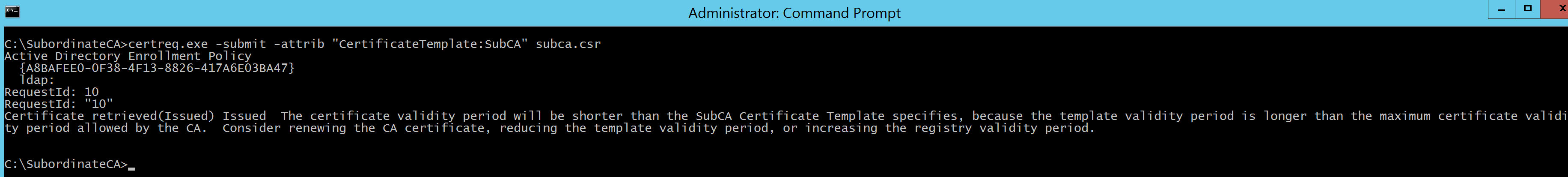
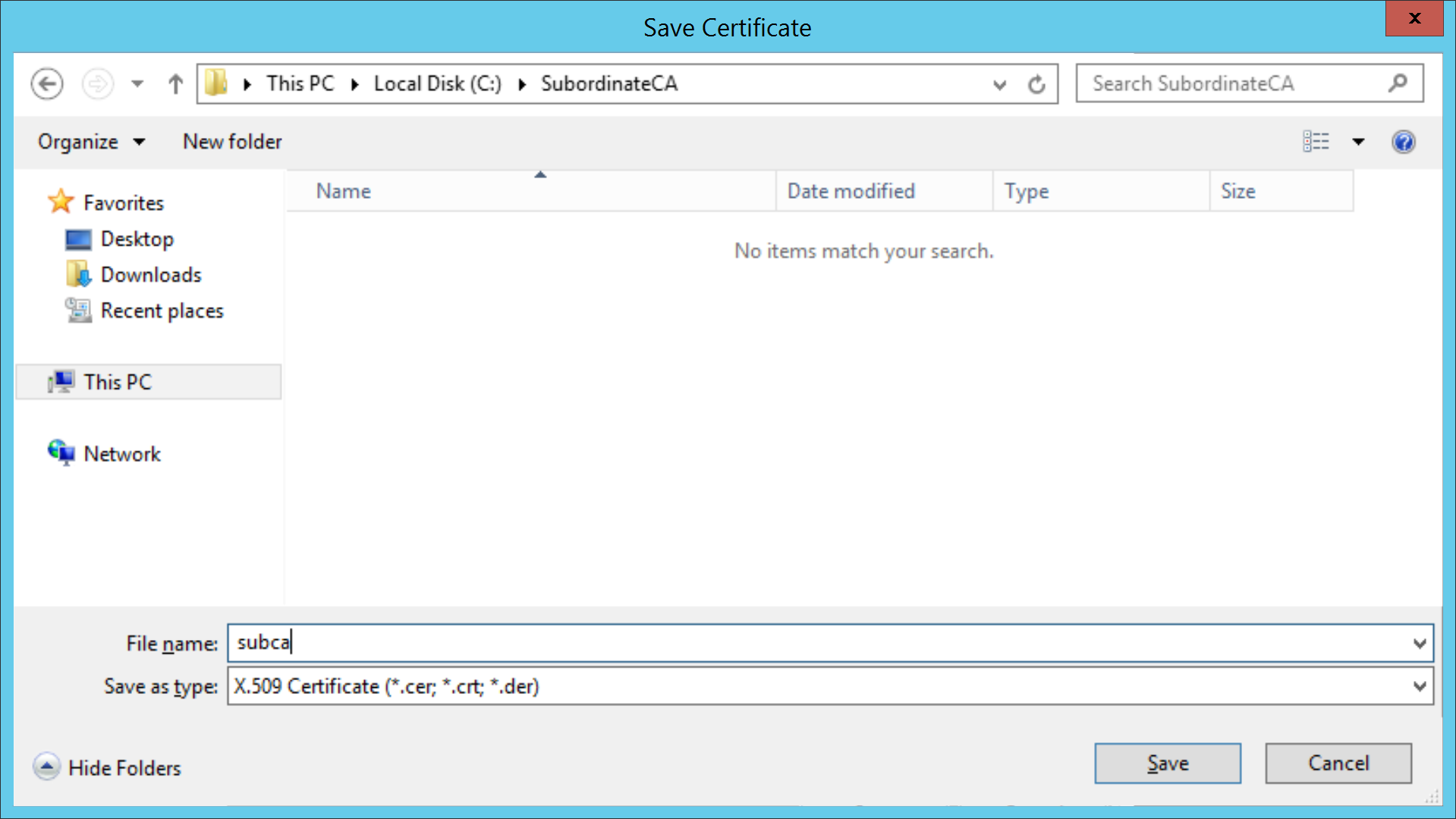
Install Subordinate CA on Squid¶
Now copy the subca.cer certificate back to your proxy box. Run the following commands to cat the subca.key and subca.cer together to make subca.pem file.
cat subca.key subca.cer > subca.pem
Upload the subca.pem to Web Safety / Squid Proxy / HTTPS / Upload New Certificate as shown on the following screenshots.
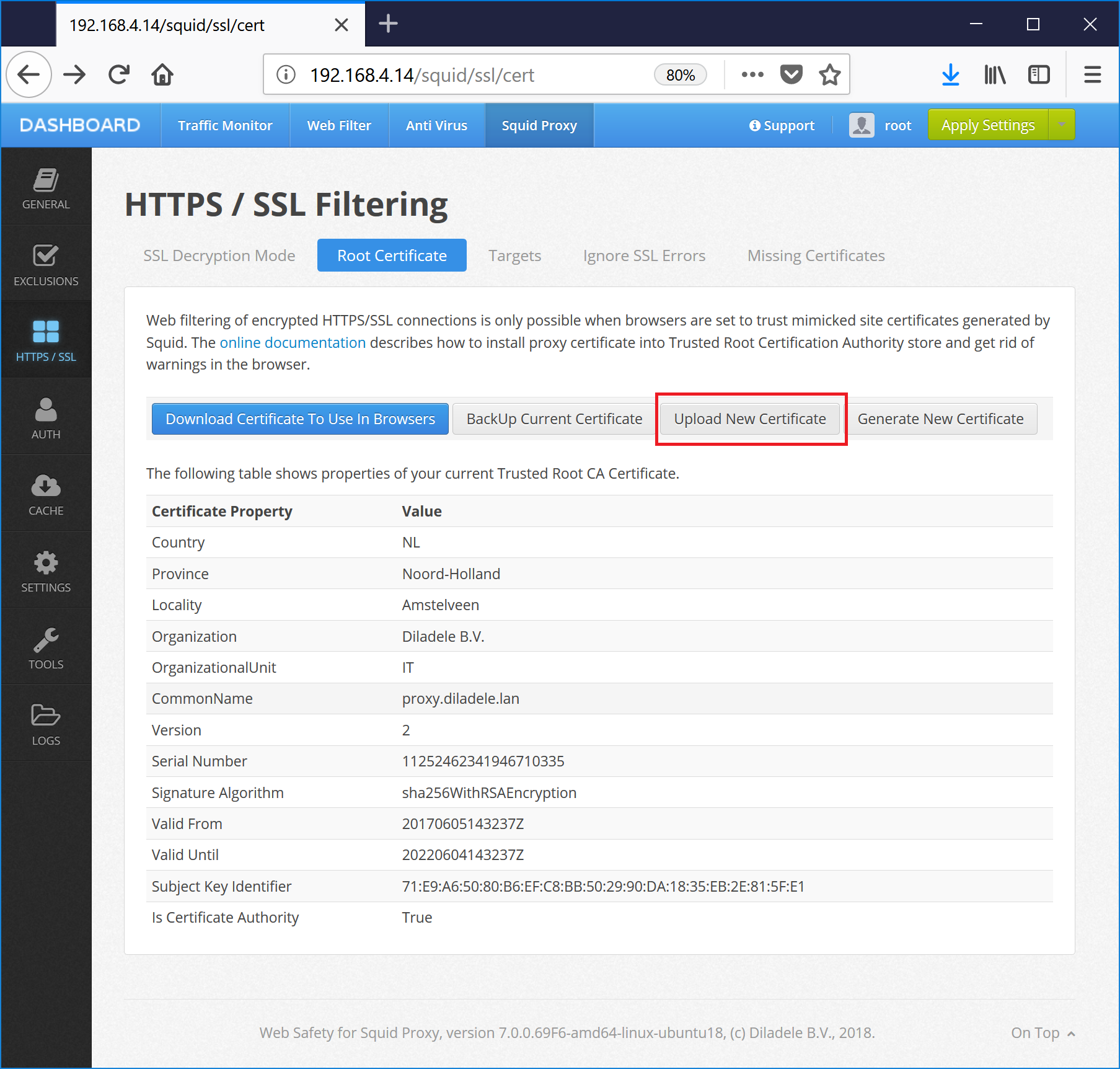
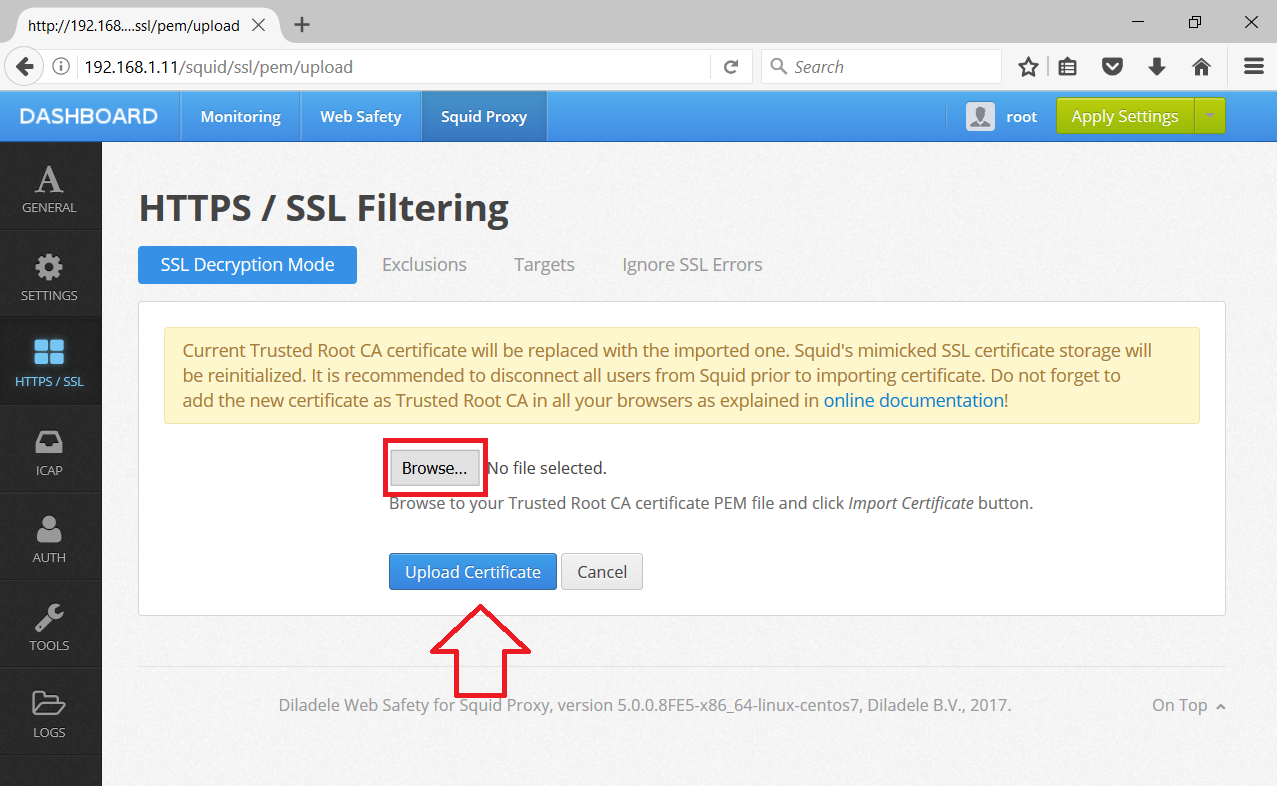
Click Save and Restart and navigate to some HTTPS site, for example https://www.google.com on Active Directory joined machine where NO PROXY ROOT CA CERTIFICATES were installed previously. The following screenshots show that HTTPS decryption now works correctly in Internet Explorer and Chrome.
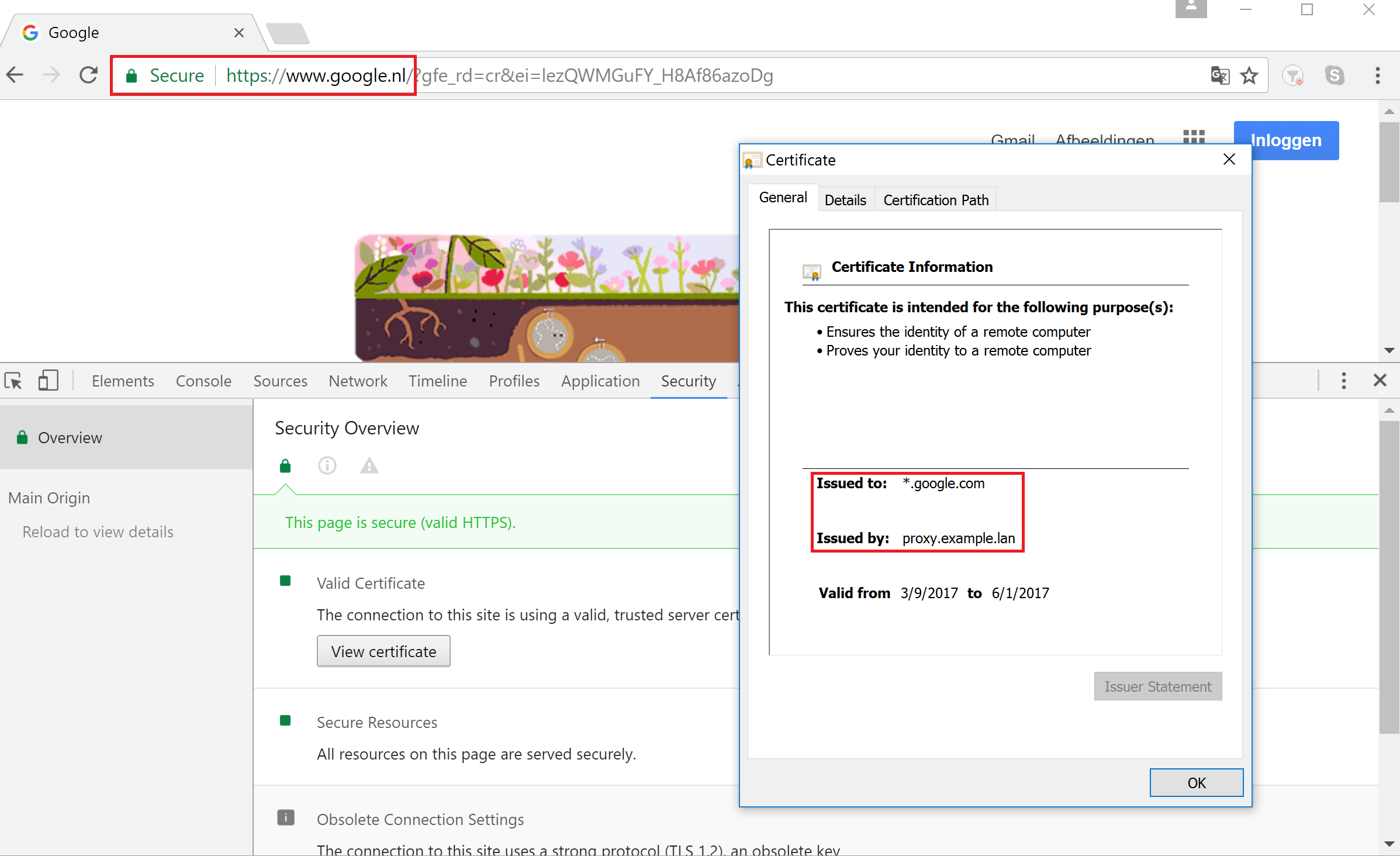
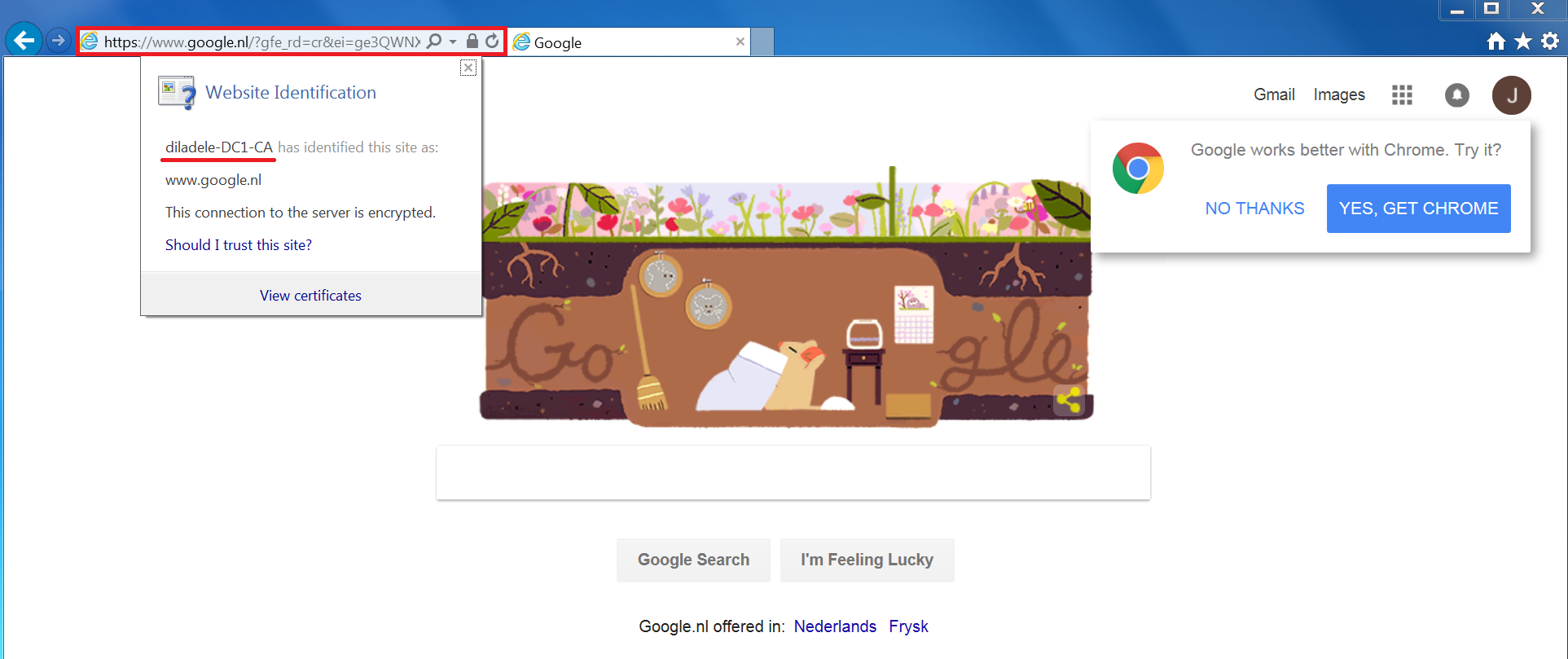
Note
This will not work for Firefox as it uses its own certificate storage. You need to manually install Enterprise Root CA into that storage too.