What is a Filtering Policy¶
Policies are used to organize proxy users into groups (based on their User Name, IP Address, Range or Subnet and LDAP or ActiveDirectory Security Groups) and apply common filtering settings to them. Such pair of members and rules applied to them constitutes a Filtering Policy.
As an example consider having two groups of proxy users - students and teachers. Teachers would like to block web site ads and students should not be able to get access to adult web sites. To solve the problem we create two policies - Strict and Relaxed, adjust blocking rules as needed and then assign teachers to “Relaxed” policy and students to the “Strict” one.
After installation Web Safety has four predefined policies. To access them, select UI / Web Safety / Policies as indicated on the following screenshot.
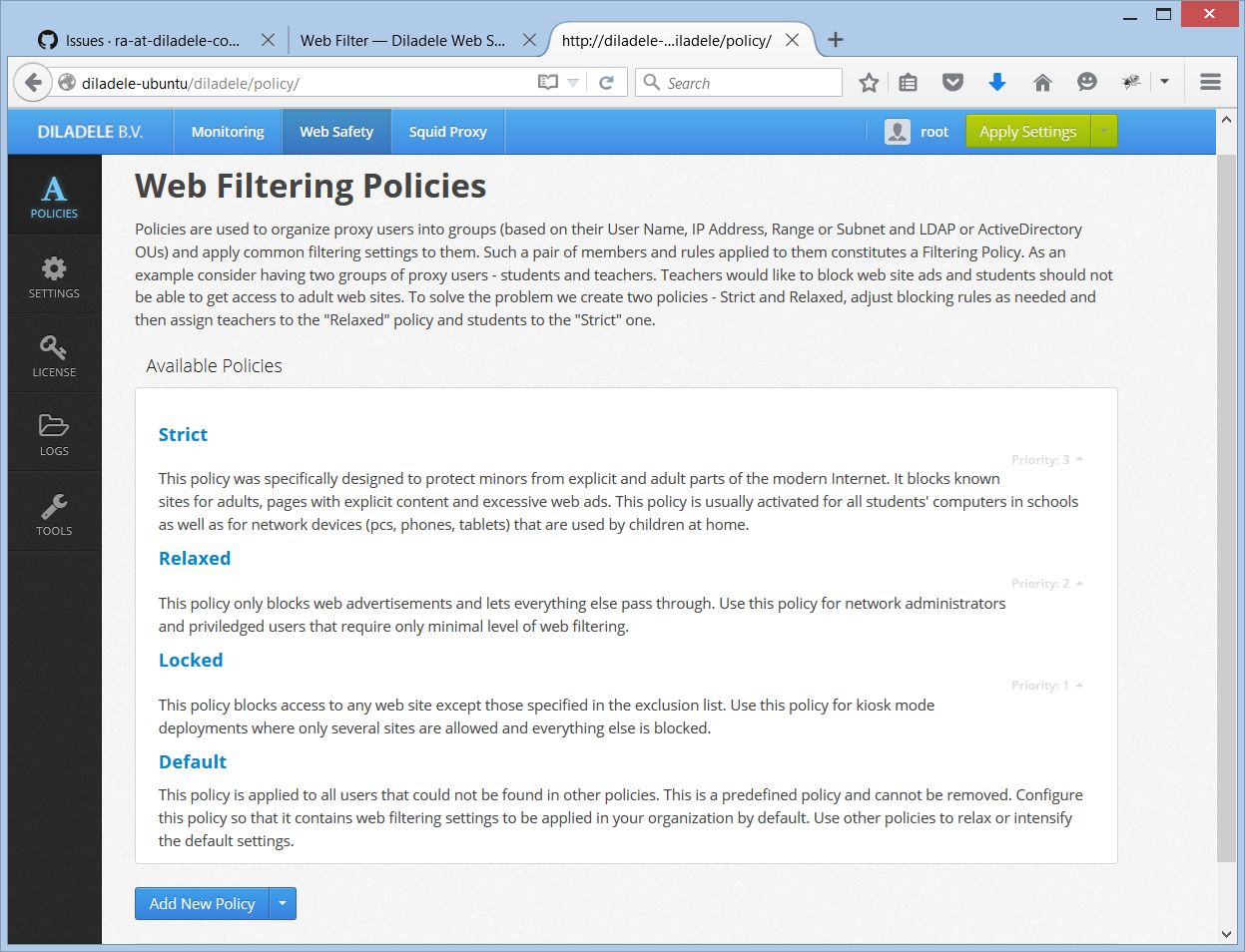
Strict - this policy was specifically designed to protect minors from explicit and adult parts of the modern internet. It blocks known sites for adults, pages with explicit contents and excessive web ads. This policy is usually activated for all students computers in schools as well as for networks devices (pcs, phones, tablets) that are used by children at home.
Relaxed - this is a relaxed policy. It only blocks web advertisements and lets everything else pass through. Use this policy for network administrators and priviledged users which require only minimal level of web filtering.
Locked - this is a locked policy. It blocks access to any web site except those specified in the exclusion list. Use this policy for kiosk mode deployments where only several sites are allowed and everything else is blocked.
Default Policy - this policy is applied to all users that could not be found in other policies. This is a predefined policy and cannot be removed. Configure this policy so that it contains web filtering settings to be applied in your organization by default. Use other policies to relax or intensify the default settings. Default is a predefined policy and cannot be removed.
Order of Policies¶
Squid proxy supplies the IP address and authenticated user name of the connected browser to the ICAP server. Having this information the ICAP server iterates over all available policies and tries to see if the user/IP can be found among policy members. If yes then this policy is selected. If no search continues until default policy is reached.
Various members of a policy is checked in the following order - user name / IP address / IP address range / IP subnet and finally Active Directory group.