Way 3 - TCP Balanced Round Robin with HAPROXY and PROXY (Recommended)¶
Important
This is the recommended mode of clustering for Web Safety. We use this mode in our test lab and regularly add/remove nodes to web filtering cluster without any client reconfiguration. Cluster configuration sync and shared traffic reporting are also working nicely in this mode.
In this case we will deploy a haproxy node in front of many proxy nodes. Browsers will connect to haproxy node that will distribute TCP connections to proxy nodes using round robin scheme.
This deployment is different from previously described Way 2 because haproxy and Squid instances will be connected using PROXY protocol. This protocol is used to notify Squid of real IP addresses of haproxy clients (browsers). It allows for full policy members matching by Active Directory name and IP address, ranges and subnets, removing limitations described at Way 2 article.
Create new type A record for proxy.example.lan with IP address 192.168.178.10. This will be the haproxy frontend to our cluster.
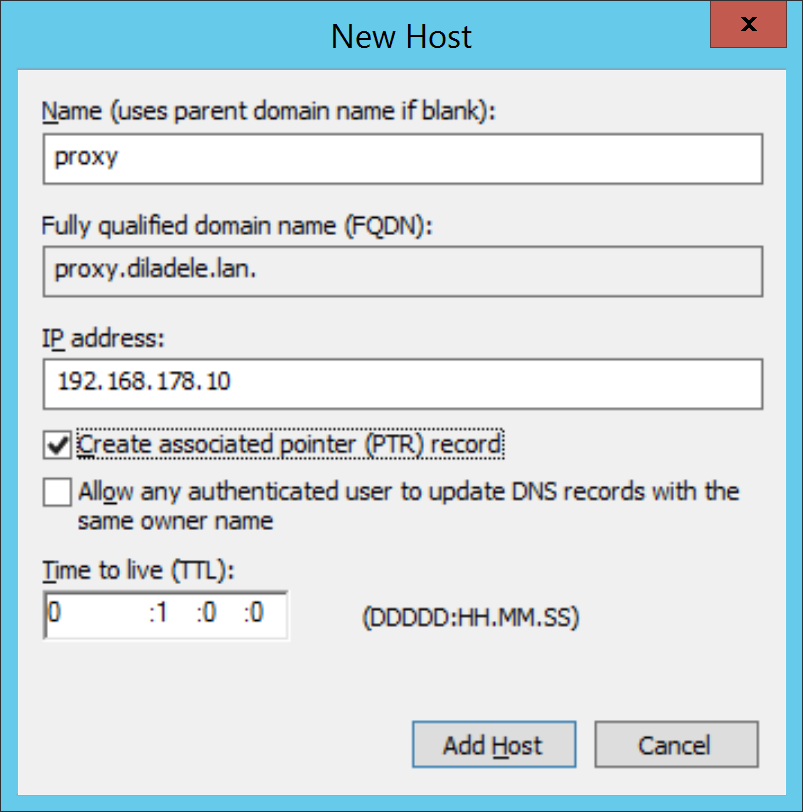
Create new type A record for node11.example.lan with IP address 192.168.178.11.
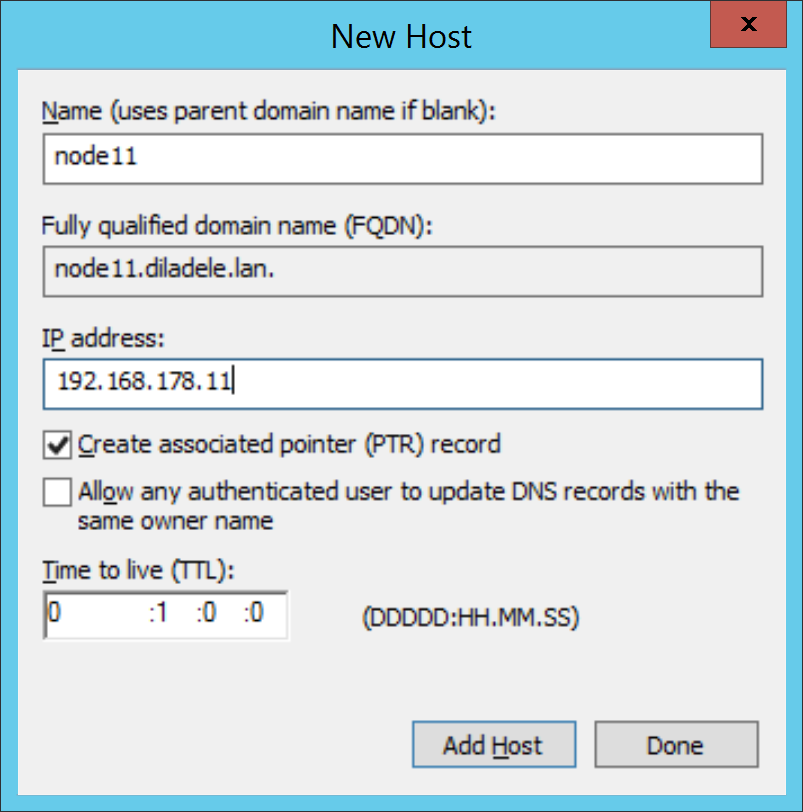
Create new type A record for node12.example.lan with IP address 192.168.178.12.
Configure haproxy on proxy.example.lan with the following configuration /etc/haproxy/haproxy.cfg. Note how each
serveris marked withsend-proxydirective.global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy stats socket /run/haproxy/admin.sock mode 660 level admin stats timeout 30s user haproxy group haproxy daemon defaults log global mode tcp option tcplog option dontlognull timeout connect 5000 timeout client 50000 timeout server 50000 frontend squid bind 192.168.178.10:3128 default_backend squid_pool backend squid_pool balance roundrobin mode tcp server squid1 192.168.178.11:3128 check send-proxy server squid2 192.168.178.12:3128 check send-proxyDeploy two virtual appliances of Web Safety and assign IP address of 192.168.178.11 for the first node and 192.168.178.12 for the second node. For the instructions on how to assign static IP for a virtual appliance see article How to Set Static IP Address in VA.
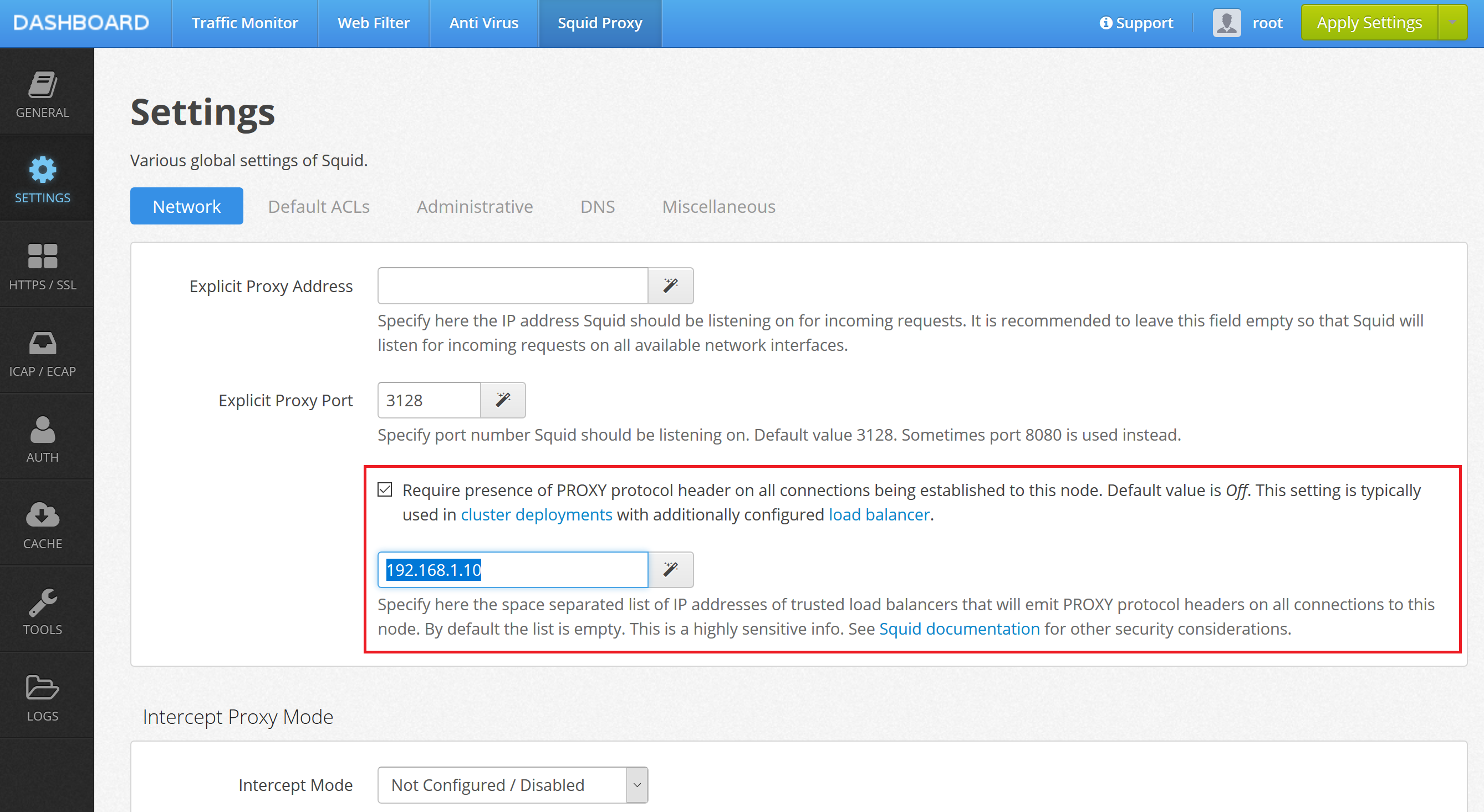
Enable support for PROXY protocol in UI / Squid / Settings / Netwrork by setting the Require presence of PROXY protocol header checkbox and providing haproxy’s IP address in address field as indicated on the following screenshot. Click Save and Restart.
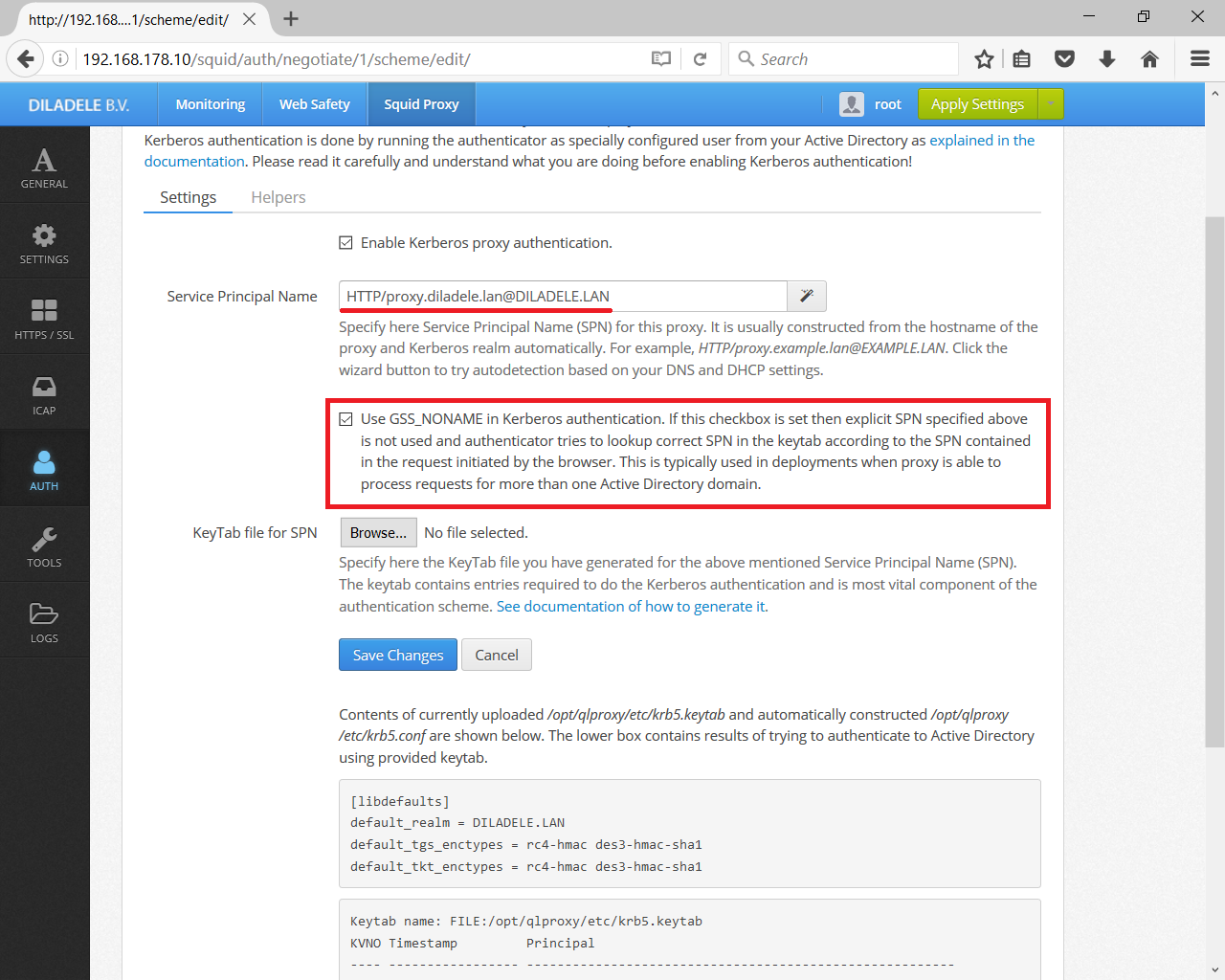
If Active Directory integration is required, follow the usual Active Directory configuration steps described in previous articles for each virtual appliance, but when configuring Kerberos authenticator provide the SPN based on proxy.example.lan and check the Use GSS_C_NO_NAME checkbox. This will let the node process requests for Kerberos authentication from browsers based on credentials contained in the request and not based on SPN (SPN still needs to be configured though).
Restart haproxy afterwards systemctl restart haproxy. Log in /var/log/haproxy.log should indicate both proxy nodes are working.