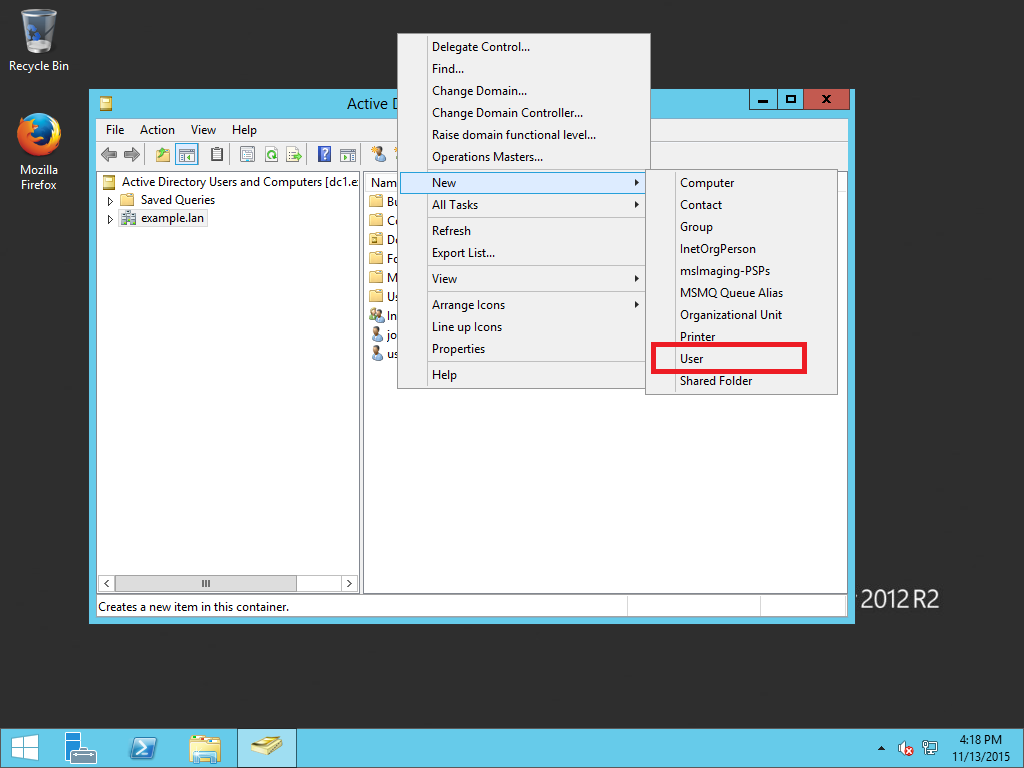
Step 3. Create User for Kerberos and LDAP authentication¶
In order to be able to authenticate domain users using Kerberos protocol and perform LDAP group lookups Web Safety needs a designated user account. The following screenshots show how to create such a user and set his properties.
Note
Some tutorials describing integration of Squid with Active Directory rely on creating special computer account in AD for the same goal. Unfortunately it ties the proxy machine to Active Directory and prevents us from making and restoring VM snapshots because the restored snapshot loses the AD join state and needs to be rejoined manually.
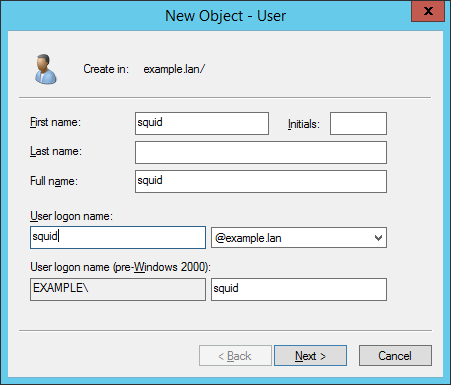
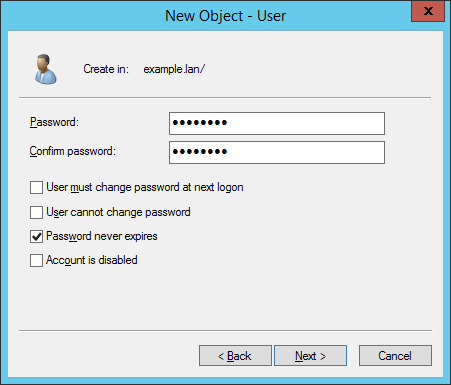
To create such a user mapping, open your Domain Users and Computers management console on dc1.example.lan and create a new user squid@example.lan with password Passw0rd that never expires (you can use any password you like of course).
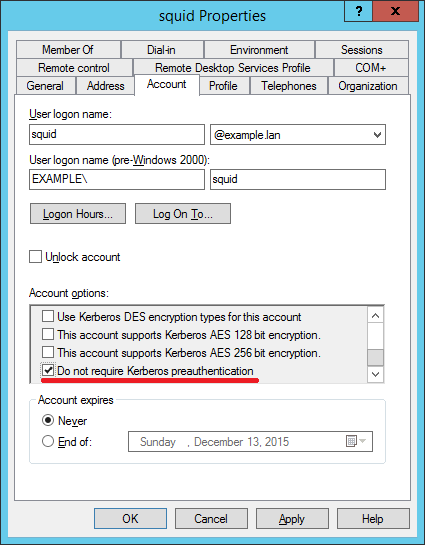
Open users Properties/Account tab and set the “Do not require Kerberos preauthentication” checkbox.
We will now use this user on next steps Step 4. Link to Active Directory domain and Step 5. Configure Kerberos authentication on Squid.