Authentication Backends¶
Once the user provides his credentials to Captive Portal these credentials need to be verified by actual authentication backend. Currently the following verification methods can be used.
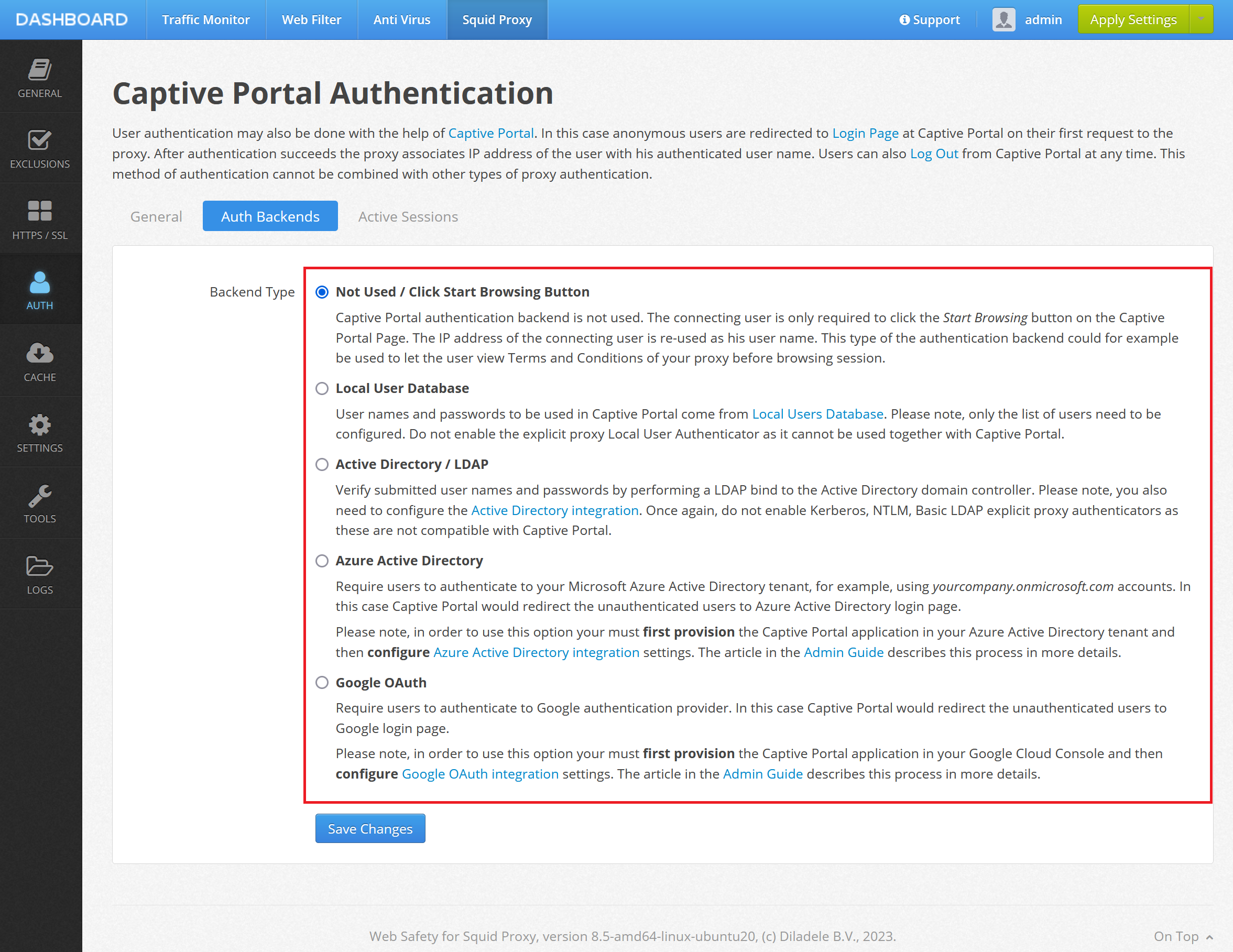
Not Used / Click Start Browsing Button
Captive Portal authentication backend is not used. The connecting user is only required to click the Start Browsing button on the Captive Portal Page. The IP address of the connecting user is re-used as his user name.
This type of the authentication backend could for example be used to let the user view Terms and Conditions of your proxy before browsing session. To customize the page the user sees at the time of authentication, edit the
/opt/websafety-ui/var/console/portal/templates/portal/accept.htmlpage.
Local User Database
User names and passwords to be used in Captive Portal come from Local Users Database. Please note, only the list of users need to be configured. Do not enable the explicit proxy Local User Authenticator as it cannot be used together with Captive Portal.
To customize the page the user sees at the time of authentication, edit the
/opt/websafety-ui/var/console/portal/templates/portal/local_users.htmlpage.
Active Directory / LDAP
Verify submitted user names and passwords by performing a LDAP bind to the Active Directory domain controller. Please note, you also need to configure the Active Directory integration. Once again, do not enable Kerberos, NTLM, Basic LDAP explicit proxy authenticators as these are not compatible with Captive Portal.
To customize the page the user sees at the time of authentication, edit the
/opt/websafety-ui/var/console/portal/templates/portal/active_directory.htmlpage.
Azure Active Directory
Require users to authenticate to your Microsoft Azure Active Directory tenant, for example, using yourcompany.onmicrosoft.com accounts. In this case Captive Portal would redirect the unauthenticated users to Azure Active Directory login page.
Please note, in order to use this option your must first provision the Captive Portal application in your Azure Active Directory tenant and then configure Azure Active Directory integration settings. For more information and detailed guidance, see tutorial at Azure Active Directory Authentication on Squid.
To customize the page the user sees at the time of authentication, edit the
/opt/websafety-ui/var/console/portal/templates/portal/azure_ad.htmlpage.
Google OAuth
Require users to authenticate to your Google Workspace (G Suite) deployment. In this case Captive Portal would redirect the unauthenticated users to Google Authentication login page.
Please note, in order to use this option your must first provision the Captive Portal application in your Google Workspace and then configure integration settings. For more information and detailed guidance, see tutorial at Google OAuth Authentication on Squid.
To customize the page the user sees at the time of authentication, edit the
/opt/websafety-ui/var/console/portal/templates/portal/google_oauth.htmlpage.
After successful login the user is presented with confirmation page with session information (IP address and user name) and ability to continue browsing or perform the log off.
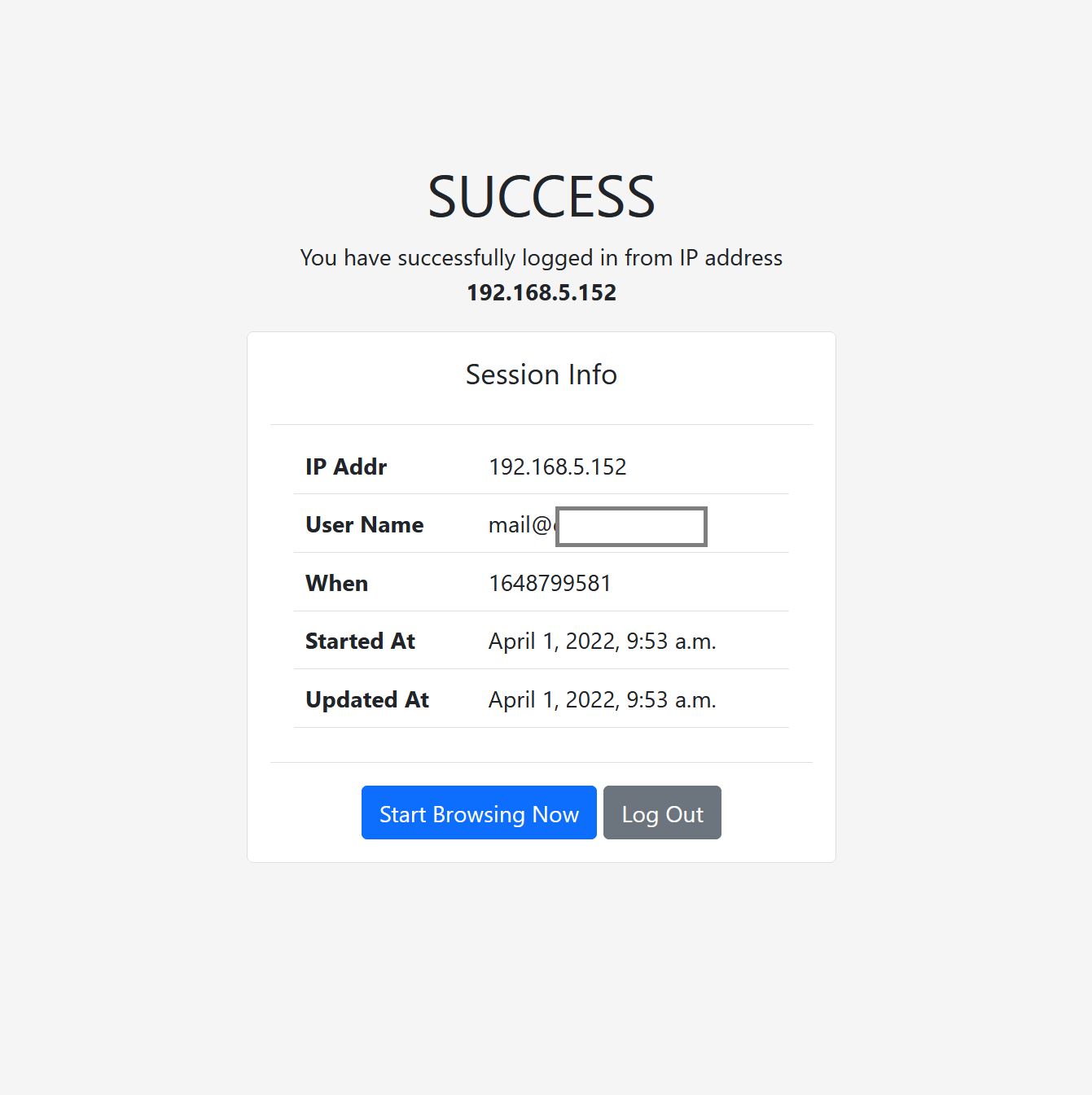
To let the user logout manually at any time, from the user machine, navigate to https://your_proxy_name_or_ip/portal/logout/ and click the Log Out button. The administrator can also manually delete the user session as shown on the following article.